Approximately 32% of freshly launched business purposes comprise security flaws from the first vulnerability scan, program security company Veracode identified in its hottest once-a-year Point out of Software Security Report, released on January 11, 2022.
While the report also demonstrates what the Veracode researchers call a ‘honeymoon period’ that runs till a yr and a fifty percent just after introducing the purposes, where by much less flaws are uncovered to be introduced in the applications’ code this amount picks up once again following a lengthier period of time.
By the time they have been in generation for five yrs, practically 70% of programs contain at the very least a single security flaw.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“What it displays is that, as they get further more along in the apps lifecycle, there is something that will allow the programs to get even worse, whether it is the composition of the groups or builders transferring on and off or the codebase just acquiring additional complicated,” Chris Eng, main analysis officer at Veracode, advised Infosecurity.
No Correlation Concerning Flaw Introduction and the Code Duration
Veracode’s researchers, even so, uncovered no immediate correlation amongst the advancement of an software – when its code will get for a longer period – and the price of flaw introduction.
Dependent on these results, Veracode concluded that “developer teaching, use of multiple scan sorts, like scanning by means of API, and scan frequency are influential aspects in minimizing the probability of flaw introduction, suggesting teams ought to make them key parts of their software security programs”.
“For case in point, skipping months concerning scans correlates with an greater likelihood that flaws will be identified when a scan is sooner or later operate,” a spokesperson said in a assertion.
Moreover, prime flaws in apps vary by screening kind: for occasion, server configuration flaws accounted for 96.5% of vulnerabilities determined by Veracode’s dynamic examination but for only 11.1% of their static assessment.
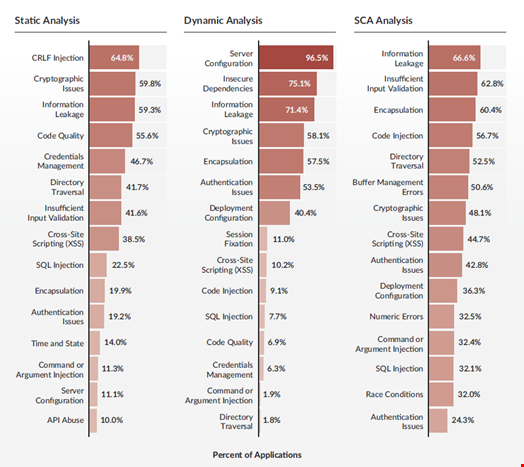 Top flaws identified in Veracode’s 2023 Point out of Application Security Report by scan style. Resource: Veracode
Top flaws identified in Veracode’s 2023 Point out of Application Security Report by scan style. Resource: Veracode
This consequence “highlights the significance of making use of multiple scan styles to ensure really hard-to-recognize flaws are not missed,” the Veracode spokesperson explained.
Software package Composition Analysis is Crucial
With a heightened emphasis on the software program monthly bill of elements (SBOMs) above the past calendar year, a need that was portion of President Biden’s 2021 executive order Improving the Nation’s Cybersecurity, Veracode’s study staff also examined 30,000 open-source repositories publicly hosted on GitHub.
Of those examined, 10% of them hadn’t experienced a dedicate – a modify to the resource code – for nearly six several years.
“Using a software package composition evaluation (SCA) resolution that leverages numerous resources for flaws, beyond the Nationwide Vulnerability Database, will give progress warning to teams as soon as a vulnerability is disclosed and help them to apply safeguards much more promptly, ideally just before exploitation starts. Environment organizational policies all-around vulnerability detection and administration is also suggested, as properly as looking at strategies to cut down 3rd-party dependencies,” Eng recommended.
Veracode’s report was primarily based on 750,000 enterprise purposes throughout all sectors, scanned using 3 procedures: static analysis, dynamic examination and computer software composition analysis (SCA).
Some components of this report are sourced from:
www.infosecurity-journal.com


 Microsoft’s ‘unusually large’ Patch Tuesday fixes actively exploited zero day, 11 critical vulnerabilities
Microsoft’s ‘unusually large’ Patch Tuesday fixes actively exploited zero day, 11 critical vulnerabilities