A new info-stealing malware has set its sights on Apple’s macOS functioning method to siphon sensitive information and facts from compromised devices.
Dubbed MacStealer, it truly is the latest case in point of a threat that makes use of Telegram as a command-and-handle (C2) platform to exfiltrate information. It mostly affects gadgets working macOS versions Catalina and later on operating on M1 and M2 CPUs.
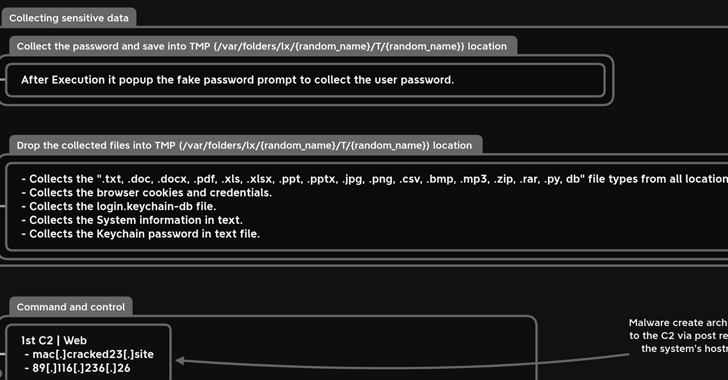
“MacStealer has the skill to steal documents, cookies from the victim’s browser, and login information,” Uptycs scientists Shilpesh Trivedi and Pratik Jeware explained in a new report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
First marketed on on the web hacking message boards at the start out of the thirty day period, it is still a operate in development, with the malware authors planning to incorporate functions to seize details from Apple’s Safari browser and the Notes application.
In its present-day form, MacStealer is made to extract iCloud Keychain knowledge, passwords and credit rating card facts from browsers like Google Chrome, Mozilla Firefox, and Brave. It also characteristics help for harvesting Microsoft Business information, photographs, archives, and Python scripts.
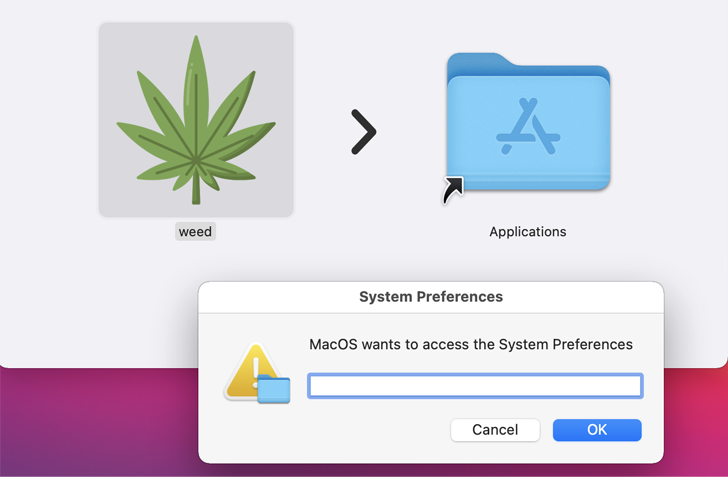
The specific technique utilized to supply the malware is not recognised, but it is propagated as a DMG file (weed.dmg) that, when executed, opens a pretend password prompt to harvest the passwords under the guise of trying to find entry to the Technique Configurations application.
MacStealer is just one of quite a few information-stealers that have surfaced just around the earlier number of months and provides to an currently massive selection of equivalent tools presently in the wild.
This also contains a further piece of new C#-dependent malware termed HookSpoofer that’s influenced by StormKitty and will come with keylogging and clipper qualities and transmits the stolen info to a Telegram bot.
A different browser cookie-thieving malware of note is Ducktail, which also utilizes a Telegram bot to exfiltrate data and re-emerged in mid-February 2023 with improved techniques to sidestep detection.
This involves “switching the original infection from an archive that contains a malicious executable to an archive that contains a malicious LNK file that would start off the infection chain,” Deep Instinct researcher Simon Kenin claimed earlier this month.
WEBINARDiscover the Concealed Risks of Third-Party SaaS Apps
Are you mindful of the threats linked with third-party app obtain to your firm’s SaaS apps? Join our webinar to find out about the varieties of permissions becoming granted and how to lower risk.
RESERVE YOUR SEAT
Stealer malware is generally spread via different channels, like email attachments, bogus application downloads, and other social engineering methods.
To mitigate these threats, it truly is encouraged that people maintain their running system and security program up to date and stay clear of downloading information or clicking back links from unidentified resources.
“As Macs have develop into ever more well-liked in the business amid management and enhancement teams, the additional essential the information stored on them is to attackers,” SentinelOne researcher Phil Stokes explained final 7 days.
Located this post attention-grabbing? Abide by us on Twitter and LinkedIn to study a lot more distinctive information we publish.
Some parts of this report are sourced from:
thehackernews.com

 Microsoft Issues Patch for aCropalypse Privacy Flaw in Windows Screenshot Tools
Microsoft Issues Patch for aCropalypse Privacy Flaw in Windows Screenshot Tools