A North Korean cyberespionage team named Konni has been connected to a series of focused attacks aimed at the Russian Federation’s Ministry of Foreign Affairs (MID) with New Calendar year lures to compromise Windows devices with malware.
“This exercise cluster demonstrates the client and persistent nature of innovative actors in waging multi-phased campaigns versus perceived large-worth networks,” scientists from Lumen Technologies’ Black Lotus Labs reported in an analysis shared with The Hacker News.
The Konni group’s practices, tactics, and treatments (TTPs) are recognized to overlap with menace actors belonging to the broader Kimsuky umbrella, which is also tracked by the cybersecurity neighborhood below the monikers Velvet Chollima, ITG16, Black Banshee, and Thallium.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The most recent attacks concerned the actor getting entry to the focus on networks by way of stolen credentials, exploiting the foothold to load malware for intelligence gathering reasons, with early indicators of the activity documented by MalwareBytes as much again as July 2021.
Subsequent iterations of the phishing marketing campaign are thought to have unfolded in 3 waves — the to start with commencing on Oct 19, 2021 to harvest qualifications from MID personnel, followed by leveraging COVID-19 themed lures in November to put in a rogue model of the Russian-mandated vaccination registration computer software that served as a loader for added payloads.
“The timing of this activity intently aligned with the passage of Russian Vaccine Passport regulations that mandated Russians experienced to obtain a QR code from the governing administration to verify vaccination in order to obtain public locations this sort of as places to eat and bars,” the researchers pointed out.
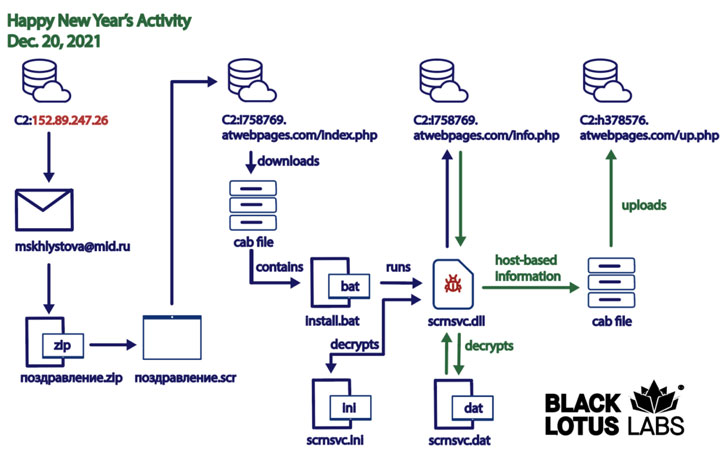
The third attack, also corroborated by Cluster25 earlier this week, began on December 20, 2021, utilizing New Year’s Eve festivities as a spear-phishing theme to set off a multi-phase an infection chain that culminated in the set up of a distant accessibility trojan named Konni RAT.
Particularly, the intrusions transpired by initially compromising the email account belonging to a staff members member of the MID, from which email messages have been sent to at minimum two other MID entities, together with the Russian Embassy in Indonesia and Sergey Alexeyevich Ryabkov, a deputy minister overseeing non-proliferation and arms handle.
The email missives seemingly propagated a “Happy New Year’s” message, only to contain a trojanized screensaver attachment that is designed to retrieve and run up coming-phase executables from a distant server. The remaining phase of the attack is the deployment of the Konni RAT trojan, which conducts reconnaissance of the contaminated machine and exfiltrates the collected details again to the server.
“While this particular marketing campaign was very qualified, it is critical for defenders to have an understanding of the evolving capabilities of advanced actors to realize an infection of coveted targets,” the researcher said, urging organizations to view out for phishing email messages and use multi-factor authentication to safe accounts.
Identified this write-up interesting? Comply with THN on Fb, Twitter and LinkedIn to read a lot more distinctive content material we article.
Some areas of this post are sourced from:
thehackernews.com



 Apple iPhone Malware Tactic Causes Fake Shutdowns to Enable Spying
Apple iPhone Malware Tactic Causes Fake Shutdowns to Enable Spying