Raccoon Stealer is again on the news once more. US officers arrested Mark Sokolovsky, one particular of the malware actors driving this software. In July 2022, soon after quite a few months of the shutdown, a Raccoon Stealer V2 went viral. Final 7 days, the Division of Justice’s press launch mentioned that the malware gathered 50 million qualifications.
This report will give a brief guideline to the newest facts stealer’s model.
What is Raccoon infostealer V2?
Raccoon Stealer is a sort of malware that steals different info from an infected computer system. It is really really a standard malware, but hackers have designed Raccoon well-known with great services and simple navigation.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In 2019, Raccoon infostealer was a single of the most reviewed malware. In trade for $75 per week and $200 per month, cybercriminals marketed this easy but adaptable info stealer as a MaaS. The malware was effective in attacking a selection of units. In March 2022, on the other hand, menace authors ceased to work.
An up-to-date edition of this malware was unveiled in July 2022. As a consequence, Raccoon Stealer V2 has absent viral and acquired a new identify – RecordBreaker.
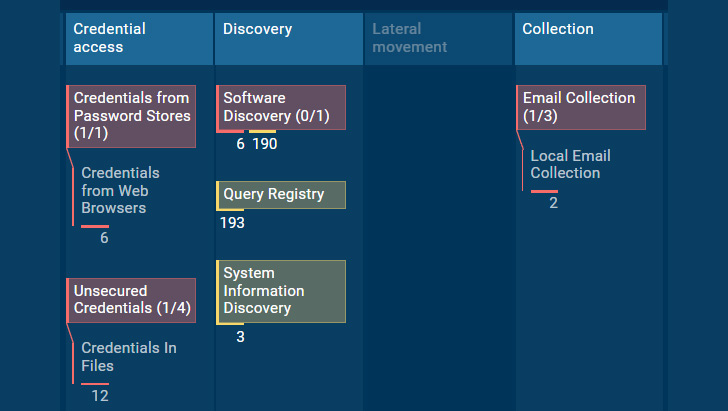 Raccoon v2’s strategies & tactics in ANY.Operate Sandbox
Raccoon v2’s strategies & tactics in ANY.Operate Sandbox
How to review Raccoon stealer V2
Execution method
What Raccoon malware does
Downloads WinAPI libraries
Makes use of kernel32.dll!LoadLibraryW
Receives WinAPI functions’ addresses
Utilizes kernel32.dll!GetProcAddress
Strings and C2 servers encryption
Encrypts with RC4 or XOR algorithm, can be no encryption at all, or combination of diverse selection
Crash triggers
CIS countries locale, mutex
Procedure/LocalSystem stage privilege look at
Works by using Advapi32.dll!GetTokenInformation and Advapi32.dll!ConvertSidToStringSidW comparing StringSid with L “S-1-5-18”
Approach enumeration
Works by using the TlHelp32 API (kernel32.dll!CreateToolhelp32Snapshot to capture procedures and kernel32.dll!Procedure321st / kernel32.dll!Procedure32Next).
Connecting to C2 servers
Results in a string: machineId=machineguid|username&configId=rc4_c2_key
Then sends a Publish request
User and program information collection
- the OS bitness
- data about RAM, CPU
- purposes installed in the program
- cookies
- autofill facts
- autofill variety information
Sending of gathered facts
Submit requests to C2.
Having an solution from the C2
C2 sends “been given”
Finishing functions
Can take a screenshot(s), releases the remaining allocated resources, unloads the libraries, and finishes its perform
We have triaged several Raccoon stealer V2 samples, collected normal habits pursuits, and briefly explained its execution method.
Browse deeper and a lot more comprehensive Raccoon stealer 2. malware analysis. In the report, you can observe all techniques and get a entire photograph of the data stealer’s behavior. Other than this profound exploration, you get a prospect to extract malware configuration by yourselves – copy the Python script of Raccoon stealer and unpack memory dumps to extract C&C servers and keys.
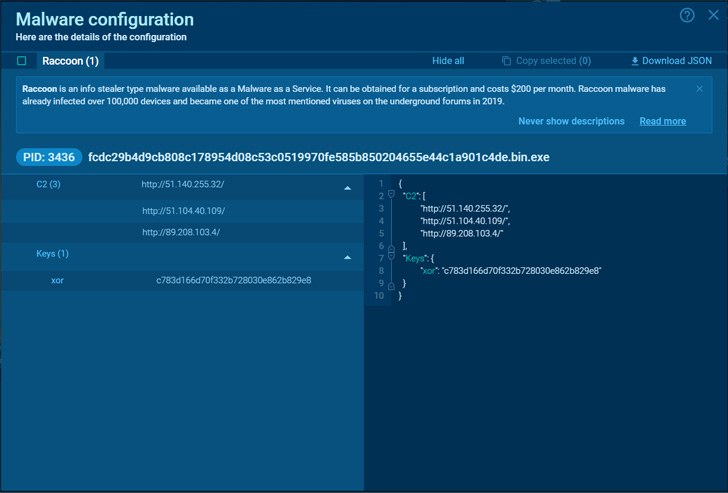 Raccoon v2 malware configuration
Raccoon v2 malware configuration
The place to assess malware
Do you want to review malicious data files and backlinks? There is a rapidly and quick alternative: get all set-manufactured configurations in ANY.Run on line malware sandbox and look into suspicious data files inside and out. Attempt to crack any malware making use of an interactive tactic:
Publish the “HACKERNEWS” promo code at [email protected] utilizing your organization email tackle and get 14 days of ANY.Run quality subscription for free of charge!
The ANY.Operate sandbox lets you assess malware swiftly, navigate by means of the analysis procedure conveniently, detect even advanced malware, and get specific reviews. Use sensible tools and hunt malware successfully.
Located this report appealing? Comply with THN on Fb, Twitter and LinkedIn to go through much more special content we article.
Some areas of this report are sourced from:
thehackernews.com

 Cisco announces Duo Passwordless Authentication for Single Sign On (SSO) apps
Cisco announces Duo Passwordless Authentication for Single Sign On (SSO) apps