With Microsoft using steps to block Excel 4. (XLM or XL4) and Visible Primary for Applications (VBA) macros by default across Office apps, malicious actors are responding by refining their new methods, tactics, and methods (TTPs).
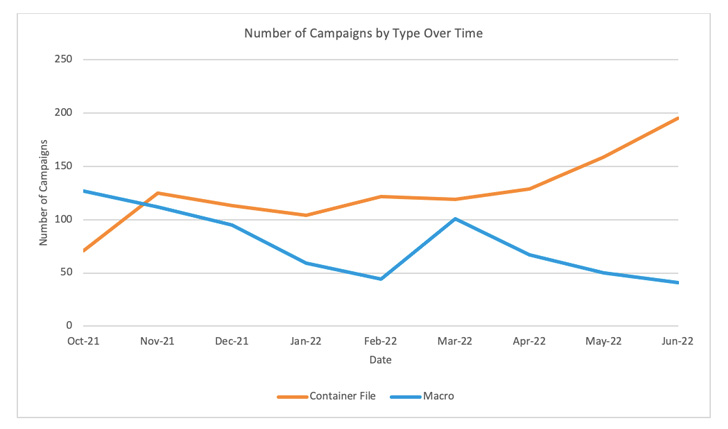
“The use of VBA and XL4 Macros reduced somewhere around 66% from October 2021 by means of June 2022,” Proofpoint mentioned in a report shared with The Hacker Information.
In its spot, adversaries are ever more pivoting away from macro-enabled documents to other alternate options, such as container documents these as ISO and RAR as well as Windows Shortcut (LNK) data files in campaigns to distribute malware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

VBA macros embedded in Workplace paperwork sent via phishing emails have proven to be an efficient technique in that it enables threat actors to routinely run destructive written content following tricking a recipient into enabling macros by way of social engineering tactics.
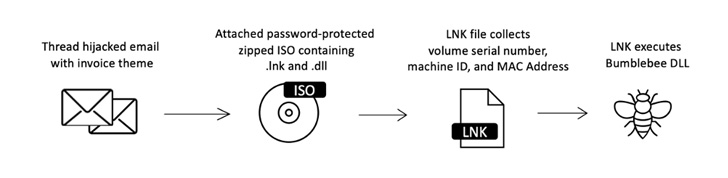
On the other hand, Microsoft’s plans to block macros in information downloaded from the internet have led to email-based mostly malware campaigns experimenting with other strategies to bypass Mark of the Web (MOTW) protections and infect victims.
This involves the use of ISO, RAR and LNK file attachments, which have surged practically 175% through the very same interval. At least 10 menace actors are reported to have begun utilizing LNK data files because February 2022.
“The amount of campaigns made up of LNK documents amplified 1,675% because Oct 2021,” the organization security enterprise noted, including the number of attacks working with HTML attachments much more than doubled from Oct 2021 to June 2022.

Some of the noteworthy malware families distributed through these new solutions consist of Emotet, IcedID, Qakbot, and Bumblebee.
“Threat actors pivoting away from immediately distributing macro-dependent attachments in email signifies a significant shift in the danger landscape,” Sherrod DeGrippo, vice president of danger study and detection at Proofpoint, stated in a assertion.
“Threat actors are now adopting new strategies to supply malware, and the amplified use of data files these types of as ISO, LNK, and RAR is expected to continue.”
Located this posting fascinating? Comply with THN on Facebook, Twitter and LinkedIn to study more exceptional articles we post.
Some sections of this report are sourced from:
thehackernews.com


 NCSC launches startup incubator to protect against national cyber threats
NCSC launches startup incubator to protect against national cyber threats