Significant-functionality computing clusters belonging to college networks as properly as servers affiliated with federal government businesses, endpoint security suppliers, and internet services providers have been qualified by a newly identified backdoor that presents attackers the capability to execute arbitrary instructions on the techniques remotely.
Cybersecurity business ESET named the malware “Kobalos” — a nod to a “mischievous creature” of the similar identify from Greek mythology — for its “small code measurement and numerous tips.”
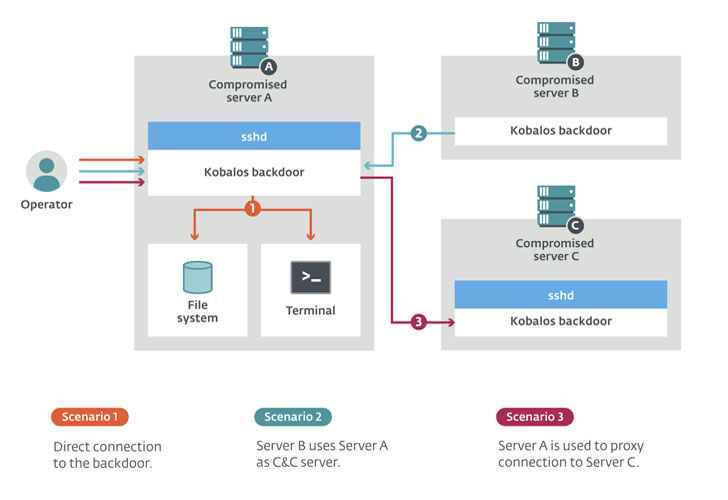
“Kobalos is a generic backdoor in the feeling that it contains broad commands that don’t reveal the intent of the attackers,” scientists Marc-Etienne M. Léveillé and Ignacio Sanmillan stated in a Tuesday investigation. “In shorter, Kobalos grants distant access to the file technique, provides the capacity to spawn terminal sessions, and permits proxying connections to other Kobalos-contaminated servers.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Aside from tracing the malware back to attacks against a variety of substantial-profile targets, ESET mentioned the malware is capable of having purpose at Linux, FreeBSD, Solaris, and probably AIX and Windows devices, with code references hinting at Windows 3.11 and Windows 95 legacy operating methods.
Kobalos bacterial infections are believed to have commenced in late 2019 and have considering that continued to continue being energetic in the course of 2020.
The initial compromise vector used to deploy the malware and the ultimate objective of the menace actor continues to be unclear as but, but the existence of a trojanized OpenSSH client in a person of the compromised devices alludes to the probability that “credential stealing could be a single of the techniques Kobalos propagates.”
No other malware artifacts were located on the units, nor have there been any evidence that could possibly expose the attackers’ intent.
“We have not uncovered any clues to point out no matter if they steal confidential data, go after financial achieve, or are just after one thing else,” the researchers mentioned.
But what they did uncover displays the multi-system malware harbors some uncommon tactics, together with attributes that could switch any compromised server into a command-and-handle (C&C) server for other hosts compromised by Kobalos.
In other terms, infected devices can be utilised as proxies that join to other compromised servers, which can then be leveraged by the operators to make new Kobalos samples that use this new C&C server to make a proxy chain comprising of numerous contaminated servers to access their targets.
To manage stealth, Kobalos authenticates connections with contaminated machines working with a 32-byte password which is generated and then encrypted with a 512-little bit RSA private key. Subsequently, a set of RC4 keys are utilised — a single each and every for inbound site visitors and outbound targeted traffic — for communications with the C&C server.
The backdoor also leverages a complicated obfuscation mechanism to thwart forensic analysis by recursively contacting the code to complete a huge array of subtasks.
“The numerous perfectly-carried out attributes and the network evasion methods exhibit the attackers behind Kobalos are considerably additional knowledgeable than the usual malware author targeting Linux and other non-Windows units,” the scientists stated.
“Their targets, being fairly large-profile, also display that the objective of the Kobalos operators is just not to compromise as many systems as doable. Its little footprint and network evasion methods could make clear why it went undetected right up until we approached victims with the benefits of our Internet-huge scan.”
Uncovered this report intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to study far more exceptional written content we article.
Some parts of this posting are sourced from:
thehackernews.com


 Over Three Million US Drivers Exposed in Data Breach
Over Three Million US Drivers Exposed in Data Breach