A new covert Linux kernel rootkit named Syslogk has been noticed beneath growth in the wild and cloaking a malicious payload that can be remotely commandeered by an adversary using a magic network visitors packet.
“The Syslogk rootkit is seriously dependent on Adore-Ng but incorporates new functionalities making the user-manner software and the kernel rootkit difficult to detect,” Avast security researchers David Álvarez and Jan Neduchal reported in a report posted Monday.
Adore-Ng, an open-source rootkit available because 2004, equips the attacker with full manage in excess of a compromised process. It also facilitates hiding processes as effectively as custom malicious artifacts, documents, and even the kernel module, earning it more difficult to detect.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“The module starts off by hooking alone into numerous file methods. It digs up the inode for the root filesystem, and replaces that inode’s readdir() purpose pointer with one particular of its own,” LWN.net mentioned at the time. “The Adore model performs like the a single it replaces, apart from that it hides any documents owned by a certain person and group ID.”
Moreover its abilities to conceal network visitors from utilities like netstat, housed inside of the rootkit is a payload named “PgSD93ql” that is almost nothing but a C-centered compiled backdoor trojan named Rekoobe and gets brought on on getting a magic packet.
“Rekoobe is a piece of code implanted in reputable servers,” the researchers said. “In this case it is embedded in a fake SMTP server, which spawns a shell when it gets a specifically crafted command.”
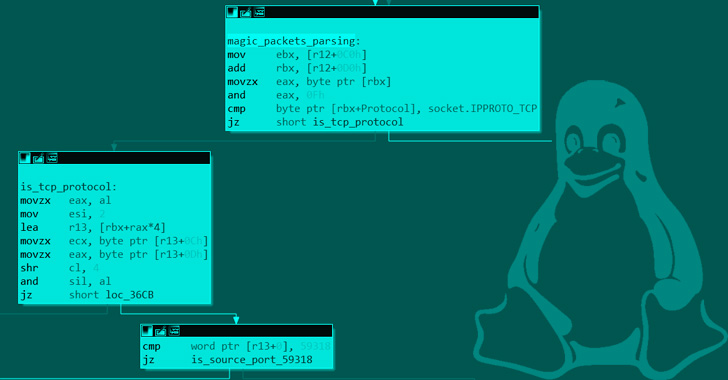
Specially, Syslogk is engineered to examine TCP packets that contains the resource port selection 59318 to start the Rekoobe malware. Halting the payload, on the other hand, calls for the TCP packet to meet the pursuing requirements –
- Reserved discipline of the TCP header is established to 0x08
- Source port is amongst 63400 and 63411 (inclusive)
- Each the desired destination port and the resource deal with are the very same as that were utilized when sending the magic packet to commence Rekoobe, and
- Is made up of a key (“D9sd87JMaij”) that is hardcoded in the rootkit and located in a variable offset of the magic packet

For its part, Rekoobe masquerades as a seemingly innocuous SMTP server but in fact is centered on an open up-source job identified as Little SHell and stealthily incorporates a backdoor command for spawning a shell that will make it feasible to execute arbitrary commands.
Syslogk provides to a developing list of freshly discovered evasive Linux malware these as BPFDoor and Symbiote, highlighting how cyber criminals are progressively focusing on Linux servers and cloud infrastructure to start ransomware campaigns, cryptojacking attacks, and other illicit exercise.
“Rootkits are perilous parts of malware,” the researchers explained. “Kernel rootkits can be difficult to detect and take away because these items of malware operate in a privileged layer.”
Uncovered this report interesting? Abide by THN on Facebook, Twitter and LinkedIn to examine far more exclusive written content we write-up.
Some elements of this write-up are sourced from:
thehackernews.com

 Attack on Kaiser Permanente Exposes Data on 70,000 Customers
Attack on Kaiser Permanente Exposes Data on 70,000 Customers