The operators of the Purple Fox malware have retooled their malware arsenal with a new variant of a remote obtain trojan identified as FatalRAT, even though also at the same time upgrading their evasion mechanisms to bypass security computer software.
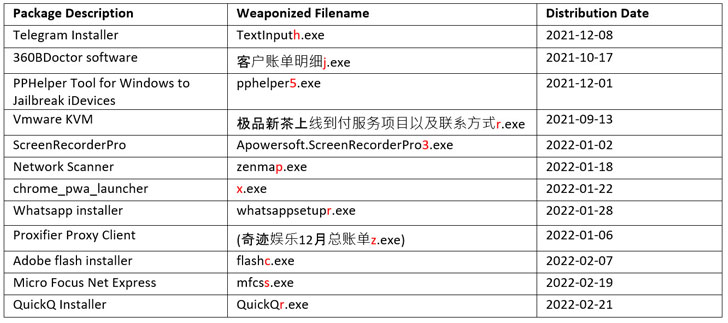
“Users’ devices are qualified by means of trojanized software program packages masquerading as legit application installers,” Development Micro researchers said in a report released on March 25, 2022. “The installers are actively dispersed online to trick customers and boost the overall botnet infrastructure.”


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The results adhere to prior analysis from Minerva Labs that drop light on a related modus operandi of leveraging fraudulent Telegram applications to distribute the backdoor. Other disguised software program installers include things like WhatsApp, Adobe Flash Player, and Google Chrome.
These offers act as a very first-stage loader, triggering an infection sequence that sales opportunities to the deployment of a next-stage payload from a distant server and culminating in the execution of a binary that inherits its attributes from FatalRAT.
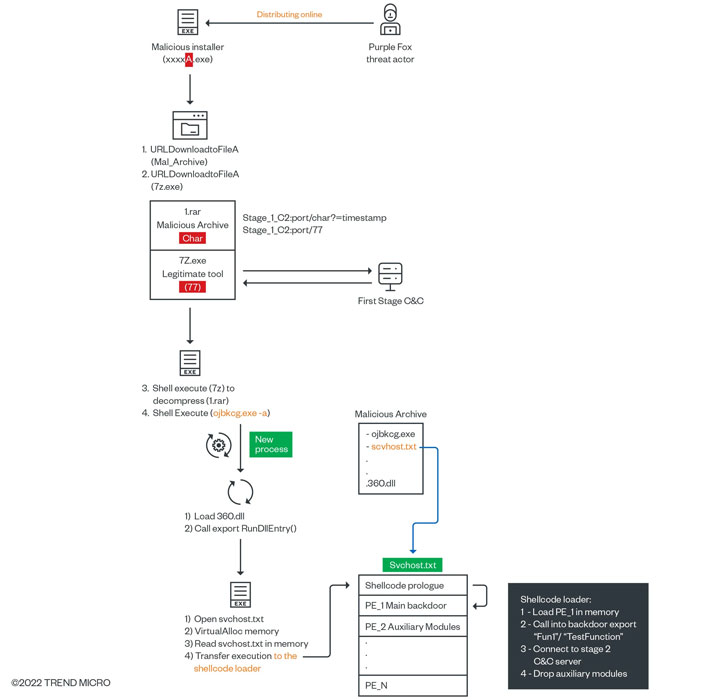
FatalRAT is a C++-centered implant created to run instructions and exfiltrate sensitive details back to a distant server, with the malware authors incrementally updating the backdoor with new functionality.
“The RAT is dependable for loading and executing the auxiliary modules primarily based on checks done on the victim techniques,” the scientists claimed. “Changes can occur if certain [antivirus] brokers are running or if registry keys are identified. The auxiliary modules are meant as guidance for the group’s specific objectives.”
In addition, Purple Fox, which arrives with a rootkit module, arrives with assistance for five diverse instructions, including copying and deleting files from the kernel as well as evading antivirus engines by intercepting calls sent to the file program.
The conclusions also follow latest disclosures from cybersecurity company Avast, which specific a new campaign that included the Purple Fox exploitation framework acting as a deployment channel for a different botnet named DirtyMoe.
“Operators of the Purple Fox botnet are nonetheless active and continually updating their arsenal with new malware, when also upgrading the malware variants they have,” the scientists claimed. “They are also striving to enhance their signed rootkit arsenal for [antivirus] evasion and hoping to bypass detection mechanisms by focusing on them with personalized signed kernel motorists.”
Discovered this short article fascinating? Comply with THN on Facebook, Twitter and LinkedIn to read through more distinctive content material we submit.
Some elements of this article are sourced from:
thehackernews.com



 One in 10 UK Staff Circumvent Corporate Security
One in 10 UK Staff Circumvent Corporate Security