The Chinese-backed Hafnium hacking team has been joined to a piece of a new malware that’s made use of to preserve persistence on compromised Windows environments.
The menace actor is claimed to have focused entities in the telecommunication, internet services service provider and information products and services sectors from August 2021 to February 2022, increasing from the original victimology patterns noticed during its attacks exploiting the then zero-working day flaws in Microsoft Exchange Servers in March 2021.
Microsoft Menace Intelligence Center (MSTIC), which dubbed the defense evasion malware “Tarrask,” characterized it as a instrument that makes “hidden” scheduled duties on the process. “Scheduled process abuse is a really prevalent method of persistence and defense evasion — and an attractive a single, at that,” the scientists said.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Hafnium, whilst most notable for Trade Server attacks, has considering the fact that leveraged unpatched zero-day vulnerabilities as first vectors to fall web shells and other malware, like Tarrask, which produces new registry keys within two paths Tree and Duties upon the development of new scheduled tasks –
- HKEY_Community_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionScheduleTaskCacheTreeTASK_Name
- HKEY_Neighborhood_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionScheduleTaskCacheTasksGUID
“In this circumstance, the danger actor made a scheduled task named ‘WinUpdate’ via HackTool:Acquire64/Tarrask in get to re-set up any dropped connections to their command-and-regulate (C&C) infrastructure,” the scientists claimed.
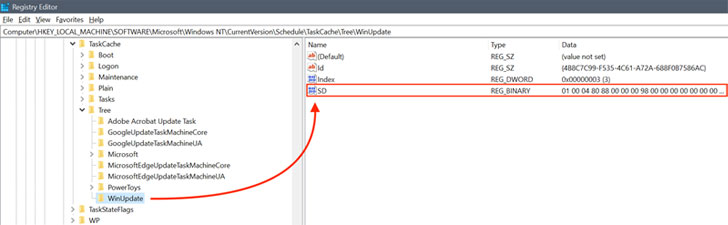
“This resulted in the creation of the registry keys and values explained in the previously portion, nevertheless, the menace actor deleted the [Security Descriptor] price in the Tree registry path.” A security descriptor (aka SD) defines obtain controls for operating the scheduled task.
But by erasing the SD worth from the aforementioned Tree registry route, it successfully potential customers to the activity concealed from the Windows Process Scheduler or the schtasks command-line utility, until manually examined by navigating to the paths in the Registry Editor.
“The attacks […] signify how the risk actor Hafnium shows a distinctive comprehending of the Windows subsystem and makes use of this skills to mask pursuits on specific endpoints to keep persistence on influenced techniques and cover in plain sight,” the researchers reported.
Uncovered this article fascinating? Adhere to THN on Fb, Twitter and LinkedIn to examine far more distinctive content we write-up.
Some areas of this report are sourced from:
thehackernews.com


 Authorities finally confirm leading hacker platform RaidForums has been seized
Authorities finally confirm leading hacker platform RaidForums has been seized