Menace actors are exploiting improperly-secured Google Cloud Platform (GCP) situations to down load cryptocurrency mining software to the compromised units as perfectly as abusing its infrastructure to put in ransomware, phase phishing campaigns, and even create website traffic to YouTube video clips for watch depend manipulation.
“Even though cloud prospects continue to face a variety of threats throughout programs and infrastructure, numerous productive attacks are owing to very poor hygiene and a absence of simple regulate implementation,” Google’s Cybersecurity Action Workforce (CAT) outlined as part of its recent Danger Horizons report released previous 7 days.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
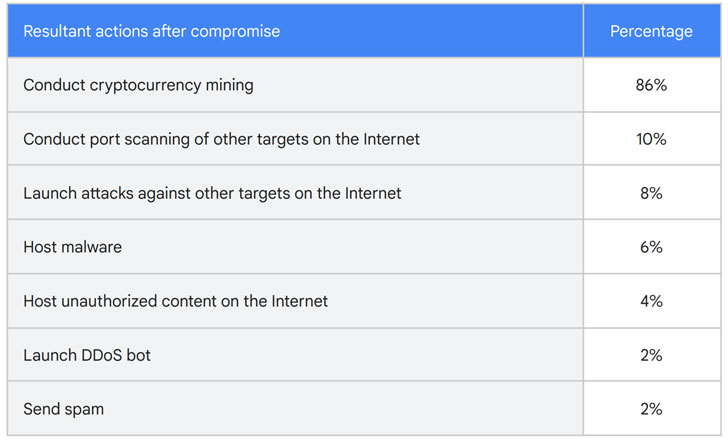
Of the 50 not too long ago compromised GCP circumstances, 86% of them ended up made use of to conduct cryptocurrency mining, in some situations inside of 22 seconds of thriving breach, even though 10% of the circumstances were being exploited to conduct scans of other publicly accessible hosts on the Internet to identify vulnerable methods, and 8% of the occasions had been employed to strike other entities. About 6% of the GCP situations have been utilized to host malware.
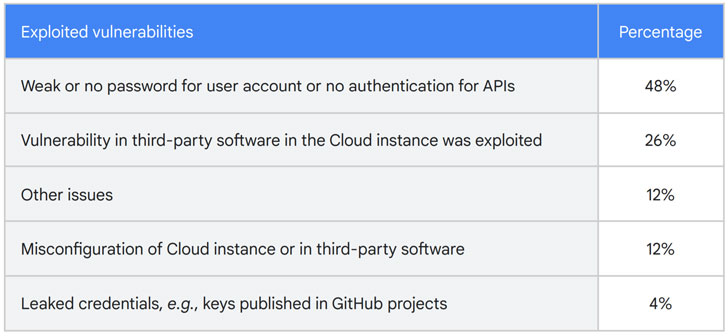
In most cases, the unauthorized obtain was attributed to the use of weak or no passwords for consumer accounts or API connections (48%), vulnerabilities in 3rd-party program mounted on the cloud situations (26%), and leakage of qualifications in GitHub projects (4%).
A further attack of notice was a Gmail phishing campaign introduced by APT28 (aka Fancy Bear) to the close of September 2021 that involved sending an email blast to in excess of 12,000 account holders principally in the U.S., U.K., India, Canada, Russia, Brazil, and the E.U. nations with the goal of stealing their qualifications.
Furthermore, Google CAT stated it observed adversaries abusing absolutely free Cloud credits by utilizing demo projects and posing as bogus startups to interact in site visitors pumping to YouTube. In a different incident, a North Korean government-backed attacker team masqueraded as Samsung recruiters to send out bogus occupation opportunities to staff members at many South Korean information and facts security providers that promote anti-malware options.

“The e-mails incorporated a PDF allegedly boasting to be of a career description for a job at Samsung however, the PDFs have been malformed and did not open up in a conventional PDF reader,” the scientists explained. “When targets replied that they could not open the position description, attackers responded with a destructive website link to malware purporting to be a ‘Secure PDF Reader’ saved in Google Generate which has now been blocked.”
Google connected the attacks to the similar danger actor that formerly set its sights on security specialists operating on vulnerability investigate and advancement earlier this calendar year to steal exploits and phase further attacks on susceptible targets of their alternative.
“Cloud-hosted methods have the gain of substantial availability and ‘anywhere, anytime’ obtain,” Google CAT reported. “Although cloud-hosted means streamline workforce functions, lousy actors can consider to consider benefit of the ubiquitous nature of the cloud to compromise cloud means. Even with escalating public focus to cybersecurity, spear-phishing and social engineering practices are regularly thriving.”
Discovered this article exciting? Stick to THN on Facebook, Twitter and LinkedIn to go through extra special information we put up.
Some areas of this post are sourced from:
thehackernews.com


 Two Drug Dealers Get 18 Years Following EncroChat Bust
Two Drug Dealers Get 18 Years Following EncroChat Bust