Researchers from the Bitdefender Cell Threats workforce claimed they have intercepted much more than 100,000 malicious SMS messages attempting to distribute Flubot malware given that the starting of December.
“Conclusions indicate attackers are modifying their topic lines and making use of older nevertheless demonstrated scams to entice end users to click,” the Romanian cybersecurity firm in depth in a report posted Wednesday. “In addition, attackers are promptly modifying the international locations they are concentrating on in this campaign.”
The new wave of attacks is claimed to have been most lively in Australia, Germany, Poland, Spain, Austria, and Italy, amongst other individuals, with attacks spreading to newer nations like Romania, the Netherlands, and Thailand setting up mid-January.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
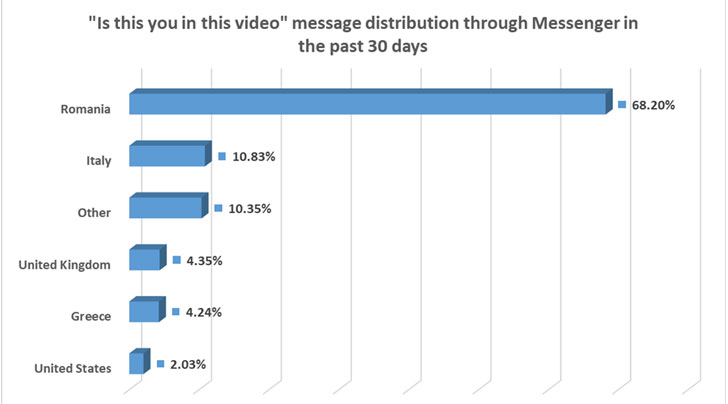
FluBot (aka Cabassous) strategies use smishing as the key shipping and delivery strategy to goal likely victims, whereby consumers obtain an SMS message with the question “Is this you in this online video?” and are tricked into clicking a link that installs the malware.

“This new vector for banking trojans exhibits that attackers are on the lookout to increase earlier the regular malicious SMS messages,” the researchers explained.
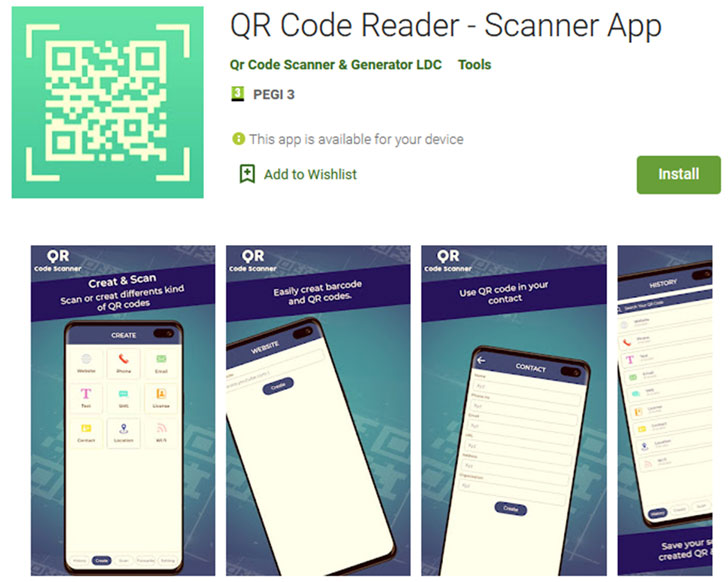
TeaBot masquerades as QR Code Scanner Apps
It is really not just FluBot. A different Android trojan named TeaBot (aka Anatsa) has been observed lurking on the Google Enjoy Shop in the type of an application named “QR Code Reader – Scanner Application,” attracting no much less than 100,000 downloads even though delivering 17 various variants of the malware among December 6, 2021, and January 17, 2022.
In a tactic that is getting to be progressively prevalent, the app does give the promised performance, but it really is also created to retrieve a malicious APK file hosted on GitHub, but not prior to ascertaining that the country code of the current registered operator does not start off with a “U.”
The installation of the rogue app then includes presenting a bogus UI notifying the consumer that an increase-on update is necessary and that the environment to allow for installs from mysterious resources needs to be enabled in order to utilize the update.
BitDefender explained it discovered 4 more dropper apps — 2FA Authenticator, QR Scanner APK, QR Code Scan, and Wise Cleaner — that were being available on the Engage in Store and distributed the TeaBot malware considering that at least April 2021.
One more technique of curiosity adopted by the operators is versioning, which will work by distributing a benign variation of an application to the app store for purposes of evading the critique course of action set in location by Google, only to swap the codebase around time with extra malicious features via updates at a later on date.
Outside of circumventing the Enjoy Shop protections to arrive at a wider an infection pool, the operators are believed to have paid out to appear in Google Adverts served within just other authentic applications and game titles, “supplying them display screen time in an application that could have thousands and thousands of customers.”
The examination also corroborates a earlier report from Dutch cybersecurity firm ThreatFabric, which located six Anatsa droppers on the Enjoy Shop since June 2021. The apps had been programmed to down load an “update” adopted by prompting consumers to grant them Accessibility Company privileges and permissions to put in applications from mysterious third-party sources.
“Malicious actors deal with malware like a product or service, with development and versioning, performing hard to circumvent security technologies and achieve additional victims,” Richard Melick, director of product or service system for endpoint security at Zimperium, said.
“When 1 edition will get disrupted, the destructive actors go back to building the subsequent model, specifically when the results have been successful. And the mobile endpoint is an amazingly valuable goal for attackers,” Melick included.
From GriftHorse to Dark Herring
The improvement comes as Zimperium zLabs disclosed details of still yet another top quality service abuse marketing campaign along the strains of GriftHorse that leveraged as numerous as 470 benign-on the lookout applications to subscribe consumers to compensated solutions costing $15 for each thirty day period without the need of their knowledge.
The billing fraud, also classified as “fleeceware,” is reported to have influenced upwards of 105 million end users across a lot more than 70 countries, with most victims positioned in Egypt, Finland, India, Pakistan, and Sweden.
The mammoth procedure, which the cellular security business codenamed “Dark Herring,” has been backtraced to March 2020, building it a person of the longest-managing cell SMS cons discovered to day.
Even though the large nest of trojan applications have because been purged from the Perform Shop, they are still obtainable on third-party app stores, once yet again underscoring the possible dangers when it comes to sideloading purposes on to cellular equipment.
“In addition to more than 470 Android applications, the distribution of the programs was very perfectly-planned, spreading their applications across multiple, varied classes, widening the vary of possible victims,” Zimperium researcher Aazim Yaswant explained. “The applications them selves also functioned as marketed, rising the wrong sense of confidence.”
Located this posting attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to study far more distinctive articles we write-up.
Some elements of this posting are sourced from:
thehackernews.com



 Hackers Using New Evasive Technique to Deliver AsyncRAT Malware
Hackers Using New Evasive Technique to Deliver AsyncRAT Malware