A Brazilian danger actor recognized as Prilex has resurfaced following a year-lengthy operational hiatus with an state-of-the-art and advanced malware to steal dollars by usually means of fraudulent transactions.
“The Prilex team has demonstrated a higher stage of understanding about credit rating and debit card transactions, and how program used for payment processing performs,” Kaspersky researchers claimed. “This enables the attackers to keep updating their equipment in get to locate a way to circumvent the authorization procedures, letting them to perform their attacks.”
The cybercrime group emerged on the scene with ATM-centered malware attacks in the South American nation, giving it the ability to break into ATM machines to complete jackpotting – a sort of attack aiming to dispense income illegitimately – and clone hundreds of credit score cards to steal money from the targeted bank’s shoppers.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Prilex’s modus operandi more than the several years has considering the fact that progressed to just take gain of procedures relating to point-of-sale (PoS) software program to intercept and modify communications with digital units these types of as PIN pads, which are utilised to facilitate payments employing debit or credit history playing cards.
Identified to be active because 2014, the operators are also adept at carrying out EMV replay attacks in which traffic from a legitimate EMV-based chip card transaction is captured and replayed to a payment processor like Mastercard, but with the transaction fields modified to contain stolen card details.
Infecting a laptop with PoS software package put in is a extremely-focused attack incorporating a social engineering ingredient that enables the threat actor to deploy the malware.
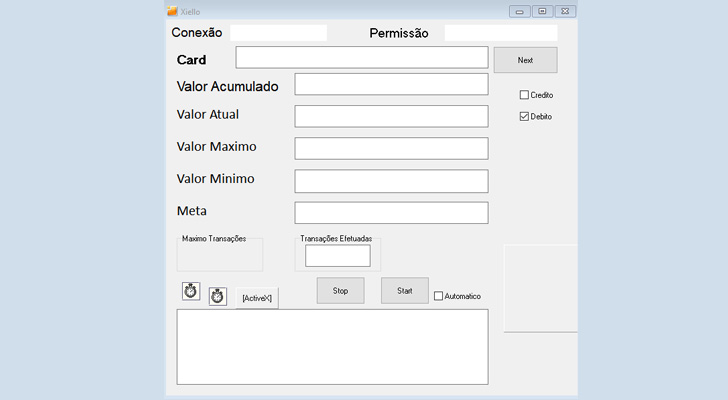
“A focus on enterprise may well get a contact from a ‘technician’ who insists that the enterprise demands to update its PoS application,” the scientists famous. “The bogus technician may well visit the concentrate on in particular person or request the victims to install AnyDesk and provide distant entry for the ‘technician’ to set up the malware.”
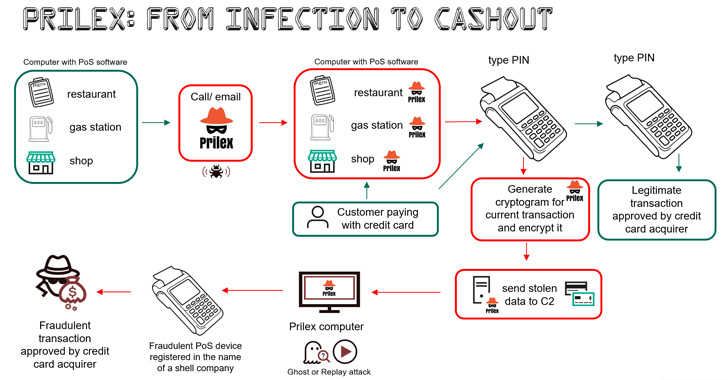
The most up-to-date installments noticed in 2022, nevertheless, exhibit a single vital difference in that the replay attacks have been substituted with an alternate strategy to illicitly dollars out money applying cryptograms generated by the sufferer card throughout the in-retail store payment method.
The approach, referred to as GHOST transactions, incorporates a stealer component that grabs all communications among the PoS application and the PIN pad applied for examining the card in the course of the transaction with the intention of getting the card facts.
This is subsequently transmitted to a command-and-command (C2) server, permitting the danger actor to make transactions via a fraudulent PoS product registered in the identify of a faux enterprise.

Now, it is really truly worth pointing out that EMV chip cards use what is actually referred to as a cryptogram to secure cardholder facts each and every time a transaction is built. This is carried out so as to validate the identification of the card and the acceptance from the card issuer, thereby lowering the risk of counterfeit transactions.
While former variations of Prilex circumvented these security steps by checking the ongoing transaction to get the cryptogram and carry out a replay attack working with the gathered “signature,” the GHOST attack requests for new EMV cryptograms that are set to use to full the rogue transactions.
Also baked into the malware is a backdoor module that is engineered to debug the PoS program behavior and make adjustments on the fly. Other backdoor instructions authorize it to terminate processes, get started and end screen captures, down load arbitrary documents from the C2 server, and execute instructions applying CMD.
Prilex is “working immediately with the PIN pad components protocol in its place of employing better degree APIs, performing true-time patching in focus on program, hooking working technique libraries, messing with replies, communications and ports, and switching from a replay-centered attack to deliver cryptograms for its GHOST transactions even from credit history cards protected with CHIP and PIN technology,” the scientists explained.
Identified this short article fascinating? Follow THN on Facebook, Twitter and LinkedIn to read much more exclusive information we article.
Some components of this article are sourced from:
thehackernews.com

 Cloud and cyber security certifications remain highest paying for IT professionals
Cloud and cyber security certifications remain highest paying for IT professionals