Endpoint units like desktops, laptops, and cell telephones allow consumers to connect to company networks and use their assets for their working day-to-working day function. However, they also increase the attack surface and make the organisation vulnerable to malicious cyberattacks and information breaches.
Why Modern-day Organisations Have to have EDR
According to the 2020 world risk report by Ponemon Institute, smartphones, laptops, cellular units, and desktops are some of the most vulnerable entry points that allow risk actors to compromise enterprise networks. Security teams have to evaluate and handle the security hazards produced by these products right before they can destruction the organisation. And for this, they call for Endpoint Detection & Response (EDR).
EDR answers provide authentic-time visibility into endpoints and detect threats like malware and ransomware. By continuously checking endpoints, they enable security teams to uncover malicious routines, look into threats, and initiate ideal responses to protect the organisation.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The Limitations of EDR
Modern-day company networks are elaborate webs of people, endpoints, apps, and data flows dispersed across on-premises and multi-cloud environments. As EDR solutions only present visibility into endpoints, numerous security gaps and worries stay, appreciably expanding the risk of cyberattacks likely unnoticed.
- Malware disabling/abusing EDR brokers: The emergence of subtle hacker groups like Lapsus$ is a different risk that EDR instruments won’t be able to offer with. In late 2021, Lapsus$ hacked into various huge providers by compromising distant endpoints and turning off their EDR tools. They were thus equipped to hide their malicious conduct on the contaminated endpoints and attain their intention of stealing sensitive firm details. Another problem is that menace actors can abuse the “hooking” approach that EDRs use to keep an eye on functioning processes. This method permits EDR tools to monitor systems, detect suspicious pursuits, and get details for behaviour-dependent analytics. Nevertheless, this exact same approach lets attackers to accessibility a distant endpoint and import malware.
- BYOD: In current a long time, lots of organisations have shifted to remote do the job designs that permit workforce and third-party people to accessibility organization sources via remote networks and unsecured cell equipment. These devices are outside the command of security teams and their EDR instruments. Consequently, their security answers simply cannot continue to keep up with all these endpoints, considerably less shield them or the company network from destructive attacks.
- Unsupported devices: Also, not each individual linked endpoint can assist EDR brokers. This is accurate for legacy endpoints like routers and switches, as properly as more recent IoT units. More, with connected Supervisory Control and Info Acquisition (SCADA) and Industrial Command Process (ICS) environments, some endpoints may perhaps be outside the organisation’s command and hence exterior the EDR’s security perimeter. For that reason, these endpoints and units continue being vulnerable to threats like malware, DDoS attacks, and crypto mining.
- Protecting/deploying EDR: Eventually, with agent based mostly EDR items, it can be a huge stress for security teams to put in and maintain agents on every single endpoint throughout the enterprise network atmosphere.
Closing EDR’s Security Gaps with Network Visibility and NDR
A single of the most effective approaches to near the security gaps highlighted higher than is by adding Network Detection and Response (NDR) to the organization cybersecurity stack for the adhering to good reasons:
- Are not able to disable NDR: As a log information centered NDR these kinds of as ExeonTrace collects data from multiple different information resources in the network (and does not rely on unique gadgets), the detection algorithms are unable to be circumvented. Hence, even if an EDR is disabled by malware, the NDR will detect it.
- Identification of shadow IT: An NDR alternative not only will allow to check the network site visitors among recognised network units but also identifies and displays nevertheless unidentified devices and networks. And of study course, also endpoints without having EDR agents are involved in the network analytics (these types of as BYOD).
- Misconfigured firewalls and gateways: Unproper configured firewalls and gateways can be entry doors for attackers – an NDR makes it possible for for detection in advance of exploitation.
- Tamper-evidence facts collection: Network-based mostly details selection is a lot more tamper-evidence than agent-dependent details suitable for digital forensics essential by regulators.
- Comprehensive visibility of the total network: As no brokers are essential, an NDR remedy these as ExeonTrace makes it possible for for total visibility of all network connections and information flows. It therefore gives better visibility throughout the complete business network and any possible threats throughout it.
Summary
As organisations turn out to be significantly complex and increase more stop-user gadgets to their networks, they involve a responsible checking remedy to protect their endpoints from potential threats. Nonetheless, Endpoint Detection and Response (EDR) gives these kinds of endpoint protection only to a selected extent. There are various downsides of EDR that make it possible for advanced cybercriminals to surpass their security perimeter and exploit network vulnerabilities.
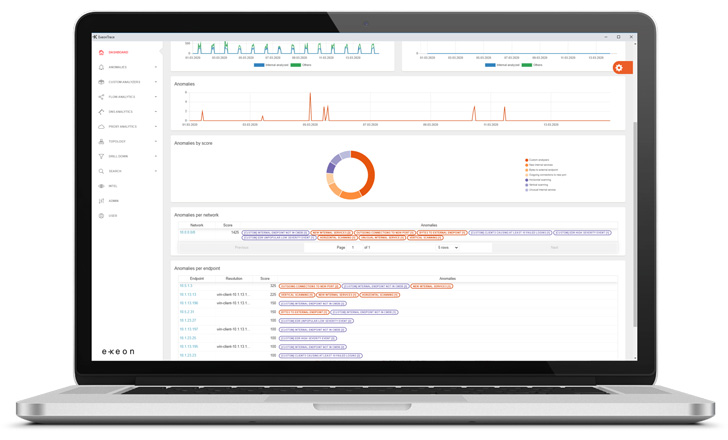 ExeonTrace System: Screenshot of Dashboard
ExeonTrace System: Screenshot of Dashboard
To fill the security gaps still left by EDR remedies, organisations ought to boost their security defences. Network Detection and Reaction (NDR) solutions like ExeonTrace are a responsible and established way to monitor network targeted traffic and thus complete business cybersecurity stacks. As EDR and NDR remedies are complementary, their mixed detection capabilities can effectively shield organisations from sophisticated cyberattacks.
E book a cost-free demo to uncover how ExeonTrace can assistance handle your security worries and make your organisation far more cyber resilient.
Located this post attention-grabbing? Abide by THN on Facebook, Twitter and LinkedIn to study a lot more special content we publish.
Some elements of this short article are sourced from:
thehackernews.com

 Manufacturers Failing to Address Cybersecurity Vulnerabilities Liable Under New European Rules
Manufacturers Failing to Address Cybersecurity Vulnerabilities Liable Under New European Rules