A economically-determined malware campaign has compromised around 800 WordPress sites to provide a banking trojan dubbed Chaes focusing on Brazilian shoppers of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
Initially documented by Cybereason in November 2020, the facts-thieving malware is shipped by means of a refined infection chain which is engineered to harvest delicate customer information, including login credentials, credit card figures, and other economical details.
“Chaes is characterised by the numerous-phase delivery that makes use of scripting frameworks such as JScript, Python, and NodeJS, binaries prepared in Delphi, and destructive Google Chrome extensions,” Avast researchers Anh Ho and Igor Morgenstern explained. “The final aim of Chaes is to steal credentials stored in Chrome and intercept logins of well known banking internet websites in Brazil.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The attack sequence is induced when people go to 1 of the contaminated web sites, upon which a pop-up is exhibited, urging them to put in a phony Java Runtime application. Ought to the user observe as a result of the recommendations, the rogue installer initiates a intricate malware shipping program that culminates in the deployment of a number of modules.
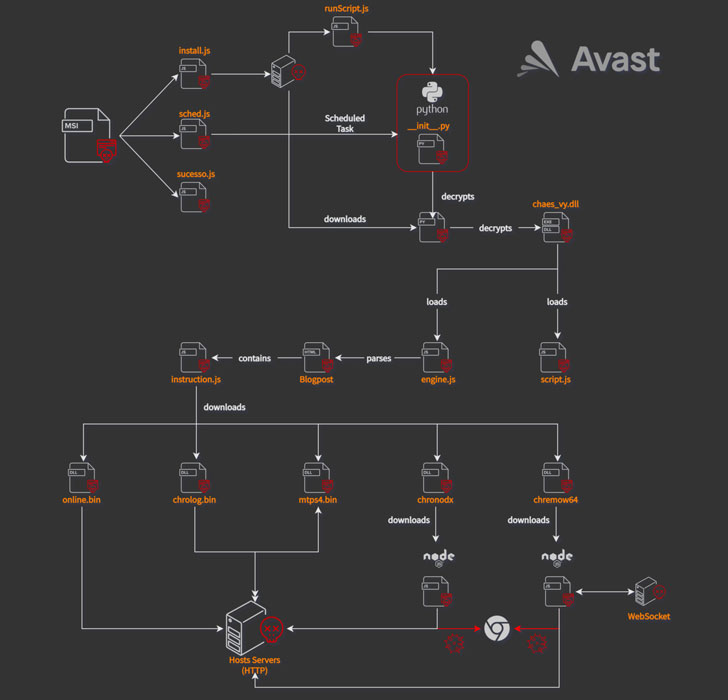
Some of the middleman payloads are not only encrypted but also concealed as commented-out code inside of the HTML web site of a Blogger blogspot domain (“awsvirtual[.]blogspot.com”). In the closing phase, a JavaScript dropper downloads and installs as numerous as five Chrome extensions —
- On the web – A Delphi module used to fingerprint the victim and transmit the method details to a command-and-control (C2) server
- Mtps4 (MultiTela Pascal) – A Delphi-primarily based backdoor whose most important intent is to link to the C2 server and wait around for a responding Pascal Script to execute
- Chrolog (ChromeLog) – A Google Chrome password stealer published in Delphi
- Chronodx (Chrome Noder) – A JavaScript trojan that, on detecting the start of Chrome browser by the target, closes it straight away and reopens its possess instance of Chrome made up of a malicious module that steals banking facts
- Chremows (Chrome WebSocket) – A JavaScript banking trojan that information keypresses and mouse clicks on Chrome with the target of plundering login qualifications from users of Mercado Livre and Mercado Pago
Stating that the attacks are ongoing, Avast reported that it experienced shared its results with the Brazilian CERT to disrupt the malware’s distribute. That mentioned, Chaes-relevant artifacts continue on to remain on some of the infected web sites.
“Chaes exploits numerous websites that contains CMS WordPress to serve malicious installers,” the researchers concluded. “The Google Chrome extensions are able to steal users’ credentials saved in Chrome and gather users’ banking info from well known banking websites.”
Observed this post exciting? Abide by THN on Facebook, Twitter and LinkedIn to go through more exceptional material we write-up.
Some sections of this post are sourced from:
thehackernews.com


 Apple fixes array of iOS, macOS zero-days and code execution security flaws
Apple fixes array of iOS, macOS zero-days and code execution security flaws