There are lots of cloud-hosted network-monitoring selections to opt for from, but Auvik can assert to be one of the swiftest to deploy. Two variations are offered: the Necessities version delivers network mapping, monitoring, alerting and product configuration management, although the Effectiveness version adds capabilities this sort of as Syslog collection and flow data analysis for thorough application visibility.
To use it you just want to install a collector agent in just about every internet site – and this is painless as it’s a light-weight services that will run on any version of Windows. The back again-finish, meanwhile, is hosted in AWS data centres, and safeguarded by equally solitary indicator-on and 2FA treatments. All collector knowledge is encrypted, and outbound communications are only permitted with its cloud servers.
Onboarding is a piece of cake. Right after building our cloud account we employed Microsoft’s Authenticator application to confirm secure administrative access, made our initial web site and downloaded the agent installer. Right after managing this on a Windows Server 2019 host, we ended up prompted to offer a unique API crucial, and then a safe relationship to our cloud account was designed.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Auvik kicks off its discovery approach immediately, and whilst it’s scanning you can enter credentials for SNMP, WMI, SSH, telnet, and VMware. We were being amazed to see that it took only all over 16 minutes to create a entirely populated network map for a finish subnet.
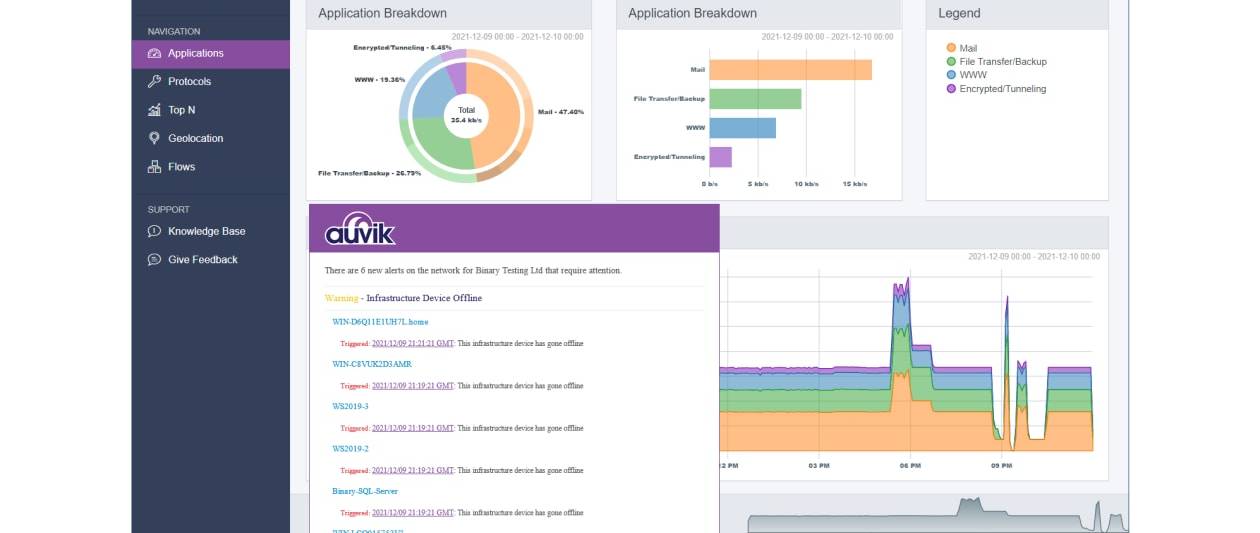
From now on the network is constantly scanned – you can established an interval in seconds – though the map exhibits your network structure. Colored url lines between devices distinguish between Layer 1, Layer 3, and VPN connections, although dotted lines denote wireless one-way links. We uncovered the map rapidly current itself to replicate network or gadget condition modifications, and every single unit icon is active, so you can hover more than a node to see a pop-up standing window, or click on to load its facts in the panel underneath.
The house dashboard panel delivers a helpful action overview with tables of the busiest units, open alerts, SSL VPN status and the affliction of VMware host hardware factors. The computer software offered total visibility into our Hyper-V host, demonstrating details this kind of as CPU, memory, storage and virtual change utilisation, targeted traffic throughput, and specific VM position.
To help you continue to keep on best of any emergent issues, Auvik offers 58 preconfigured alerts, ranging from a down device or services to significant storage use, as effectively as the alternative to set your own. Notifications can be despatched by email or through numerous messaging platforms, like Teams, Slack, and FreshDesk.
While Auvik’s main focus is plainly on network, service, and product availability, it can also keep critical infrastructure equipment risk-free with automated configuration backups, restores and comparisons. The Overall performance edition provides a TrafficInsights dashboard where by NetFlow, sFlow, and J-Circulation info is ingested, analysed, and introduced as informative graphs.
Auvik’s per-machine licensing initially appears to be like pricey, but it’s not really hard to customise the configuration so that only your crucial devices are monitored, and you help you save by not owning to supply a dedicated on-premises host. Considering that it’s so functional, so easy to deploy, and so straightforward to regulate, it is a great option for SMBs that want a clear picture of their network.
Some sections of this write-up are sourced from:
www.itpro.co.uk

 IT Pro News In Review: Kaspersky national security threat, UK tech worth $1trillion, LAPSUS$ expands its attacks
IT Pro News In Review: Kaspersky national security threat, UK tech worth $1trillion, LAPSUS$ expands its attacks