Danger actors are actively incorporating community cloud products and services from Amazon and Microsoft into their destructive campaigns to deliver commodity remote obtain trojans (RATs) this kind of as Nanocore, Netwire, and AsyncRAT to siphon sensitive data from compromised techniques.
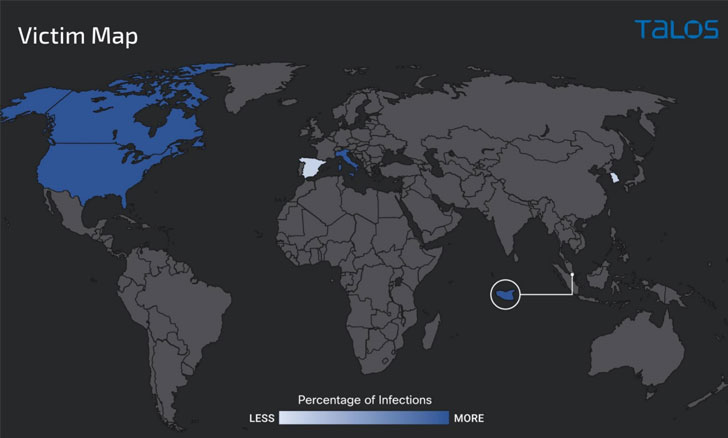
The spear-phishing attacks, which commenced in October 2021, have generally targeted entities situated in the U.S., Canada, Italy, and Singapore, researchers from Cisco Talos said in a report shared with The Hacker Information.
Utilizing current infrastructure to aid intrusions is significantly turning out to be portion of an attacker’s playbook as it obviates the will need to host their have servers, not to point out employing it as a cloaking mechanism to evade detection by security alternatives.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

In current months, collaboration and conversation equipment like Discord, Slack, and Telegram have found a place in quite a few an infection chain to commandeer and exfiltrate data from the victim devices. Seen in that mild, the abuse of cloud platforms is a tactical extension that attackers could exploit as a initially stage into a broad array of networks.
“There are many fascinating elements to this specific campaign, and it points to some of the factors we usually see utilized and abused by malicious actors,” Nick Biasini, head of outreach at Cisco Talos, explained to The Hacker Information by way of email.
“From the use of cloud infrastructure to host malware to the abuse of dynamic DNS for command-and-regulate (C2) actions. Moreover, the layers of obfuscation issue to the present-day state of legal cyber functions, wherever it can take tons of evaluation to get down to the last payload and intentions of the attack.”
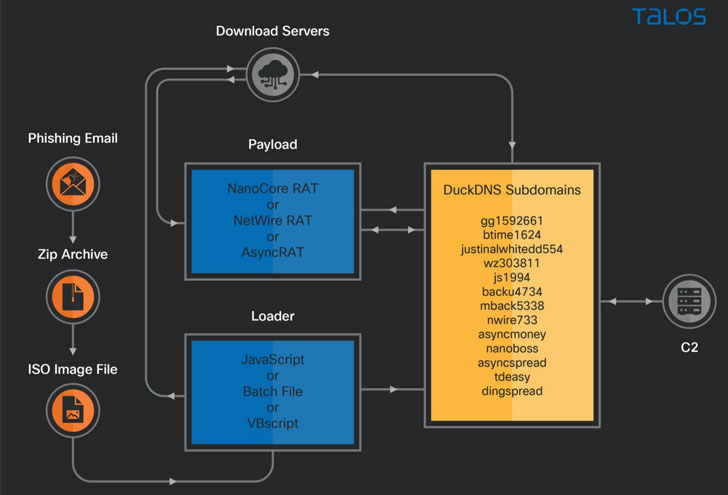
As with many of these varieties of strategies, it all begins with an invoice-themed phishing email containing a ZIP file attachment that, when opened, triggers an attack sequence that downloads future-stage payloads hosted on an Azure Cloud-centered Windows server or an AWS EC2 occasion, in the end culminating in the deployment of distinct RATs, which include AsyncRAT, Nanocore, and Netwire.
Also noteworthy is the use of DuckDNS, a totally free dynamic DNS services, to create destructive subdomains to provide malware, with some of the actor-managed destructive subdomains resolving to the download server on Azure Cloud when other servers are operated as C2 for the RAT payloads.
“Destructive actors are opportunistic and will constantly be on the lookout for new and ingenious approaches to equally host malware and infect victims,” Biasini said. “The abuse of platforms these as Slack and Discord as effectively as the connected cloud abuse are section of this pattern. We also frequently find compromised web sites being utilized to host malware and other infrastructure as effectively and yet again details to the point that these adversaries will use any and all suggests to compromise victims.”
Identified this report fascinating? Stick to THN on Facebook, Twitter and LinkedIn to examine more unique content we article.
Some components of this report are sourced from:
thehackernews.com


 US gov issues fresh warning over Russian threat to critical infrastructure
US gov issues fresh warning over Russian threat to critical infrastructure