A nascent service called Dark Utilities has currently captivated 3,000 users for its means to supply command-and-command (C2) expert services with the objective of commandeering compromised systems.
“It is marketed as a means to enable remote accessibility, command execution, dispersed denial-of-assistance (DDoS) attacks and cryptocurrency mining operations on infected methods,” Cisco Talos reported in a report shared with The Hacker News.
Dark Utilities, which emerged in early 2022, is marketed as a “C2-as-a-Assistance” (C2aaS), giving accessibility to infrastructure hosted on the clearnet as nicely as the TOR network and linked payloads with support for Windows, Linux, and Python-primarily based implementations for a mere €9.99.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

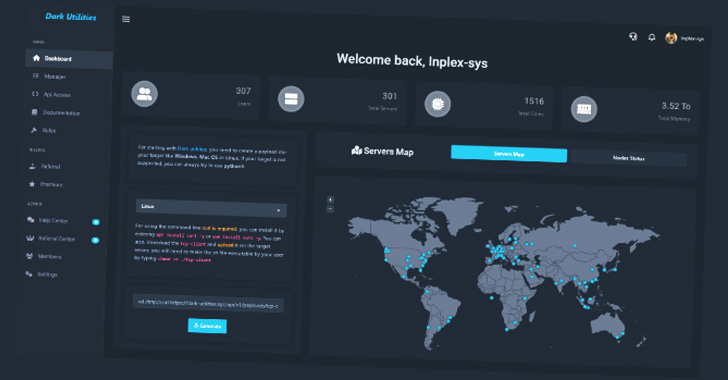
Authenticated end users on the platform are introduced with a dashboard that helps make it doable to produce new payloads customized to a particular running program that can then be deployed and executed on victim hosts.
Furthermore, users are offered an administrative panel to run instructions on the machines underneath their management on developing an lively C2 channel, properly granting the attacker comprehensive accessibility to the techniques.
The thought is to empower danger actors to concentrate on a number of architectures without the need of requiring considerable advancement endeavours. Also prolonged to its shoppers are complex guidance and help through Discord and Telegram.
“Provided the reasonably reduced charge when compared to the sum of features the platform offers, it is probable eye-catching to adversaries attempting to compromise programs with out necessitating them to generate their personal C2 implementation within their malware payloads,” the researchers noted.
To add fuel to the hearth, the malware artifacts are hosted inside the decentralized InterPlanetary File System (IPFS) resolution, building them resilient to content moderation or law enforcement intervention in a manner comparable to “bulletproof hosting.”
“IPFS is at present currently being abused by a range of menace actors who are using it to host malicious contents as aspect of phishing and malware distribution campaigns,” Talos researcher Edmund Brumaghin explained to The Hacker News.

“[The IPFS gateway] allows computer systems on the internet to access contents hosted within just the IPFS network without having the prerequisite for a customer software program set up, comparable to how Tor2Web gateways provide that operation for information hosted inside the Tor network.”
Dark Utilities is believed to be the handiwork of a risk actor who goes by the moniker Inplex-sys in the cybercriminal underground place, with Talos identifying some kind of a “collaborative connection” among Inplex-sys and a person of the operators of a botnet company named Smart Bot.
“Platforms like Dark Utilities lower the barrier to entry for cybercriminals getting into the risk landscape by enabling them to promptly launch attacks targeting a assortment of operating techniques,” the scientists reported.
“They also present a number of techniques that can be employed to further more monetize access received to devices in corporate environments and could direct to additional deployment of malware in the setting once preliminary entry has been obtained.”
Located this posting interesting? Abide by THN on Facebook, Twitter and LinkedIn to study additional distinctive content material we put up.
Some components of this posting are sourced from:
thehackernews.com

 Leading malware campaigns are abusing genuine Windows shortcuts to bypass Microsoft’s VBA macro block
Leading malware campaigns are abusing genuine Windows shortcuts to bypass Microsoft’s VBA macro block