Two new security vulnerabilities have been disclosed in Rockwell Automation’s programmable logic controllers (PLCs) and engineering workstation program that could be exploited by an attacker to inject destructive code on impacted devices and stealthily modify automation procedures.
The flaws have the potential to disrupt industrial functions and bring about physical harm to factories in a way equivalent to that of Stuxnet and the Rogue7 attacks, operational technology security company Claroty mentioned.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
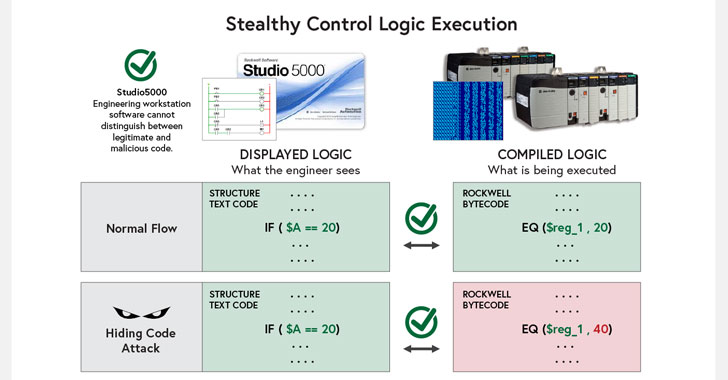
“Programmable logic and predefined variables travel these [automation] processes, and changes to possibly will change typical procedure of the PLC and the approach it manages,” Claroty’s Sharon Brizinov pointed out in a produce-up published Thursday.
The record of two flaws is beneath –
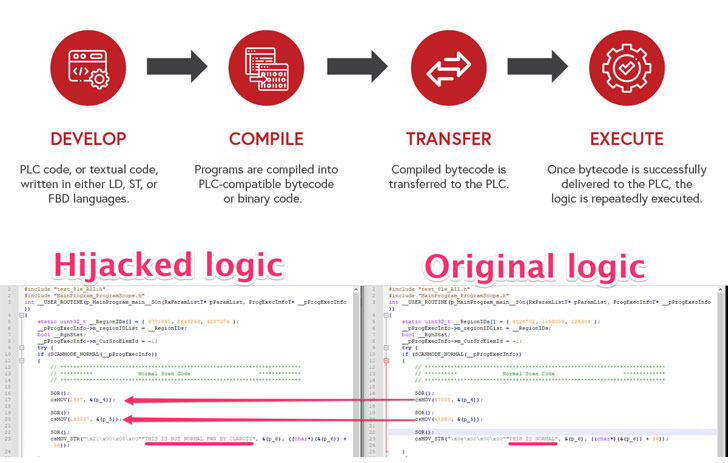
- CVE-2022-1161 (CVSS rating: 10.) – A remotely exploitable flaw that makes it possible for a destructive actor to compose user-readable “textual” method code to a separate memory area from the executed compiled code (aka bytecode). The issue resides in PLC firmware jogging on Rockwell’s ControlLogix, CompactLogix, and GuardLogix regulate devices.
- CVE-2022-1159 (CVSS rating: 7.7) – An attacker with administrative obtain to a workstation operating Studio 5000 Logix Designer application can intercept the compilation procedure and inject code into the person program without having the user’s know-how.
Prosperous exploitation of the problems could allow for an attacker to modify person courses and download malicious code to the controller, proficiently altering the PLC’s ordinary operation and permitting rogue commands to be sent to the actual physical gadgets controlled by the industrial program.
“The conclusion final result of exploiting both of those vulnerabilities is the very same: The engineer thinks that benign code is managing on the PLC meanwhile, totally unique and likely malicious code is becoming executed on the PLC,” Brizinov defined.
The severity of the flaws has also prompted an advisory from the U.S. Cybersecurity and Infrastructure Security Company (CISA) that outlines mitigation measures consumers of the afflicted hardware and software can consider for a “detailed protection-in-depth approach.”
Discovered this posting intriguing? Stick to THN on Fb, Twitter and LinkedIn to read through more unique material we publish.
Some sections of this post are sourced from:
thehackernews.com


 Auvik Network Management review: A breeze to deploy
Auvik Network Management review: A breeze to deploy