The operators of TrickBot malware have infected an approximated 140,000 victims throughout 149 nations around the world a minor more than a calendar year immediately after tries were being to dismantle its infrastructure, even as the malware is rapid starting to be an entry position for Emotet, an additional botnet that was taken down at the begin of 2021.
Most of the victims detected since November 1, 2020, are from Portugal (18%), the U.S. (14%), and India (5%), followed by Brazil (4%), Turkey (3%), Russia (3%), and China (3%), Look at Issue Exploration observed in a report shared with The Hacker News, with federal government, finance, and producing entities emerging the top rated impacted marketplace verticals.
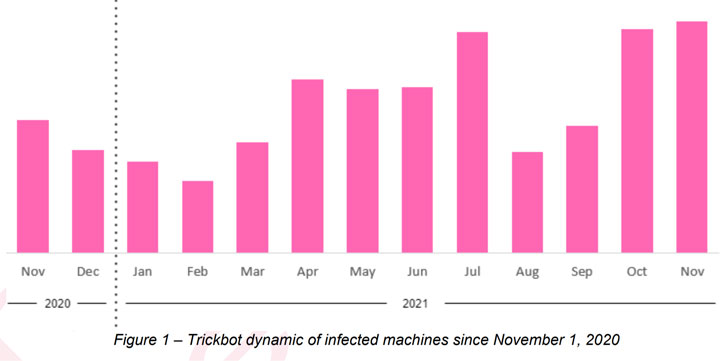
“Emotet is a solid indicator of long run ransomware attacks, as the malware delivers ransomware gangs a backdoor into compromised machines,” explained the researchers, who detected 223 unique Trickbot campaigns above the training course of the past six months.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Both TrickBot and Emotet are botnets, which are a network of internet-connected gadgets infected by malware and can be tasked to conduct an array of malicious functions. TrickBot originated as a C++ banking Trojan and as a successor of Dyre malware in 2016, that includes capabilities to steal monetary aspects, account credentials and other sensitive details laterally unfold throughout a network and fall extra payloads, including Conti, Diavol, and Ryuk ransomware payloads.

Disseminated through malspam campaigns or previously dropped by other malware like Emotet, TrickBot is considered to be the handiwork of a Russia-centered team identified as Wizard Spider and has since prolonged its capabilities to develop a entire modular malware ecosystem, making it an adaptable and evolving threat, not to mention an attractive instrument for conducting a myriad of illegal cyber actions.
The botnet also caught the consideration of federal government and private entities late previous year, when the U.S. Cyber Command and a team of private sector associates spearheaded by Microsoft, ESET, and Symantec acted to blunt Trickbot’s access and avert the adversary from purchasing or leasing servers for command-and-handle operations.
Emotet arrives back with new tips
But these actions have only been non permanent setbacks, with the malware authors rolling out updates to the botnet code that have manufactured it extra resilient and suited for mounting further more attacks. What’s much more, TrickBot bacterial infections in November and December have also propelled a surge in Emotet malware on compromised devices, signaling a revival of the infamous botnet just after a gap of 10 months subsequent a coordinated legislation enforcement exertion to disrupt its unfold.
“Emotet could not choose a greater platform than Trickbot as a supply assistance when it came to its rebirth,” the scientists famous.

The most current wave of spam attacks prompts users to down load password-shielded ZIP archive files, which consist of destructive documents that, once opened and macros are enabled, final result in the deployment of Emotet malware, thus enabling it to rebuild its botnet network and increase in quantity.
“Emotet’s comeback is a significant warning indicator for nonetheless a different surge in ransomware attacks as we go into 2022,” reported Lotem Finkelstein, Look at Point’s head of danger intelligence. “Trickbot, who has often collaborated with Emotet, is facilitating Emotet’s comeback by dropping it on contaminated victims. This has allowed Emotet to begin from a incredibly business situation, and not from scratch.”
That’s not all. In what seems to be a additional escalation in methods, new Emotet artifacts have been uncovered dropping Cobalt Strike beacons immediately on to compromised units, according to Cryptolaemus cybersecurity industry experts, as opposed to dropping 1st-stage payloads before installing the submit-exploitation software.
“This is a major offer. Usually Emotet dropped TrickBot or QakBot, which in switch dropped Cobalt Strike. You’d typically have about a month amongst [the] initial an infection and ransomware. With Emotet dropping [Cobalt Strike] specifically, there is possible to be a considerably significantly shorter hold off,” security researcher Marcus Hutchins tweeted.
Uncovered this article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to go through much more exclusive information we submit.
Some components of this post are sourced from:
thehackernews.com


 French Transport Giant Exposes 57,000 Employees and Source Code
French Transport Giant Exposes 57,000 Employees and Source Code