Microsoft on Tuesday verified that the LAPSUS$ extortion-focused hacking crew had obtained “minimal entry” to its techniques, as authentication solutions supplier Okta revealed that just about 2.5% of its clients have been perhaps impacted in the wake of the breach.
“No customer code or details was included in the observed actions,” Microsoft’s Danger Intelligence Middle (MSTIC) explained, incorporating that the breach was facilitated by signifies of a single compromised account that has considering that been remediated to avoid additional malicious exercise.
The Windows maker, which was by now tracking the team underneath the moniker DEV-0537 prior to the community disclosure, said it “does not rely on the secrecy of code as a security measure and viewing resource code does not lead to elevation of risk.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This public disclosure escalated our action letting our crew to intervene and interrupt the actor mid-procedure, limiting broader effects,” the company’s security teams observed.
Identity and accessibility administration firm Okta, which also acknowledged the breach by means of the account of a customer aid engineer functioning for a 3rd-party company, claimed that the attackers had obtain to the engineer’s laptop computer for the duration of a 5-working day window between January 16 and 21, but that the assistance by itself was not compromised.
The San Francisco-dependent cloud computer software organization also mentioned it can be identified the affected prospects and that it is speaking to them immediately, stressing that the “Okta provider is completely operational, and there are no corrective actions our prospects need to choose.”
“In the scenario of the Okta compromise, it would not suffice to just adjust a user’s password,” web infrastructure corporation Cloudflare said in a write-up mortem assessment of the incident. “The attacker would also will need to change the components (FIDO) token configured for the same person. As a final result, it would be straightforward to location compromised accounts centered on the associated hardware keys.”
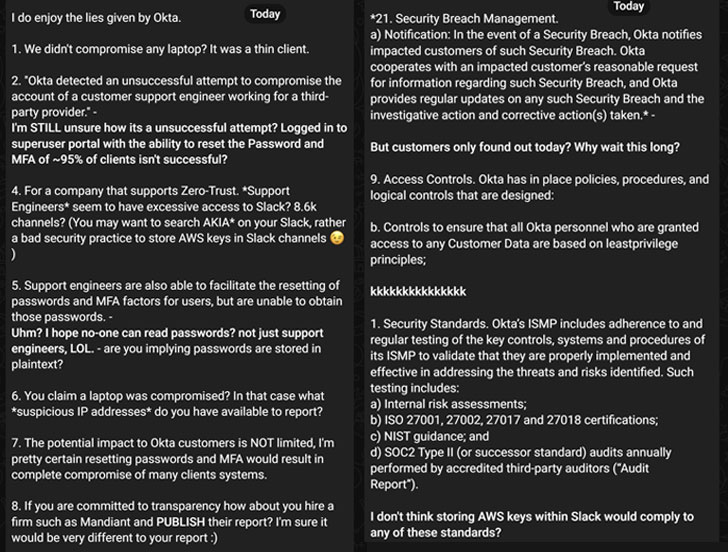
That reported, of individual concern is the fact that Okta failed to publicly disclose the breach for two months, prompting the cyber legal team to question “Why wait around this prolonged?” in its counter assertion.
LAPSUS$ has also claimed in its rebuttal that Okta was storing Amazon Web Services (AWS) keys inside Slack and that support engineers seem to have “extreme access” to the communications system. “The possible affect to Okta buyers is NOT confined, I am really sure resetting passwords and MFA would final result in comprehensive compromise of lots of clients’ units,” the gang elaborated.
Microsoft Exposes the Methods of LAPSUS$
LAPSUS$, which 1st emerged in July 2021, has been on a hacking spree in latest months, targeting a wealth of companies over the intervening time period, such as Impresa, Brazil’s Ministry of Overall health, Claro, Embratel, NVIDIA, Samsung, Mercado Libre, Vodafone, and most recently Ubisoft.
The economically determined group’s modus operandi has been fairly easy: split into a target’s network, steal delicate knowledge, and blackmail the target enterprise into spending up by publicizing snippets of the stolen facts on their Telegram channel.
Microsoft explained LAPSUS$ as a group adhering to a “pure extortion and destruction design without the need of deploying ransomware payloads” and a single that “does not appear to be to deal with its tracks.”
Other techniques adopted by the crew include things like phone-dependent social engineering strategies these types of as SIM-swapping to facilitate account takeover, accessing personalized email accounts of personnel at target companies, bribing workers, suppliers, or small business associates of providers for accessibility, and intruding in the ongoing crisis-response phone calls of their targets to initiate extortion calls for.
LAPSUS$ has also been observed deploying the RedLine Stealer which is out there for sale on underground discussion boards to get hold of passwords and session tokens, in addition to acquiring qualifications and access tokens from dark web marketplaces as perfectly as seeking public code repositories for exposed qualifications, to gain an original foothold.
“The goal of DEV-0537 actors is to get elevated accessibility via stolen credentials that allow knowledge theft and destructive attacks versus a focused organization, generally resulting in extortion,” the enterprise mentioned. “Methods and aims indicate this is a cybercriminal actor motivated by theft and destruction.”
Pursuing initial entry, the group is acknowledged to exploit unpatched vulnerabilities on internally available Confluence, JIRA, and GitLab servers for privilege escalation, prior to proceeding to exfiltrate appropriate info and delete the target’s techniques and methods.
To mitigate such incidents, Microsoft is recommending organizations to mandate multi-factor authentication (but not SMS-centered), leverage modern day authentication possibilities such as OAuth or SAML, review personal indicator-ins for symptoms of anomalous activity, and monitor incident reaction communications for unauthorized attendees.
“Dependent on observed exercise, this group understands the interconnected nature of identities and rely on relationships in modern-day technology ecosystems and targets telecommunications, technology, IT providers and help companies – to leverage their accessibility from a person organization to accessibility the lover or supplier companies.”
Amidst the fallout from the leaks, LAPSUS$ surface to be using a split. “A number of of our associates has [sic] a vacation until 30/3/2022. We could possibly be tranquil for some instances [sic],” the team stated on its Telegram channel.
Identified this report attention-grabbing? Abide by THN on Facebook, Twitter and LinkedIn to browse extra unique material we post.
Some components of this short article are sourced from:
thehackernews.com




 Lapsus$ Data Kidnappers Claim Snatches From Microsoft, Okta
Lapsus$ Data Kidnappers Claim Snatches From Microsoft, Okta