GitHub Actions and Azure digital devices (VMs) are remaining leveraged for cloud-based mostly cryptocurrency mining, indicating sustained tries on the aspect of destructive actors to target cloud assets for illicit needs.
“Attackers can abuse the runners or servers supplied by GitHub to run an organization’s pipelines and automation by maliciously downloading and installing their have cryptocurrency miners to achieve profit effortlessly,” Craze Micro researcher Magno Logan reported in a report final 7 days.
GitHub Actions (GHAs) is a constant integration and constant shipping (CI/CD) platform that permits buyers to automate the computer software build, test, and deployment pipeline. Developers can leverage the function to make workflows that build and exam each and every pull ask for to a code repository, or deploy merged pull requests to manufacturing.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Both of those Linux and Windows runners are hosted on Regular_DS2_v2 digital equipment on Azure and appear with two vCPUs and 7GB of memory.
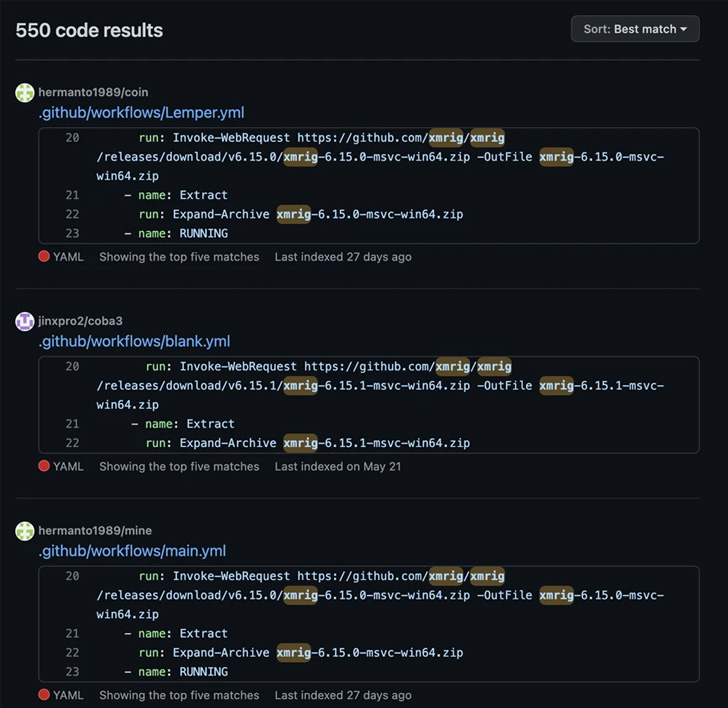
The Japanese corporation stated it identified no less than 1,000 repositories and above 550 code samples that are having gain of the system to mine cryptocurrency using the runners delivered by GitHub, which has been notified of the issue.
What is actually more, 11 repositories were being discovered to harbor comparable variants of a YAML script that contains instructions to mine Monero cash, all of which relied on the exact same wallet, suggesting it’s possibly the handiwork of a solitary actor or a group functioning in tandem.
“For as very long as the destructive actors only use their possess accounts and repositories, conclude consumers should have no result in for be concerned,” Logan reported. “Challenges occur when these GHAs are shared on GitHub Market or employed as a dependency for other Steps.”
Cryptojacking-oriented groups are recognised to infiltrate cloud deployments through the exploitation of a security flaw within just concentrate on methods, these as an unpatched vulnerability, weak credentials, or a misconfigured cloud implementation.
Some of the notable actors in the unlawful cryptocurrency mining landscape contain 8220, Keksec (aka Kek Security), Kinsing, Outlaw, and TeamTNT.

The malware toolset is also characterised by the use of destroy scripts to terminate and delete competing cryptocurrency miners to best abuse the cloud programs to their have benefit, with Development Micro contacting it a struggle “fought for command of the victim’s methods.”
That mentioned, the deployment of cryptominers, other than incurring infrastructure and strength expenses, are also a barometer of very poor security cleanliness, enabling threat actors to weaponize the original obtain gained via a cloud misconfiguration for much additional harming plans this sort of as details exfiltration or ransomware.
“One particular special aspect […] is that destructive actor groups do not only have to offer with a concentrate on organization’s security methods and staff members, but they also have to compete with 1 an additional for constrained resources,” the company observed in an before report.
“The battle to consider and retain regulate about a victim’s servers is a key driving drive for the evolution of these groups’ applications and tactics, prompting them to consistently strengthen their potential to take out competitors from compromised devices and, at the similar time, resist their own elimination.”
Found this short article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to study more special content we post.
Some components of this short article are sourced from:
thehackernews.com


 CEO of Dozens of Companies Charged in Scheme to Traffic An Estimated $1bn in Fake Cisco Devices
CEO of Dozens of Companies Charged in Scheme to Traffic An Estimated $1bn in Fake Cisco Devices