In an perfect environment, security and growth groups would be functioning jointly in fantastic harmony. But we stay in a globe of competing priorities, the place DevOps and security departments normally butt heads with each individual other.
Agility and security are usually at odds with each and every other— if a new element is shipped rapidly but consists of security vulnerabilities, the SecOps team will will need to scramble the release and patch the vulnerabilities, which can consider days or weeks. On the other hand, if the SecOps team takes as well long to evaluate and approve a new function, the advancement group will get pissed off with the sluggish rate of shipping.
Security demands to shift slowly but surely and cautiously, even though development wants to “shift rapid and crack points” and launch new features rapidly. DevOps teams can look at security as an impediment to their operate alternatively of an significant part of the approach. With each individual team pulling in opposite directions, there is usually stress and conflict concerning the two groups, slowing improvement and leaving companies open to security pitfalls.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It’s Time to Automate Security Tests
One particular way to resolve this conflict is to automate tests with each individual release. As a substitute of functioning a a single-time pen check when the web software is released, security teams ought to make sure vulnerabilities are not staying reintroduced with each individual new release and update in an technique regarded as “steady security.”
In constant security, the SecOps team is involved early and generally in the advancement approach. They function with developers to have an understanding of the challenges affiliated with new characteristics and assist them find ways to mitigate them. By remaining involved early on, the SecOps staff can assist to guarantee that new features are made with security in mind from the very beginning.
Pros of Constant Pen Screening
Penetration testing is a critical ingredient of web software security. As attack surfaces extend and programs become far more complex, regular pen tests develop into a vital part of a robust web software security posture.
However, pen tests is generally performed periodically, which success in a “security sprint” just about every time a new test is scheduled. When carried out late in the launch cycle, pen tests can be disruptive to the development procedure. Getting vulnerabilities only at specified flagpole factors in progress generally involves comprehensive and highly-priced rework for Dev and DevOps groups.
As aspect and parcel of shifting still left and improving the workflows amongst DevOps and Security teams, web application security tests wants to be developed into the advancement course of action. This way, vulnerabilities can be discovered and set right before the code is even deployed to output.
A constant testing tactic is an helpful way to integrate security testing into the advancement process so that companies can determine vulnerabilities without disrupting release cycles. Having said that, regardless of its strengths, frequent and ongoing pen screening can be complicated to employ. It is a resource-intensive approach and demands applications and abilities that might not be commonly available.
Pen-Tests-as-a-Services: Aligning DevOps and SecOps Priorities
One particular option is to partner with a service provider that specializes in constant pen testing and can enable carry out it in your firm. With Pen-Screening-as-a-Provider (PTaaS), you can get commenced with steady pen testing quickly and very easily without the need of investing in further methods or increasing your group.
PTaaS remedies develop a shared being familiar with of security issues and their affect. When development group members are presented the possibility to take a look at their code for vulnerabilities and fix them ahead of they attain manufacturing, they turn into more engaged in the security of the programs they are building. Some PTaaS remedies go one move further more by providing features that make it quick for builders to fix vulnerabilities, these types of as offering 1-click fixes for popular issues.
Outpost24’s Pen Testing as a Service (PTaaS) presents continuous pen tests for web apps in the course of a contract interval, typically a 12 months or lengthier. It consists of the applications and the expertise you have to have to put into action constant pen testing in your firm.
Outpost24’s PTaaS resolution provides many pros, which includes:
- Increased web software security: By integrating security testing into the advancement procedure, you can find and resolve vulnerabilities early on before they have a chance to lead to problems.
- Continual coverage: PTaaS offers constant protection of your programs so you can be confident that they are always secure, even soon after enhancement updates and vulnerability remediation.
- Expertise on desire: With PTaaS, you have obtain to the experience you want when you require it, such as 24/7 Portal communications.
- Enhanced performance: PTaaS can assist your SecOps conversation with DevOps many thanks to clear remediation measures and re-tests that allow for for continual enhancement through the pen tests period.
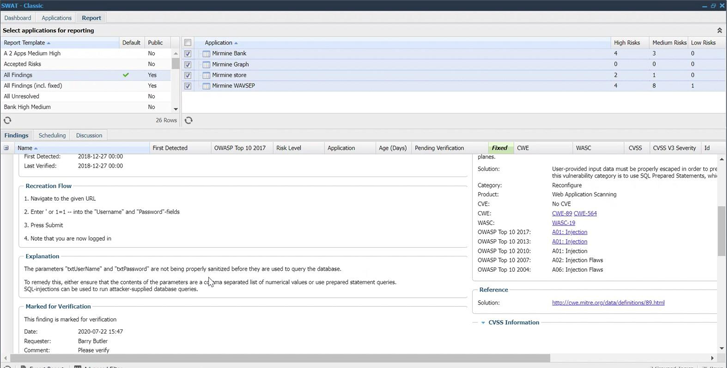 Here is an example of the remediation process for a person of the vulnerabilities identified by Outpost24’s continual pen testing.
Here is an example of the remediation process for a person of the vulnerabilities identified by Outpost24’s continual pen testing.
PTaaS is a cost-helpful answer that merges software progress and security processes into DevSecOps — a continual, automatic, and protected application enhancement lifecycle. By aligning the priorities of progress, security, and operations groups, PTaaS permits companies to supply secure program more quickly.
Discover extra about how Outpost24 can enable you apply ongoing penetration screening in your firm by getting in contact, here.
Found this report intriguing? Observe us on Twitter and LinkedIn to go through extra distinctive content material we post.
Some components of this posting are sourced from:
thehackernews.com


 Experts Warn of ‘Beep’ – A New Evasive Malware That Can Fly Under the Radar
Experts Warn of ‘Beep’ – A New Evasive Malware That Can Fly Under the Radar