Scientists have disclosed a new severe Oracle Cloud Infrastructure (OCI) vulnerability that could be exploited by consumers to entry the virtual disks of other Oracle prospects.
“Every virtual disk in Oracle’s cloud has a distinctive identifier known as OCID,” Shir Tamari, head of research at Wiz, reported in a series of tweets. “This identifier is not viewed as top secret, and companies do not treat it as such.”
“Given the OCID of a victim’s disk that is not currently hooked up to an lively server or configured as shareable, an attacker could ‘attach’ to it and obtain examine/create about it,” Tamari extra.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The cloud security firm, which dubbed the tenant isolation vulnerability “AttachMe,” stated Oracle patched the issue within 24 hrs of liable disclosure on June 9, 2022.
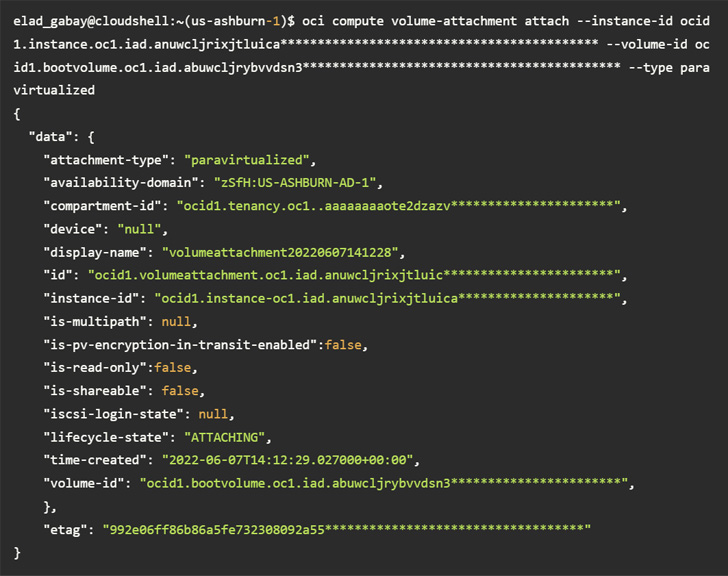 Accessing a volume making use of the CLI without enough permissions
Accessing a volume making use of the CLI without enough permissions
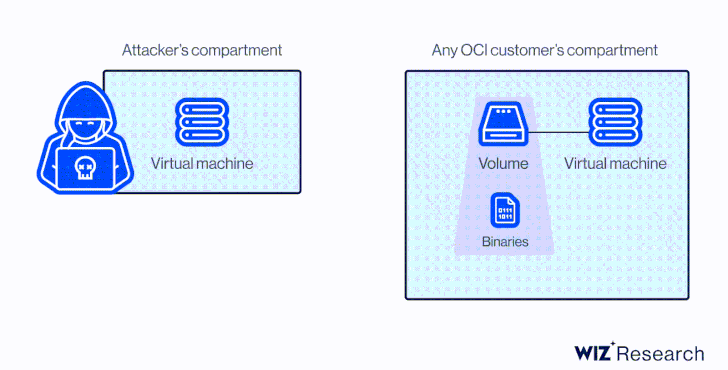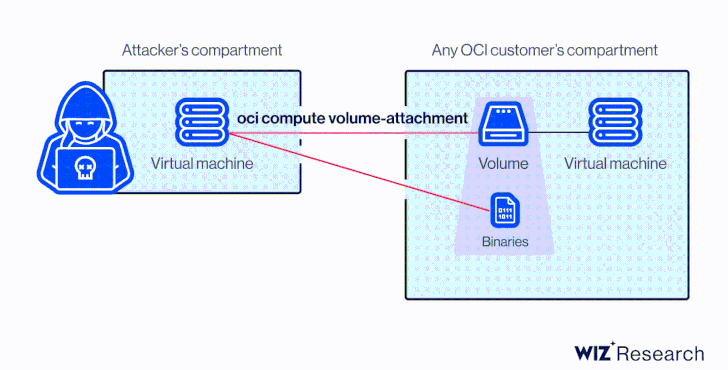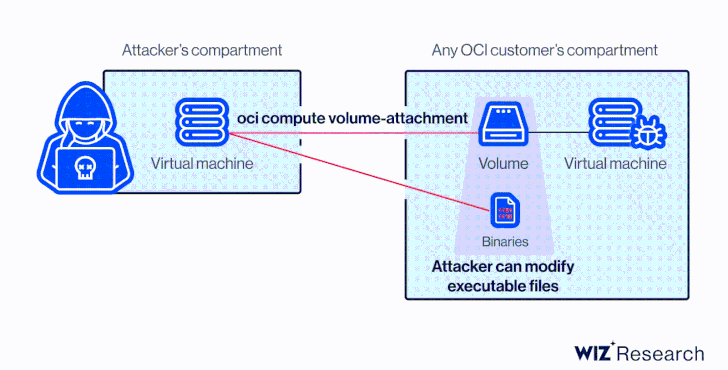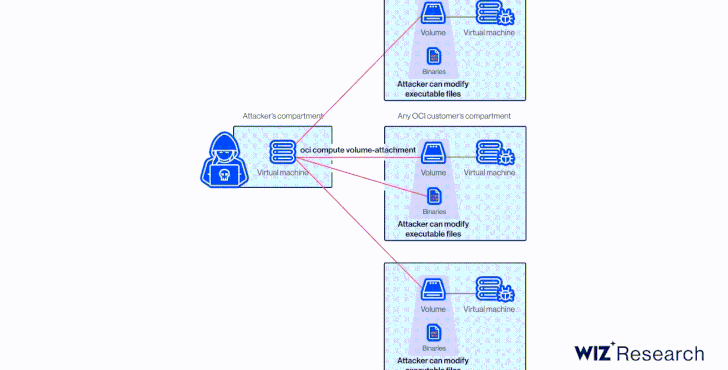
At its core, the vulnerability is rooted in the actuality that a disk could be hooked up to a compute occasion in another account by way of the Oracle Cloud Identifier (OCID) devoid of any specific authorization.
This meant that an attacker in possession of the OCID could have taken edge of AttachMe to accessibility any storage volume, ensuing in knowledge exposure, exfiltration, or worse, alter boot volumes to acquire code execution.
Apart from figuring out the OCID of the concentrate on volume, yet another prerequisite to pull off the attack is that the adversary’s instance have to be in the similar Availability Area (Advertisement) as the goal.

“Insufficient validation of user permissions is a typical bug class amid cloud service suppliers,” Wiz researcher Elad Gabay said. “The best way to establish these issues is by doing rigorous code testimonials and extensive assessments for each individual delicate API in the development stage.”
The results get there nearly 5 months after Microsoft tackled a pair of issues with the Azure Databases for PostgreSQL Versatile Server that could consequence in unauthorized cross-account databases accessibility in a location.
Uncovered this short article attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to browse a lot more unique information we article.
Some components of this posting are sourced from:
thehackernews.com

 Australian telco Optus confirms cyber attack involving potential leak of sensitive customer data
Australian telco Optus confirms cyber attack involving potential leak of sensitive customer data