For 6 months, the infamous Emotet botnet has revealed virtually no activity, and now it’s distributing destructive spam. Let us dive into information and go over all you will need to know about the notorious malware to fight it.
Why is anyone scared of Emotet?
Emotet is by much 1 of the most unsafe trojans at any time established. The malware turned a very destructive application as it grew in scale and sophistication. The victim can be anyone from corporate to non-public buyers uncovered to spam email campaigns.
The botnet distributes through phishing containing malicious Excel or Phrase documents. When users open these files and enable macros, the Emotet DLL downloads and then masses into memory.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It searches for email addresses and steals them for spam campaigns. In addition, the botnet drops supplemental payloads, these as Cobalt Strike or other attacks that direct to ransomware.
The polymorphic mother nature of Emotet, together with the quite a few modules it contains, will make the malware difficult to identify. The Emotet staff constantly adjustments its ways, approaches, and procedures to assure that the existing detection policies can’t be used. As element of its tactic to keep invisible in the infected system, the destructive application downloads extra payloads making use of numerous measures.
And the benefits of Emotet habits are devastating for cybersecurity professionals: the malware is approximately unattainable to remove. It spreads quickly, generates defective indicators, and adapts according to attackers’ requirements.
How has Emotet upgraded above the yrs?
Emotet is an highly developed and continuously modifying modular botnet. The malware begun its journey as a simple banking trojan in 2014. But because then, it has obtained a bunch of different attributes, modules, and campaigns:
- 2014. Funds transfer, mail spam, DDoS, and tackle ebook stealing modules.
- 2015. Evasion performance.
- 2016. Mail spam, RIG 4. exploit package, supply of other trojans.
- 2017. A spreader and address e-book stealer module.
- 2021. XLS malicious templates, takes advantage of MSHTA, dropped by Cobalt Strike.
- 2022. Some functions remained the exact same, but this yr also brought various updates.
This inclination proves that Emotet isn’t going anyplace irrespective of regular “vacations” and even the formal shutdown. The malware evolves fast and adapts to every thing.
What capabilities has a new Emotet 2022 version acquired?
Just after just about fifty percent a year of a break, the Emotet botnet returned even stronger. Below is what you will need to know about a new 2022 variation:
- It drops IcedID, a modular banking trojan.
- The malware loads XMRig, a miner that steals wallet facts.
- The trojan has binary improvements.
- Emotet bypasses detection making use of a 64-bit code base.
- A new version employs new instructions:
Invoke rundll32.exe with a random named DLL and the export PluginInit
- Emotet’s goal is to get credentials from Google Chrome and other browsers.
- It truly is also focused to make use of the SMB protocol to collect enterprise data
- Like six months back, the botnet employs XLS destructive lures, but it adopted a new a single this time:

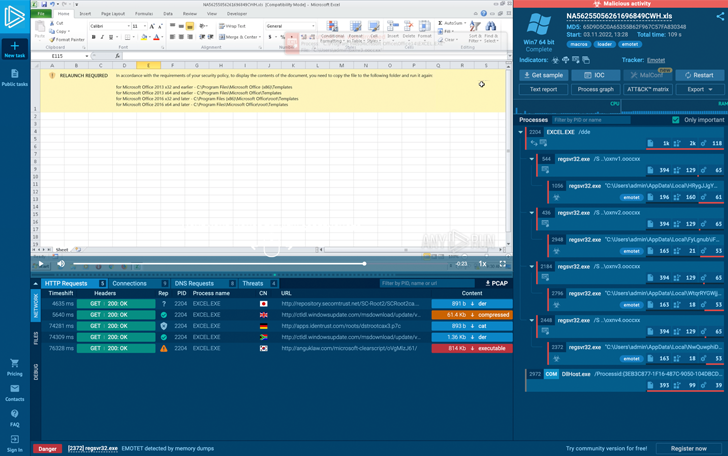 The Emotet’s Excel entice
The Emotet’s Excel entice
How to detect Emotet?
The key Emotet obstacle is to detect it in the process rapidly and precisely. Apart from that, a malware analyst need to comprehend the botnet’s habits to avert potential attacks and stay away from probable losses.
With its prolonged story of progress, Emotet stepped up in the anti-evasion tactic. By the evolution of the approach execution chain and malware action within the infected program variations, the malware has modified detection methods greatly.
For case in point, in 2018, it was probable to detect this banker by on the lookout at the name of the procedure – it was 1 of these:
eventswrap, implrandom, turnedavatar, soundser, archivesymbol, wabmetagen, msrasteps, secmsi, crsdcard, narrowpurchase, smxsel, watchvsgd, mfidlisvc, searchatsd, lpiograd, noticesman, appxmware, sansidaho
Later on, in the initially quarter of 2020, Emotet begun to create certain critical into the registry – it writes into the vital HKEY_Present-day_USERSOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORER worth with the length 8 symbols (letters and people).
Of training course, Suricata policies usually detect this malware, but detection techniques frequently keep on outside of the first wave because procedures will need to update.
Another way to detect this banker was its destructive files – crooks use unique templates and lures, even with grammatical errors in them. A person of the most responsible means to detect Emotet is by the YARA rules.
To conquer malware’s anti-evasion approaches and seize the botnet – use a malware sandbox as the most effortless software for this goal. In ANY.Operate, you can not only detect, check, and review destructive objects but also get presently extracted configurations from the sample.
There are some options that you use just for Emotet analysis:
- expose C2 inbound links of a malicious sample with the FakeNet
- use Suricata and YARA rulesets to properly recognize the botnet
- Get data about C2 servers, keys, and strings extracted from the sample’s memory dump
- assemble clean malware’s IOCs
The resource helps to perform successful investigations rapidly and exactly, so malware analysts can conserve important time.
ANY.Run sandbox has organized extraordinary deals for Black Friday 2022! Now is the very best time to improve your malware analysis and save some money! Look at out exclusive features for their high quality plans but for a confined time – from 22-29 November, 2022.

Emotet has not shown complete operation and consistent comply with-on payload supply. Use modern day instruments like ANY.Operate on line malware sandbox to boost your cybersecurity and detect this botnet properly. Continue to be safe and sound and great danger hunting!
Found this short article exciting? Observe THN on Fb, Twitter and LinkedIn to examine extra special material we submit.
Some sections of this report are sourced from:
thehackernews.com


 U.S. Bans Chinese Telecom Equipment and Surveillance Cameras Over National Security Risk
U.S. Bans Chinese Telecom Equipment and Surveillance Cameras Over National Security Risk