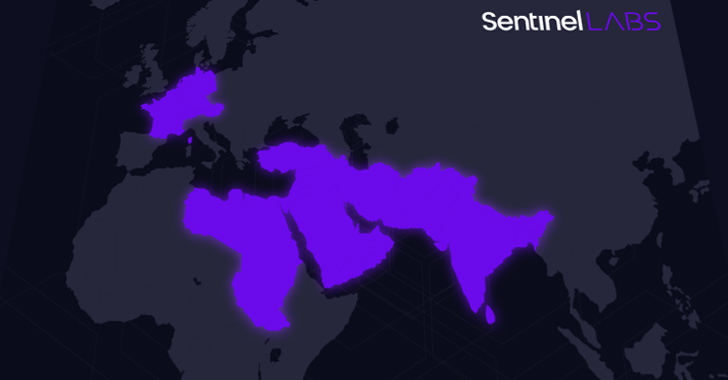
A previously undocumented menace actor dubbed Sandman has been attributed to a set of cyber attacks concentrating on telecommunic koation providers in the Center East, Western Europe, and the South Asian subcontinent.
Notably, the intrusions leverage a just-in-time (JIT) compiler for the Lua programming language recognized as LuaJIT as a automobile to deploy a novel implant termed LuaDream.
“The actions we observed are characterized by strategic lateral motion to distinct specific workstations and minimal engagement, suggesting a deliberate method aimed at accomplishing the established objectives even though reducing the risk of detection,” SentinelOne security researcher Aleksandar Milenkoski explained in an analysis posted in collaboration with QGroup.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The implementation of LuaDream suggests a effectively-executed, managed, and actively created undertaking of a significant scale.”
Neither the marketing campaign nor its techniques have been correlated with any recognised threat actor or group, although offered proof details to a cyber espionage adversary with a penchant for concentrating on the telecom sector throughout geographies. The attacks were initially noticed more than various weeks in August 2023.
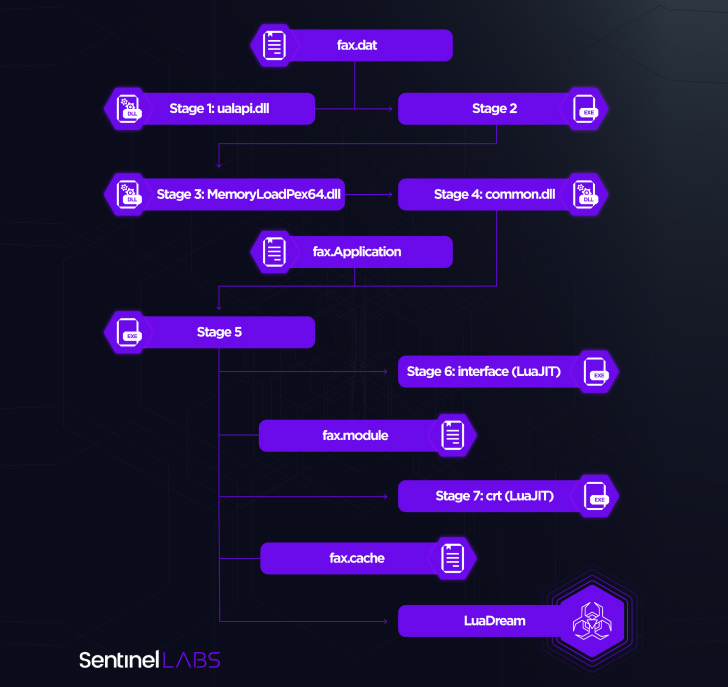
“The LuaDream staging chain is developed to evade detection and thwart analysis whilst deploying the malware specifically into memory,” Milenkoski spelled out. “LuaDream’s implementation and staging approach leverage the LuaJIT platform, the just-in-time compiler for the Lua scripting language. This is primarily to make malicious Lua script code challenging to detect.”

String artifacts contained within the implant’s resource code reference June 3, 2022, indicating that the preparatory function has been underway for much more than a calendar year.
It is suspected that LuaDream is a variant of a new malware strain referred to as DreamLand by Kaspersky in its APT tendencies report for Q1 2023, with the Russian cybersecurity company describing it as using “the Lua scripting language in conjunction with its Just-in-Time (JIT) compiler to execute malicious code that is difficult to detect.”
The use of Lua is anything of a rarity in the menace landscape, owning been formerly observed in a few diverse instances considering that 2012: Flame, Animal Farm (aka SNOWGLOBE), and Task Sauron.
The specific method of preliminary entry stays unclear, but it has been observed thieving administrative credentials and conducting reconnaissance to breach workstations of curiosity and in the end produce LuaDream.
A modular, multi-protocol backdoor with 13 main and 21 guidance components, LuaDream is mainly developed to exfiltrate procedure and person info as properly as take care of attacker-offered plugins that extend on its attributes, this kind of as command execution. It also options a variety of anti-debugging abilities to evade detection and thwart assessment.
Command-and-regulate (C2) communication is achieved by developing get in touch with with a domain named “method.encagil[.]com” employing the WebSocket protocol. But it can also pay attention for incoming connections in excess of TCP, HTTPS, and QUIC protocols.
The core modules put into action all of the aforementioned options, while the aid factors are liable for augmenting the backdoor’s abilities to await connections primarily based on the Windows HTTP server API and execute instructions.
“LuaDream stands as a compelling illustration of the steady innovation and progression endeavours that cyber espionage threat actors pour into their at any time-evolving malware arsenal,” Milenkoski stated.
The disclosure coincides with a parallel report from SentinelOne which thorough sustained strategic intrusions by Chinese risk actors in Africa, such as those aimed at telecommunication, finance and authorities sectors in Africa, as part of action clusters dubbed BackdoorDiplomacy, Earth Estries, and Operation Tainted Love.
Forthcoming WEBINARLevel-Up SaaS Security: A Complete Guidebook to ITDR and SSPM
Keep ahead with actionable insights on how ITDR identifies and mitigates threats. Find out about the indispensable role of SSPM in making certain your identification remains unbreachable.
Supercharge Your Skills
The intention, the enterprise reported, is to increase affect through the continent and leverage these offensives as element of its comfortable ability agenda.
SentinelOne claimed it detected a compromise of a telecommunications entity dependent in North Africa by the exact risk actor behind Procedure Tainted Love, adding the timing of the attack aligned with the organization’s personal negotiations for even more regional enlargement.
“Qualified intrusions by the BackdoorDiplomacy APT and the menace group orchestrating Procedure Tainted Love suggest a stage intention directed at supporting [China in its efforts to] form guidelines and narratives aligned with its geostrategic ambitions, developing alone as a pivotal and defining force in Africa’s electronic evolution,” security researcher Tom Hegel claimed.
It also will come days soon after Cisco Talos discovered that telecommunication assistance companies in the Center East are the concentrate on of a new intrusion established dubbed ShroudedSnooper that employs a established of stealthy backdoors termed HTTPSnoop and PipeSnoop.
Located this post intriguing? Comply with us on Twitter and LinkedIn to go through extra exclusive written content we post.
Some elements of this posting are sourced from:
thehackernews.com

 Researchers Raise Red Flag on P2PInfect Malware with 600x Activity Surge
Researchers Raise Red Flag on P2PInfect Malware with 600x Activity Surge