A acquiring menace activity cluster has been located applying Google Ads in one particular of its strategies to distribute numerous write-up-compromise payloads, which include the just lately found out Royal ransomware.
Microsoft, which spotted the updated malware delivery approach in late Oct 2022, is tracking the team underneath the title DEV-0569.
“Observed DEV-0569 attacks present a sample of steady innovation, with typical incorporation of new discovery methods, defense evasion, and several publish-compromise payloads, along with escalating ransomware facilitation,” the Microsoft Security Threat Intelligence group explained in an examination.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The risk actor is regarded to depend on malvertising to point unsuspecting victims to malware downloader links that pose as computer software installers for authentic apps like Adobe Flash Player, AnyDesk, LogMeIn, Microsoft Teams, and Zoom.
The malware downloader, a pressure referred to as BATLOADER, is a dropper that functions as a conduit to distribute upcoming-stage payloads. It has been observed to share overlaps with an additional malware termed ZLoader.
A latest examination of BATLOADER by eSentire and VMware termed out the malware’s stealth and persistence, in addition to its use of search engine optimization (Search engine marketing) poisoning to entice users to download the malware from compromised internet sites or attacker-developed domains.
Alternatively, phishing links are shared through spam emails, fake discussion board webpages, site comments, and even speak to varieties existing on specific organizations’ internet websites.
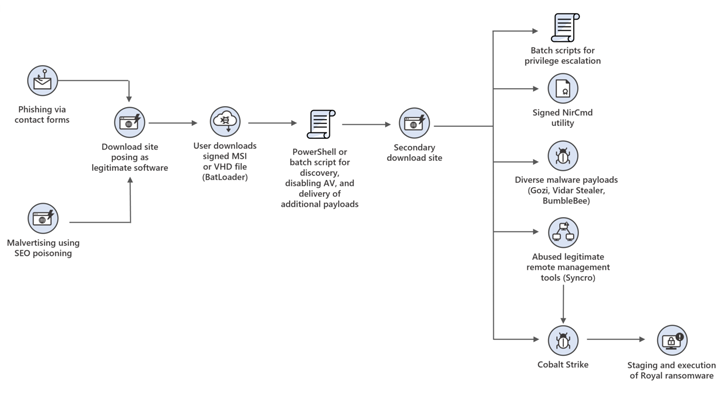
“DEV-0569 has utilised different an infection chains utilizing PowerShell and batch scripts that finally led to the obtain of malware payloads like information and facts stealers or a genuine remote administration software applied for persistence on the network,” the tech large pointed out.
“The administration instrument can also be an obtain stage for the staging and unfold of ransomware.”
Also utilized is a instrument known as NSudo to start systems with elevated privileges and impair defenses by including registry values that are made to disable antivirus alternatives.
The use of Google Advertisements to deliver BATLOADER selectively marks a diversification of the DEV-0569’s distribution vectors, enabling it to access more targets and supply malware payloads, the enterprise pointed out.
It more positions the group to provide as an original entry broker for other ransomware operations, signing up for the likes of malware these as Emotet, IcedID, Qakbot.
“Because DEV-0569’s phishing scheme abuses authentic services, organizations can also leverage mail stream regulations to seize suspicious keyword phrases or evaluate wide exceptions, such as these relevant to IP ranges and area-amount let lists,” Microsoft claimed.
Observed this article attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to browse extra exclusive information we publish.
Some pieces of this posting are sourced from:
thehackernews.com


 Chinese ‘Mustang Panda’ Hackers Actively Targeting Governments Worldwide
Chinese ‘Mustang Panda’ Hackers Actively Targeting Governments Worldwide