Specifics have been disclosed about a now-addressed critical vulnerability in Microsoft’s Azure Automation services that could have permitted unauthorized obtain to other Azure purchaser accounts and choose in excess of regulate.
“This attack could necessarily mean total command more than assets and info belonging to the focused account, dependent on the permissions assigned by the shopper,” Orca Security researcher Yanir Tsarimi explained in a report posted Monday.
The flaw perhaps put numerous entities at risk, such as an unnamed telecommunications corporation, two automobile brands, a banking conglomerate, and large four accounting firms, among others, the Israeli cloud infrastructure security enterprise additional.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Azure Automation service makes it possible for for course of action automation, configuration administration, and managing running method updates within just a outlined servicing window throughout Azure and non-Azure environments.
Dubbed “AutoWarp,” the issue influences all people of the Azure Automation company that have the Managed Identity function turned on. It can be truly worth noting that this function is enabled by default. Pursuing responsible disclosure on December 6, 2021, the issue was remediated in a patch pushed on December 10, 2021.
“Azure Automation accounts that applied Managed Identities tokens for authorization and an Azure Sandbox for position runtime and execution were uncovered,” Microsoft Security Reaction Center (MSRC) said in a statement. “Microsoft has not detected proof of misuse of tokens.”
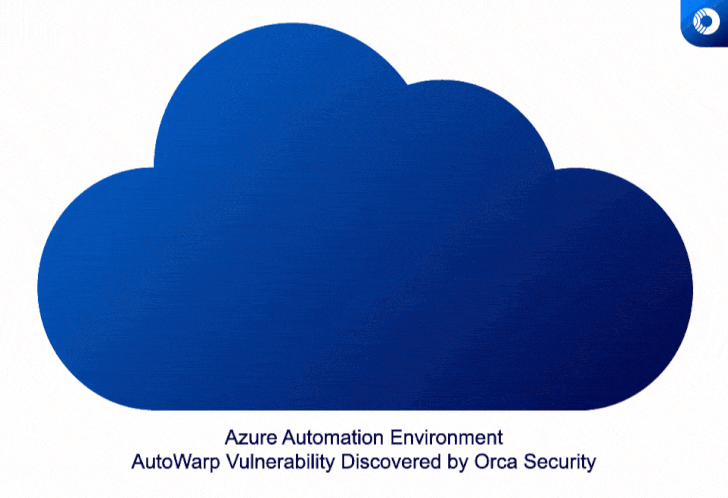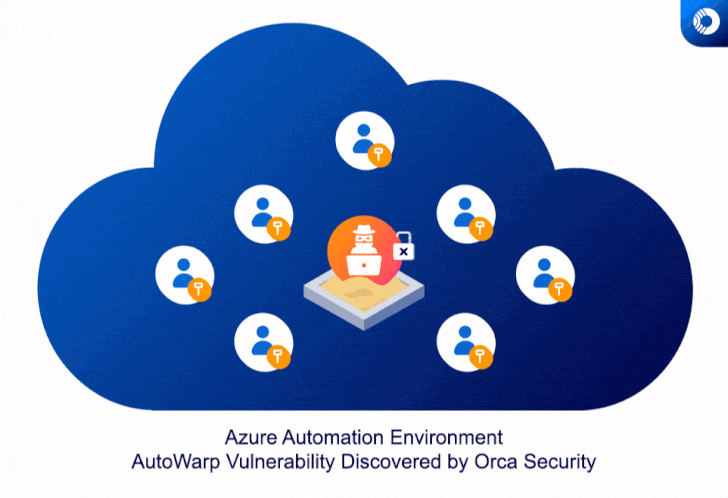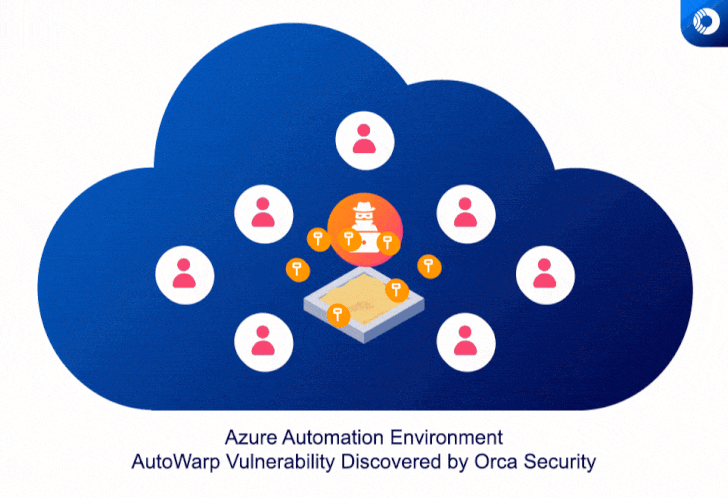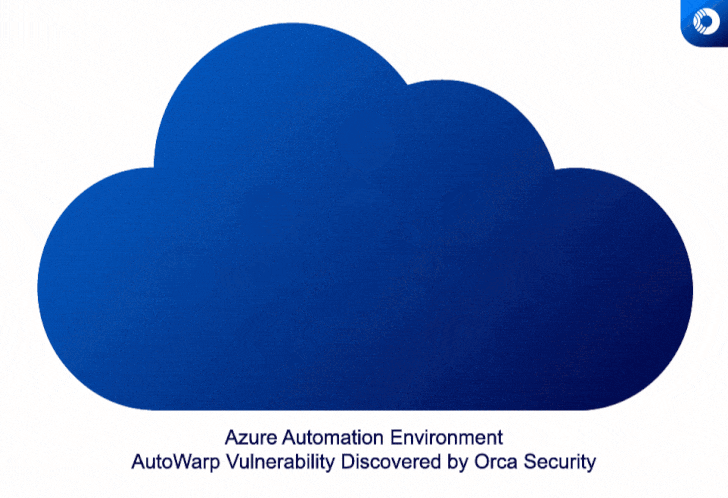
Although the automation work opportunities are built to be isolated by means of a sandbox to avert access by other code operating on the exact digital equipment, the vulnerability built it possible for a bad actor executing a occupation in an Azure Sandbox to get the authentication tokens of other automation jobs.
“Anyone with destructive intentions could’ve consistently grabbed tokens, and with every token, widen the attack to extra Azure shoppers,” Tsarimi noted.
The disclosure comes practically two months following Amazon Web Expert services (AWS) mounted two vulnerabilities – dubbed Superglue and BreakingFormation – in the AWS Glue and CloudFormation services that could have been abused to obtain knowledge of other AWS Glue shoppers and leak delicate files.
In December 2021, Microsoft also fixed an additional security weakness in the Azure Application Provider that resulted in the exposure of supply code of consumer purposes composed in Java, Node, PHP, Python, and Ruby for at minimum 4 several years considering the fact that September 2017.
Discovered this write-up interesting? Follow THN on Facebook, Twitter and LinkedIn to study more exceptional information we submit.
Some sections of this article are sourced from:
thehackernews.com




 Novel Attack Turns Amazon Devices Against Themselves
Novel Attack Turns Amazon Devices Against Themselves