Facts of a new nation-state sponsored phishing marketing campaign has been uncovered setting its sights on European governmental entities in what is seen as an try to get intelligence on refugee and source movement in the area.
Organization security firm Proofpoint, which detected the malicious email messages for the first time on February 24, 2022, dubbed the social engineering attacks “Asylum Ambuscade.”
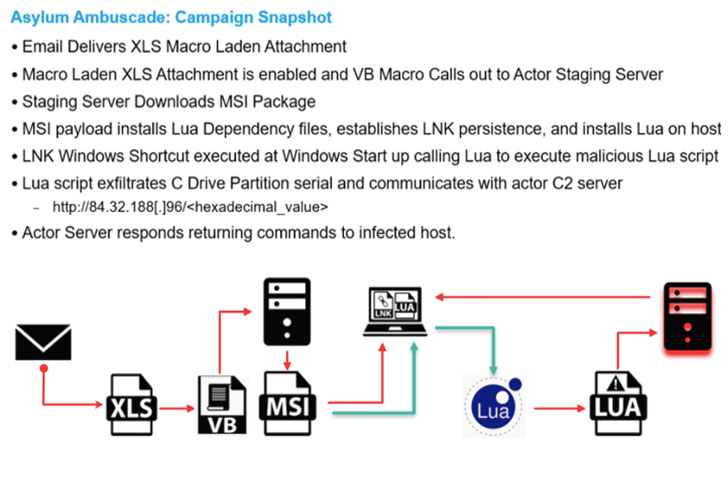
“The email involved a destructive macro attachment which used social engineering themes pertaining to the Crisis Conference of the NATO Security Council held on February 23, 2022,” researchers Michael Raggi and Zydeca Cass explained in a report posted Tuesday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The email also contained a malicious attachment which tried to obtain destructive Lua malware named SunSeed and focused European governing administration personnel tasked with handling transportation and populace motion in Europe.”
The conclusions construct on an advisory issued by the State Services of Particular Conversation and Facts Security of Ukraine (DSSZZI), which warned last week of phishing messages concentrating on its armed service staff with ZIP file attachments with the purpose of thieving delicate individual info.
Proofpoint declined to attribute the newly noticed campaign to a unique danger actor, but mentioned that the overlaps in the timeline of the two sets of attacks, the phishing lures made use of, and the victimology designs aligns with that of a Belarusian nation-point out group termed UNC1151 (aka TA445 or Ghostwriter).
Just one of the notable elements of Asylum Ambuscade is the possible use of a compromised Ukrainian armed assistance member’s email account to broadcast malware-laced email messages that contains a macro-enabled XLS file that delivers SunSeed onto infected hosts, implying that the most recent marketing campaign may be a continuation of these attacks.
“The social engineering lures used in this phishing marketing campaign have been pretty well timed, following a NATO Security Council conference on February 23, 2022 and a information story about a Russian governing administration ‘kill list’ concentrating on Ukrainians that commenced circulating in Western media retailers on February 21, 2022,” the scientists pointed out.
SunSeed, for its portion, features as a downloader that establishes communications with an actor-controlled server to retrieve future-phase payloads for execution.
The Sunnyvale-based cybersecurity company noted that the attacks particularly singled out individuals who have been tasked with duties associated to transportation, economical and finances allocation, administration, and population movement within just Europe.
The disclosure arrives as Russia’s intensifying army invasion of Ukraine has polarized cyberspace, with hacktivists, cybercriminals, white hat researchers, and technology providers choosing a facet in the conflict.
In a independent update posted earlier these days, Ukraine’s Personal computer Unexpected emergency Response Team (CERT-UA) described the ongoing developments as an “data and psychological war,” urging persons in the nation to diligently keep an eye on their accounts for unrecognized products, change on two-factor authentication, and use conclude-to-conclude encrypted messaging apps.
What is a lot more, email security corporation Avanan claimed it witnessed an eightfold raise in email-borne attacks originating from Russia setting up on February 27, at least some of them focusing on production, global delivery, and transportation companies positioned in the U.S. and Europe.
“In gentle of the ongoing Russia-Ukraine war, steps by proxy actors like TA445 will go on to concentrate on European governments to obtain intelligence close to the movement of refugees from Ukraine and on issues of importance to the Russian federal government,” the researchers claimed.
Observed this short article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to study far more exclusive material we publish.
Some areas of this write-up are sourced from:
thehackernews.com




 #CCSE22: “Zero Trust Model Is Becoming the Default Cyber Posture,” Claims Expert
#CCSE22: “Zero Trust Model Is Becoming the Default Cyber Posture,” Claims Expert