Cybersecurity scientists have unearthed new samples of malware called RapperBot that are being applied to develop a botnet capable of launching Dispersed Denial of Service (DDoS) attacks versus activity servers.
“In simple fact, it turns out that this marketing campaign is less like RapperBot than an more mature campaign that appeared in February and then mysteriously disappeared in the middle of April,” Fortinet FortiGuard Labs scientists Joie Salvio and Roy Tay explained in a Tuesday report.
RapperBot, which was 1st documented by the network security agency in August 2022, is recognized to solely brute-pressure SSH servers configured to take password authentication.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The nascent malware is closely inspired by the Mirai botnet, whose source code leaked in Oct 2016, foremost to the rise of several variants.
What’s noteworthy about the up-to-date model of RapperBot is its ability to conduct Telnet brute-pressure, in addition to supporting DoS attacks working with the Generic Routing Encapsulation (GRE) tunneling protocol.
“The Telnet brute-forcing code is made largely for self-propagation and resembles the old Mirai Satori botnet,” the scientists reported.
This listing of really hard-coded plaintext qualifications, which are default credentials linked with IoT products, are embedded into the binary as opposed to retrieving it from a command-and-command (C2) server, a actions that was observed in artifacts detected just after July 2022.
A thriving break-in is followed by reporting the qualifications employed back again to the C2 server and installing the RapperBot payload on the hacked unit.

Fortinet mentioned the malware is intended to only goal appliances that operate on ARM, MIPS, PowerPC, SH4, and SPARC architectures, and halt its self-propagation mechanism should really they be functioning on Intel chipsets.
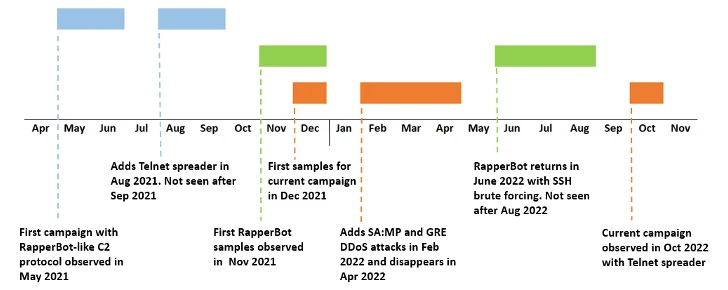
What is more, the October 2022 marketing campaign has been located to share overlaps with other operations involving the malware as considerably again as May possibly 2021, with the Telnet spreader module generating its initially look in August 2021, only to be eradicated in afterwards samples and reintroduced last thirty day period.
“Primarily based on the simple similarities amongst this new marketing campaign and the earlier reported RapperBot campaign, it is extremely most likely that they are becoming operated by a one threat actor or by various threat actors with accessibility to a privately-shared base resource code,” the researchers concluded.
Located this post appealing? Follow THN on Fb, Twitter and LinkedIn to study much more exceptional information we post.
Some pieces of this write-up are sourced from:
thehackernews.com


 Google to Roll Out Privacy Sandbox Beta on Android 13 by Early 2023
Google to Roll Out Privacy Sandbox Beta on Android 13 by Early 2023