GitHub has set out an advisory detailing what may well be an ongoing phishing campaign targeting its users to steal qualifications and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform.
The Microsoft-owned code hosting company said it learned of the attack on September 16, 2022, introducing the campaign impacted “a lot of target companies.”
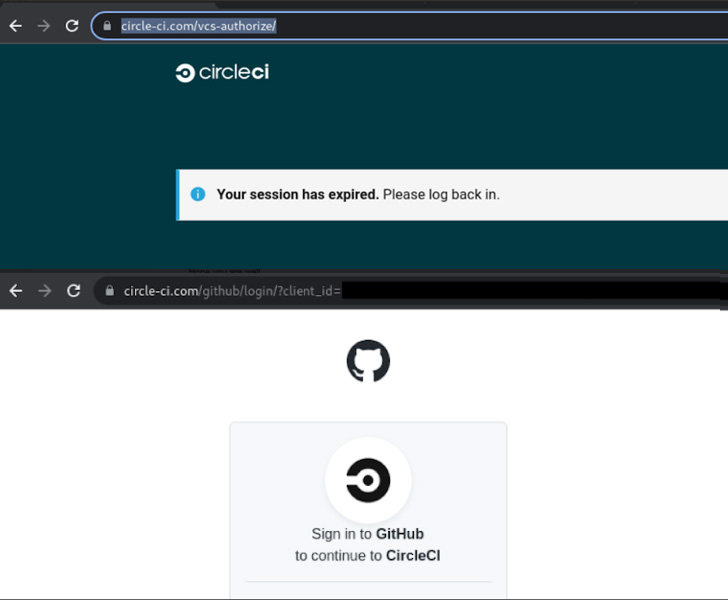
The fraudulent messages declare to notify buyers that their CircleCI classes have expired and that they ought to log in applying GitHub credentials by clicking on a url.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

A further bogus email unveiled by CircleCI prompts customers to sign in to their GitHub accounts to take the company’s new Phrases of Use and Privacy Policy by subsequent the link embedded in the information.
Irrespective of the lure, undertaking so redirects the target to a lookalike GitHub login web page built to steal and exfiltrate the entered qualifications as effectively as the Time-based mostly One particular Time Password (TOTP) codes in real-time to the attacker, effectively enabling a 2FA bypass.
“Accounts shielded by components security keys are not vulnerable to this attack,” GitHub’s Alexis Wales reported.
Amongst other techniques embraced by the menace actor upon gaining unauthorized accessibility to the user account include things like producing GitHub own accessibility tokens (PATs), authorizing OAuth applications, or introducing SSH keys to retain obtain even following a password improve.

The attacker has also been spotted downloading non-public repository contents, and even building and including new GitHub accounts to an business should the compromised account have group administration permissions.
GitHub explained it has taken techniques to reset passwords and take away maliciously-extra qualifications for impacted end users, along with notifying those impacted and suspending the actor-controlled accounts. It did not disclose the scale of the attack.
The organization is further more urging companies to think about employing phishing-resistant hardware security keys to avert these attacks.
The hottest phishing attack comes a minor more than 5 months just after GitHub endured a very specific marketing campaign that resulted in the abuse of 3rd-party OAuth consumer tokens taken care of by Heroku and Travis CI to download private repositories.
Located this report exciting? Stick to THN on Fb, Twitter and LinkedIn to go through extra special material we publish.
Some sections of this report are sourced from:
thehackernews.com


 Details of Over 300,000 Russian Reservists Leaked, Anonymous Claims
Details of Over 300,000 Russian Reservists Leaked, Anonymous Claims