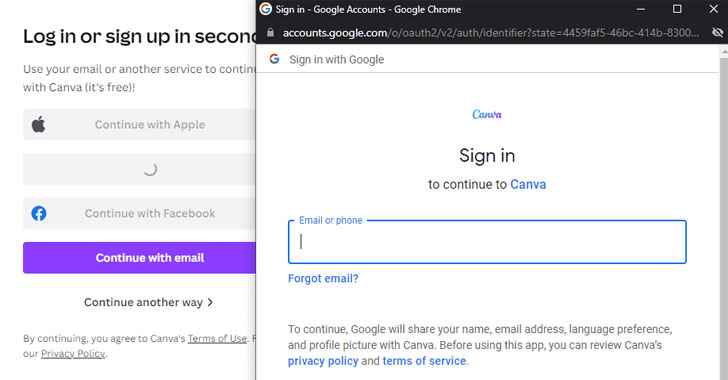
A novel phishing method termed browser-in-the-browser (BitB) attack can be exploited to simulate a browser window inside of the browser in purchase to spoof a authentic area, thus generating it achievable to phase convincing phishing attacks.
In accordance to penetration tester and security researcher, who goes by the handle mrd0x_, the process normally takes benefit of 3rd-party single indication-on (SSO) options embedded on internet sites this kind of as “Sign in with Google” (or Fb, Apple, or Microsoft).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Though the default actions when a user makes an attempt to indicator in by using these techniques is to be greeted by a pop-up window to total the authentication system, the BitB attack aims to replicate this full approach employing a combine of HTML and CSS code to develop an completely fabricated browser window.
“Blend the window style with an iframe pointing to the malicious server hosting the phishing webpage, and it can be essentially indistinguishable,” mrd0x_ mentioned in a technical produce-up published previous 7 days. “JavaScript can be easily utilized to make the window show up on a url or button click, on the page loading and so on.”
Although this process noticeably makes it less complicated to mount successful social engineering campaigns, it is well worth noting that possible victims have to have to be redirected to a phishing domain that can display screen such a phony authentication window for credential harvesting.
“But after landed on the attacker-owned website, the consumer will be at simplicity as they type their credentials away on what appears to be the authentic web-site (for the reason that the trusted URL states so),” mrd0x_ added.
Uncovered this post appealing? Abide by THN on Facebook, Twitter and LinkedIn to examine much more exclusive information we article.
Some components of this post are sourced from:
thehackernews.com




 Ransomware strikes Scottish mental health charity
Ransomware strikes Scottish mental health charity