As many as 11 security vulnerabilities have been disclosed in Nagios network management systems, some of which could be chained to realize pre-authenticated remote code execution with the best privileges, as very well as lead to credential theft and phishing attacks.
Industrial cybersecurity agency Claroty, which uncovered the flaws, stated flaws in tools these kinds of as Nagios make them an eye-catching goal owing to their “oversight of main servers, products, and other critical factors in the company network.” The issues have because been preset in updates produced in August with Nagios XI 5.8.5 or over, Nagios XI Swap Wizard 2.5.7 or previously mentioned, Nagios XI Docker Wizard 1.13 or higher than, and Nagios XI WatchGuard 1.4.8 or above.
“SolarWinds and Kaseya have been very likely focused not only for the reason that of their large and influential customer bases, but also mainly because of their respective technologies’ accessibility to business networks, no matter if it was running IT, operational technology (OT), or internet of factors (IoT) equipment,” Claroty’s Noam Moshe mentioned in a produce-up printed Tuesday, noting how the intrusions concentrating on the IT and network management offer chains emerged as a conduit to compromise thousands of downstream victims.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Nagios Main is a popular open up-supply network wellbeing resource analogous to SolarWinds Network Effectiveness Observe (NPM) that’s used for retaining tabs on IT infrastructure for performance issues and sending alerts following the failure of mission-critical factors. Nagios XI, a proprietary web-based system created atop Nagios Main, offers corporations with prolonged perception into their IT operations with scalable checking and a customizable large-level overview of hosts, companies, and network products.
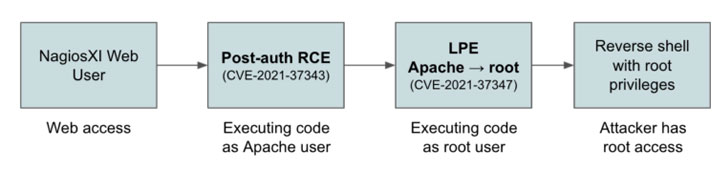
Chief amid the issues are two distant code execution flaws (CVE-2021-37344, CVE-2021-37346) in Nagios XI Switch Wizard and Nagios XI WatchGuard Wizard, an SQL injection vulnerability (CVE-2021-37350) in Nagios XI, and a server-side request forgery (SSRF) influencing Nagios XI Docker Wizard, as effectively as a write-up-authenticated RCE in Nagios XI’s Car-Discovery tool. The comprehensive checklist of 11 flaws is as follows –
- CVE-2021-37343 (CVSS score: 8.8) – A path traversal vulnerability exists in Nagios XI below version 5.8.5 AutoDiscovery ingredient and could guide to submit-authenticated RCE beneath the security context of the person working Nagios.
- CVE-2021-37344 (CVSS score: 9.8) – Nagios XI Change Wizard just before version 2.5.7 is susceptible to distant code execution by way of incorrect neutralization of special factors made use of in an OS Command (OS Command injection).
- CVE-2021-37345 (CVSS score: 7.8) – Nagios XI ahead of version 5.8.5 is vulnerable to community privilege escalation due to the fact xi-sys.cfg is getting imported from the var directory for some scripts with elevated permissions.
- CVE-2021-37346 (CVSS score: 9.8) – Nagios XI WatchGuard Wizard prior to version 1.4.8 is susceptible to remote code execution via Poor neutralization of distinctive things employed in an OS Command (OS Command injection).
- CVE-2021-37347 (CVSS score: 7.8) – Nagios XI ahead of model 5.8.5 is susceptible to local privilege escalation due to the fact getprofile.sh does not validate the listing name it gets as an argument.
- CVE-2021-37348 (CVSS score: 7.5) – Nagios XI prior to edition 5.8.5 is vulnerable to area file inclusion by an poor limitation of a pathname in index.php.
- CVE-2021-37349 (CVSS score: 7.8) – Nagios XI right before variation 5.8.5 is vulnerable to area privilege escalation for the reason that cleaner.php does not sanitize input browse from the database.
- CVE-2021-37350 (CVSS rating: 9.8) – Nagios XI right before variation 5.8.5 is susceptible to SQL injection vulnerability in Bulk Modifications Device owing to improper enter sanitization.
- CVE-2021-37351 (CVSS rating: 5.3) – Nagios XI prior to version 5.8.5 is susceptible to insecure permissions and permits unauthenticated users to accessibility guarded internet pages by means of a crafted HTTP ask for to the server.
- CVE-2021-37352 (CVSS rating: 6.1) – An open up redirect vulnerability exists in Nagios XI just before variation 5.8.5 that could direct to spoofing. To exploit the vulnerability, an attacker could ship a link that has a specifically-crafted URL and persuade the person to simply click the backlink.
- CVE-2021-37353 (CVSS rating: 9.8) – Nagios XI Docker Wizard in advance of variation 1.1.3 is vulnerable to SSRF due to inappropriate sanitization in table_inhabitants.php

In a nutshell, the flaws could be merged by attackers to fall a web shell or execute PHP scripts and elevate their privileges to root, therefore attaining arbitrary command execution in the context of the root user. As a evidence-of-idea, Claroty chained CVE-2021-37343 and CVE-2021-37347 to attain a generate-what-where by primitive, permitting an attacker to generate information to any file in the technique.
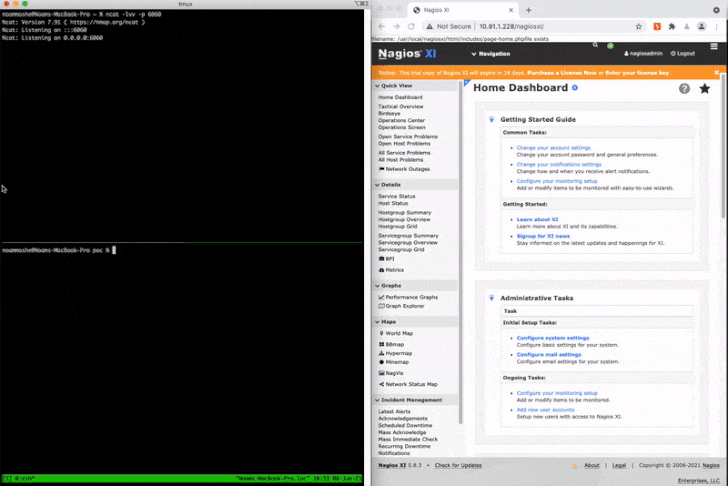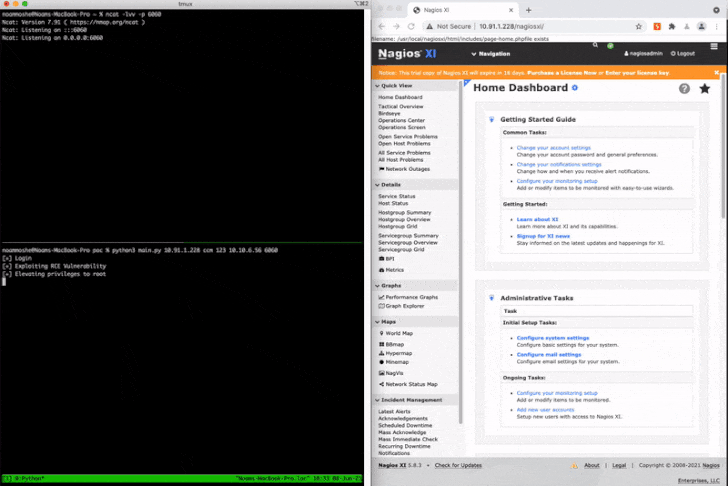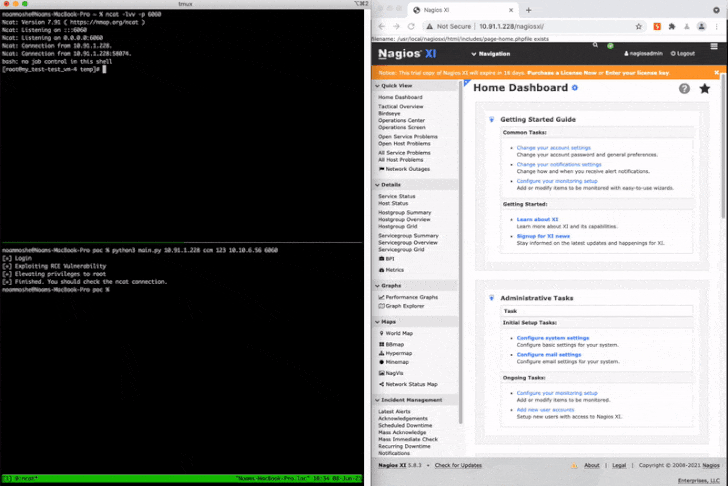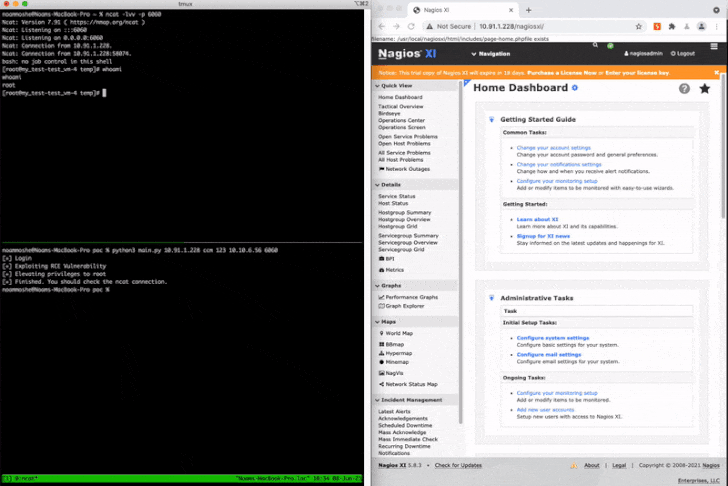
“[Network management systems] call for intensive believe in and access to network factors in buy to appropriately monitor network behaviors and efficiency for failures and weak efficiency,” Moshe mentioned.
“They may well also increase exterior your network as a result of the firewall to show up at to remote servers and connections. As a result, these centralized programs can be a tasty focus on for attackers who can leverage this variety of network hub, and endeavor to compromise it in order to accessibility, manipulate, and disrupt other units.”
The disclosure is the next time practically dozen vulnerabilities have been disclosed in Nagios. Previously this May perhaps, Skylight Cyber exposed 13 security weaknesses in the network checking application that could be abused by an adversary to hijack the infrastructure devoid of any operator intervention.
Located this report fascinating? Adhere to THN on Fb, Twitter and LinkedIn to read through a lot more exclusive content material we submit.
Some parts of this posting are sourced from:
thehackernews.com

 Enterprises Need 27 New IT Hires to Manage Security Debt
Enterprises Need 27 New IT Hires to Manage Security Debt