Risk actors have been discovered deploying never-right before-noticed put up-compromise implants in VMware’s virtualization software to seize handle of infected methods and evade detection.
Google’s Mandiant danger intelligence division referred to it as a “novel malware ecosystem” that impacts VMware ESXi, Linux vCenter servers, and Windows digital devices, making it possible for attackers to keep persistent obtain to the hypervisor as nicely as execute arbitrary commands.
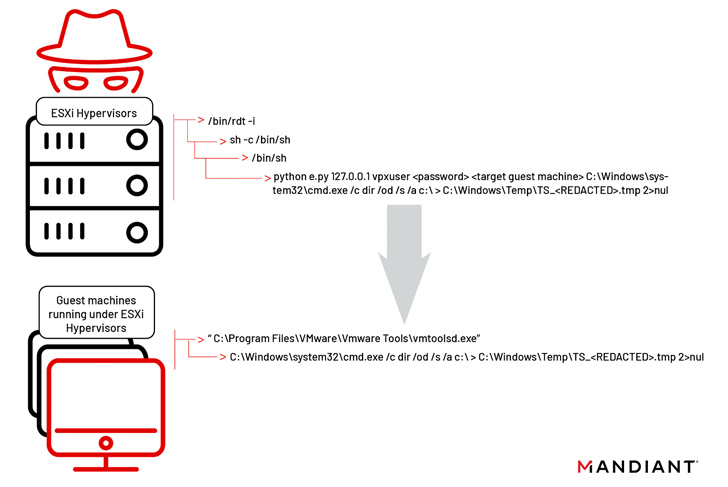
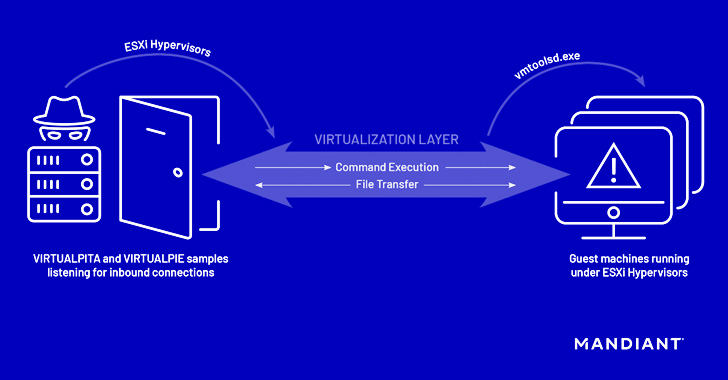
The hyperjacking attacks, for every the cybersecurity seller, included the use of destructive vSphere Set up Bundles (VIBs) to sneak in two implants, dubbed VIRTUALPITA and VIRTUALPIE, on the ESXi hypervisors.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“It is crucial to highlight that this is not an exterior remote code execution vulnerability the attacker wants admin-amount privileges to the ESXi hypervisor ahead of they can deploy malware,” Mandiant scientists Alexander Marvi, Jeremy Koppen, Tufail Ahmed, and Jonathan Lepore explained in an exhaustive two-component report.
There is no proof that a zero-working day vulnerability was exploited to get accessibility to ESXi servers. That claimed, the use of trojanized VIBs, a application package deal format applied to aid computer software distribution and digital device management, details to a new stage of sophistication.
“This malware differs in that it supports remaining both equally persistent and covert, which is consistent with the goals of much larger risk actors and APT teams who goal strategic establishments with the intention of dwelling undetected for some time,” VMware disclosed.
Though VIRTUALPITA arrives with capabilities to execute instructions as very well as have out file add and download, VIRTUALPIE is a Python backdoor with assistance for command line execution, file transfer, and reverse shell features.

Also uncovered is a malware sample called VIRTUALGATE in Windows visitor virtual devices, which is a C-dependent utility program that executes an embedded payload capable of applying VMware’s digital machine interaction interface (VMCI) sockets to operate instructions on a guest virtual machine from a hypervisor host.
Mandiant also warned that the campaign’s methods to get close to common security controls by exploiting virtualization program characterize a new attack floor that’s most likely to be picked up by other hacker teams.
The attacks have been attributed to an uncategorized, rising risk cluster codenamed UNC3886, whose determination is very likely to be espionage-driven contemplating the remarkably specific mother nature of the intrusions. It further assessed with small assurance that UNC3886 has a China-nexus.
Discovered this short article interesting? Observe THN on Fb, Twitter and LinkedIn to browse additional exclusive content we article.
Some parts of this write-up are sourced from:
thehackernews.com

 Microsoft Confirms Two Exchange Zero-Day Vulnerabilities
Microsoft Confirms Two Exchange Zero-Day Vulnerabilities