Google Cloud previous 7 days disclosed that it identified 34 distinctive hacked launch versions of the Cobalt Strike resource in the wild, the earliest of which delivered in November 2012.
The versions, spanning 1.44 to 4.7, insert up to a complete of 275 exclusive JAR files, according to findings from the Google Cloud Menace Intelligence (GCTI) staff. The most recent variation of Cobalt Strike is variation 4.7.2.
Cobalt Strike, produced by Fortra (née HelpSystems), is a common adversarial framework utilised by crimson groups to simulate attack situations and check the resilience of their cyber defenses.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It comprises a Crew Server that functions as the command-and-manage (C2) hub to remotely commandeer infected equipment and a stager which is made to produce a next-stage payload called the Beacon, a fully-highlighted implant that reports again to the C2 server.
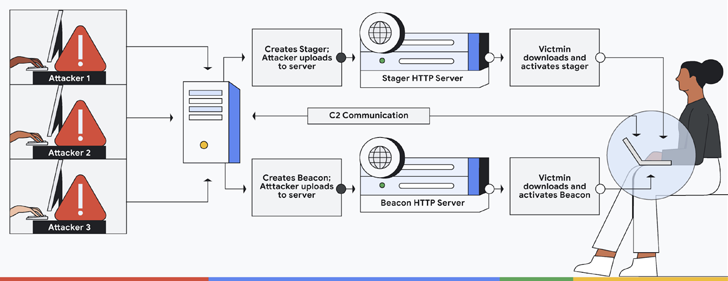
Given its vast-ranging suite of attributes, unauthorized variations of the software have been ever more weaponized by lots of a danger actor to advance their submit-exploitation activities.
“When the intention of Cobalt Strike is to emulate a genuine cyber danger, destructive actors have latched on to its capabilities, and use it as a robust software for lateral movement in their victim’s network as portion of their next-phase attack payload,” Greg Sinclair, a reverse engineer at Google’s Chronicle subsidiary, mentioned.
In a bid to tackle this abuse, GCTI has introduced a established of open resource YARA Rules to flag diverse variants of the software package employed by destructive hacking teams.
The concept is to “excise the poor versions although leaving the legitimate kinds untouched,” Sinclair claimed, introducing “our intention is to move the instrument again to the area of genuine crimson teams and make it more durable for bad fellas to abuse.”
Uncovered this short article intriguing? Follow THN on Facebook, Twitter and LinkedIn to examine additional exceptional articles we post.
Some elements of this post are sourced from:
thehackernews.com


 CISA, NSA, ODNI Publish Software Supply Chain Guidelines For Customers
CISA, NSA, ODNI Publish Software Supply Chain Guidelines For Customers