Security scientists on Tuesday uncovered new shipping and delivery and evasion strategies adopted by Agent Tesla remote access trojan (RAT) to get all over protection obstacles and check its victims.
Normally distribute as a result of social engineering lures, the Windows spyware not only now targets Microsoft’s Antimalware Scan Interface (AMSI) in an attempt to defeat endpoint safety software package, it also employs a multi-stage set up process and would make use of Tor and Telegram messaging API to connect with a command-and-management (C2) server.
Cybersecurity organization Sophos, which observed two versions of Agent Tesla — variation 2 and edition 3 — currently in the wild, said the changes are yet yet another indication of Agent Tesla’s continual evolution built to make a sandbox and static analysis much more challenging.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“The dissimilarities we see involving v2 and v3 of Agent Tesla surface to be concentrated on bettering the accomplishment amount of the malware in opposition to sandbox defenses and malware scanners, and on delivering additional C2 solutions to their attacker shoppers,” Sophos scientists pointed out.
A .NET based mostly keylogger and info stealer, Agent Tesla has been deployed in a number of attacks since late 2014, with additional functions integrated about time that lets it to check and obtain the victim’s keyboard enter, take screenshots, and exfiltrate credentials belonging to a range of program these as VPN clientele, FTP and email clientele, and web browsers.
Previous Might, for the duration of the peak of the pandemic, a variant of the malware was discovered to unfold by using COVID-themed spam strategies to steal Wi-Fi passwords alongside other facts – this sort of as Outlook email qualifications – from focus on methods.
Then in August 2020, the next variation of Agent Malware enhanced the number of applications focused for credential theft to 55, the final results of which were being then transmitted to an attacker-controlled server by using SMTP or FTP.
While the use of SMTP to deliver information and facts to a mail server controlled by the attacker was noticed way back again in 2018, one of the new variations determined by Sophos was also located to leverage Tor proxy for HTTP communications and messaging app Telegram’s API to relay the facts to a private chat home.
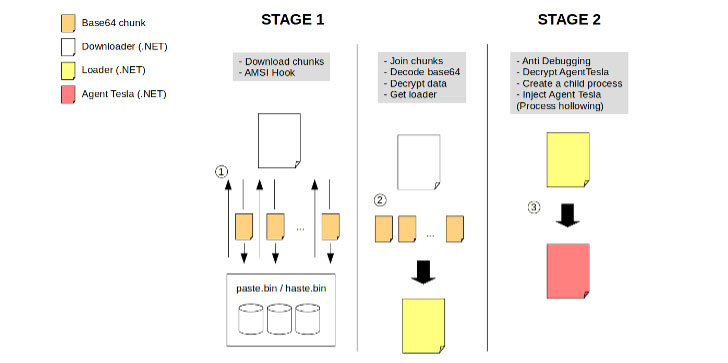
Aside from this, Agent Tesla now attempts to modify code in AMSI in a bid to skip scans of destructive payloads fetched by the 1st-phase downloader, which then grabs obfuscated foundation64-encoded code from Pastebin (or Hastebin) that acts as the loader for the Agent Tesla malware.
AMSI is an interface conventional that lets apps and products and services to be built-in with any existing antimalware merchandise that’s current on a Windows equipment.
On top of that, to achieve persistence, the malware copies itself to a folder and sets that folder’s characteristics to “Hidden” and “Program” in purchase to conceal it from see in Windows Explorer, the scientists spelled out.
“The most prevalent shipping system for Agent Tesla is malicious spam,” Sophos danger scientists Sean Gallagher and Markel Picado mentioned.
“The email accounts used to distribute Agent Tesla are generally authentic accounts that have been compromised. Businesses and individuals must, as usually, take care of email attachments from unfamiliar senders with caution, and verify attachments ahead of opening them.”
Observed this report interesting? Observe THN on Facebook, Twitter and LinkedIn to read additional exclusive content material we put up.
Some sections of this article are sourced from:
thehackernews.com


 Barclays: 2020 the Highest Year on Record for Scams
Barclays: 2020 the Highest Year on Record for Scams