A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Perform Shop to compromise users’ gadgets with banking malware.
These 17 dropper applications, collectively dubbed DawDropper by Craze Micro, masqueraded as efficiency and utility apps such as document scanners, QR code audience, VPN companies, and contact recorders, amongst others. All these applications in problem have been eradicated from the app marketplace.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
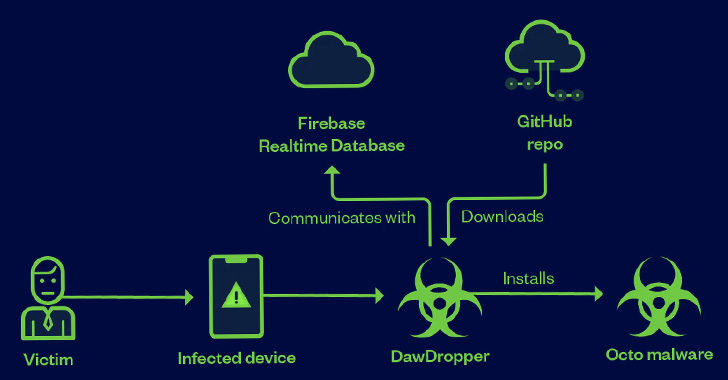
“DawDropper utilizes Firebase Realtime Database, a third-party cloud support, to evade detection and dynamically get hold of a payload down load tackle,” the researchers reported. “It also hosts destructive payloads on GitHub.”
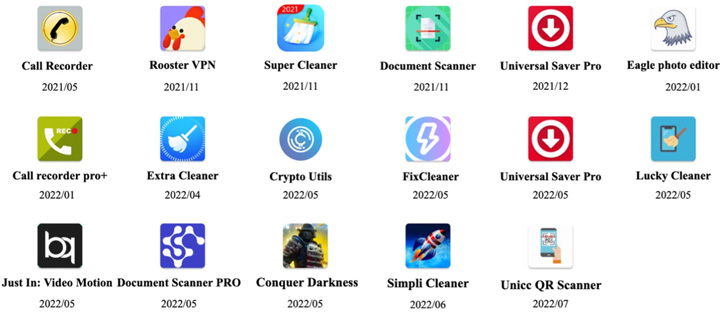
Droppers are applications built to sneak earlier Google’s Participate in Store security checks, adhering to which they are made use of to obtain much more potent and intrusive malware on a system, in this scenario, Octo (Coper), Hydra, Ermac, and TeaBot.
Attack chains involved the DawDropper malware establishing connections with a Firebase Realtime Databases to acquire the GitHub URL important to down load the destructive APK file.
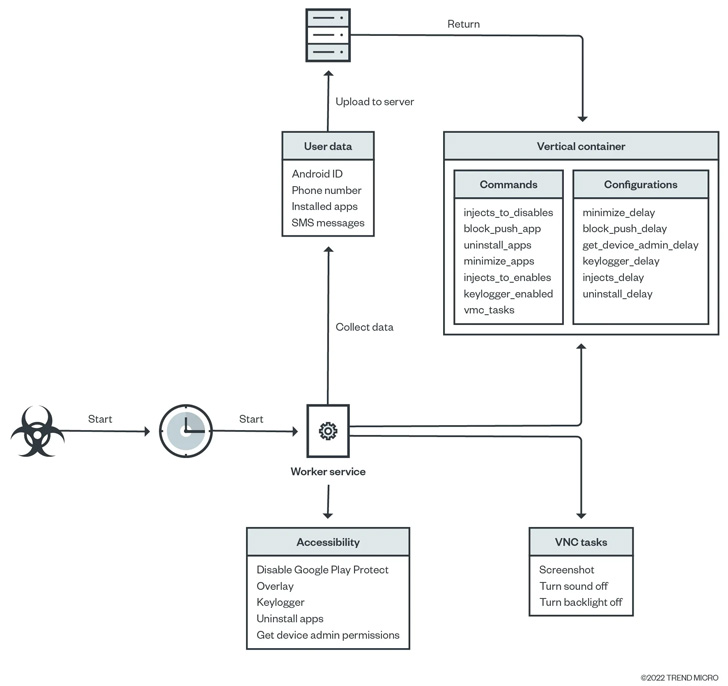
The listing of destructive apps earlier offered from the app retailer is below –
- Contact Recorder APK (com.caduta.aisevsk)
- Rooster VPN (com.vpntool.androidweb)
- Super Cleaner- hyper & good (com.j2ca.callrecorder)
- Doc Scanner – PDF Creator (com.codeword.docscann)
- Common Saver Pro (com.virtualapps.universalsaver)
- Eagle picture editor (com.techmediapro.photoediting)
- Simply call recorder pro+ (com.chestudio.callrecorder)
- Excess Cleaner (com.casualplay.leadbro)
- Crypto Utils (com.utilsmycrypto.mainer)
- FixCleaner (com.cleaner.fixgate)
- Just In: Video clip Motion (com.olivia.openpuremind)
- com.myunique.sequencestore
- com.flowmysequto.yamer
- com.qaz.universalsaver
- Lucky Cleaner (com.luckyg.cleaner)
- Simpli Cleaner (com.scando.qukscanner)
- Unicc QR Scanner (com.qrdscannerratedx)
Incorporated between the droppers is an application named “Unicc QR Scanner” that was formerly flagged by Zscaler before this month as distributing the Coper banking trojan, a variant of the Exobot mobile malware.

Octo is also regarded to disable Google Perform Secure and use digital network computing (VNC) to document a victim device’s display, which include sensitive facts these kinds of as banking credentials, email addresses and passwords, and PINs, all of which are subsequently exfiltrated to a distant server.
Banking droppers, for their component, have developed since the begin of the calendar year, pivoting away from hard-coded payload down load addresses to employing an middleman to conceal the deal with hosting the malware.
“Cybercriminals are continually getting techniques to evade detection and infect as several products as feasible,” the scientists claimed.
“On top of that, mainly because there is a higher need for novel approaches to distribute cell malware, various malicious actors claim that their droppers could enable other cybercriminals disseminate their malware on Google Perform Store, resulting in a dropper-as-a-company (DaaS) model.”
Located this article exciting? Comply with THN on Facebook, Twitter and LinkedIn to study far more distinctive material we article.
Some elements of this posting are sourced from:
thehackernews.com

 IT Pro News In Review: Rise in ransomware attacks, UK & South Korea 5G & 6G, IBM data breach report
IT Pro News In Review: Rise in ransomware attacks, UK & South Korea 5G & 6G, IBM data breach report