Scientists on Tuesday disclosed a new espionage marketing campaign that resorts to harmful information-wiping attacks concentrating on Israeli entities at least considering that December 2020 that camouflage the malicious action as ransomware extortions.
Cybersecurity business SentinelOne attributed the attacks to a nation-point out actor affiliated with Iran it tracks underneath the moniker “Agrius.”
“An examination of what at first sight appeared to be a ransomware attack discovered new variants of wipers that were deployed in a established of damaging attacks versus Israeli targets,” the researchers claimed. “The operators at the rear of the attacks deliberately masked their exercise as ransomware attacks, an unusual habits for economically inspired teams.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The group’s modus operandi consists of deploying a tailor made .NET malware named Apostle that has evolved to grow to be entirely practical ransomware, supplanting its prior wiper capabilities, although some of the attacks have been carried out utilizing a second wiper named DEADWOOD (aka Detbosit) soon after a logic flaw in early variations of Apostle prevented knowledge from staying erased.
In addition, the Agrius actors fall a .NET implant termed IPsec Helper that can be applied to exfiltrate data or deploy more malware. What is actually extra, the danger actor’s tactics have also witnessed a change from espionage to demanding ransoms from its victims to recover accessibility to encrypted info, only to have them actually destroyed in a wiping attack.
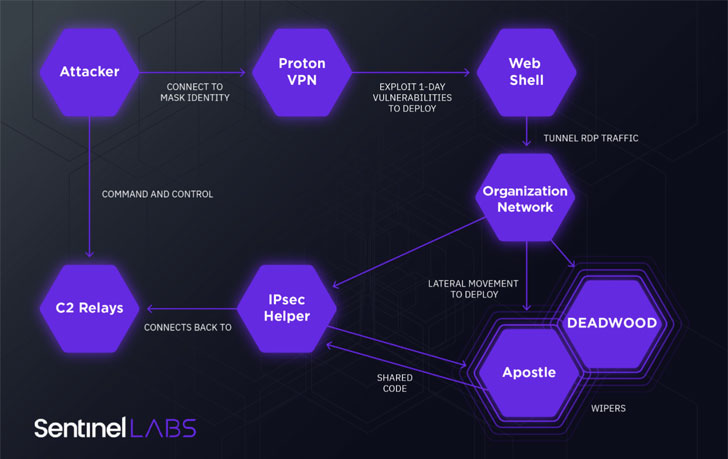
Moreover making use of ProtonVPN for anonymization, the Agrius attack cycle leverages 1-working day vulnerabilities in web-based mostly purposes, which includes CVE-2018-13379, to gain an preliminary foothold and subsequently provide ASPXSpy web shells to preserve distant accessibility to compromised techniques and run arbitrary commands.
If something, the investigation adds to evidence that condition-sponsored actors with ties to the Iranian authorities are ever more looking at ransomware functions as a subterfuge procedure to mimic other fiscally enthusiastic cybercriminal ransomware teams.
Lately leaked files by Lab Dookhtegan unveiled an initiative termed “Challenge Signal” that linked Iran’s Islamic Groundbreaking Guard Corps to a ransomware operation as a result of a contracting organization.
“Though becoming disruptive and successful, ransomware activities supply deniability, enabling states to send a concept without getting direct blame,” the scientists claimed. “Comparable strategies have been used with devastating outcome by other country-condition sponsored actors.”
Found this posting exciting? Observe THN on Fb, Twitter and LinkedIn to read through more exceptional material we publish.
Some pieces of this report are sourced from:
thehackernews.com


 22 Americans Indicted Over Card-Skimming Scam
22 Americans Indicted Over Card-Skimming Scam