The internal workings of a cybercriminal group acknowledged as the Wizard Spider have been exposed, shedding mild on its organizational structure and motivations.
“Most of Wizard Spider’s endeavours go into hacking European and U.S. companies, with a particular cracking device employed by some of their attackers to breach substantial-value targets,” Swiss cybersecurity firm PRODAFT said in a new report shared with The Hacker Information. “Some of the cash they get is place again into the job to build new equipment and expertise.”
Wizard Spider, also known as Gold Blackburn, is considered to work out of Russia and refers to a monetarily enthusiastic menace actor that’s been joined to the TrickBot botnet, a modular malware that was formally discontinued before this year in favor of improved malware these kinds of as BazarBackdoor.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
That’s not all. The TrickBot operators have also thoroughly cooperated with Conti, a different Russia-linked cybercrime team infamous for presenting ransomware-as-a-service packages to its affiliate marketers.
Gold Ulrick (aka Grim Spider), as the team liable for the distribution of the Conti (formerly Ryuk) ransomware is known as, has traditionally leveraged preliminary access delivered by TrickBot to deploy the ransomware against focused networks.
“Gold Ulrick is comprised of some or all of the same operators as Gold Blackburn, the menace group responsible for the distribution of malware these kinds of as TrickBot, BazarLoader and Beur Loader,” cybersecurity company Secureworks notes in a profile of the cybercriminal syndicate.
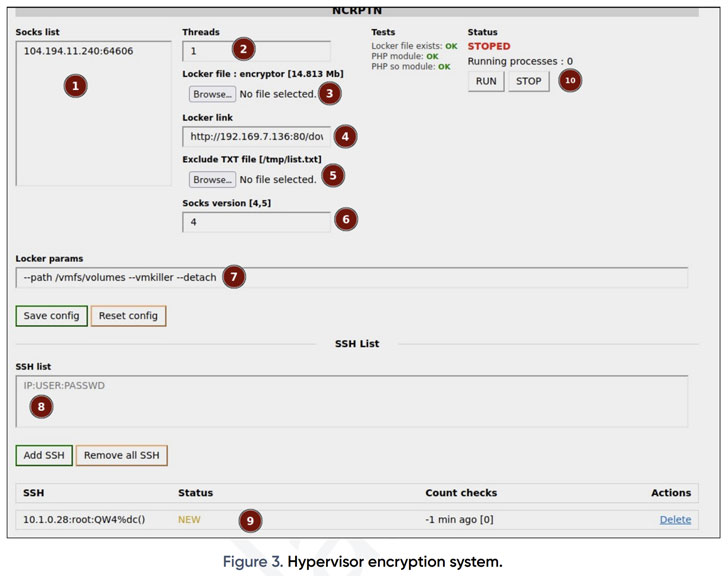
Stating that the team is “able of monetizing numerous factors of its functions,” PRODAFT emphasised the adversary’s capacity to extend its legal enterprise, which it claimed is built doable by the gang’s “incredible profitability.”
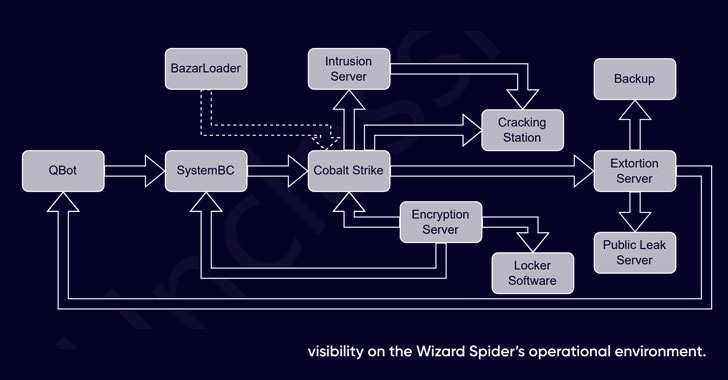
Usual attack chains involving the team start with spam campaigns that distribute malware this kind of as Qakbot (aka QBot) and SystemBC, making use of them as launchpads to drop added applications, including Cobalt Strike for lateral motion, prior to executing the locker software program.
In addition to leveraging a prosperity of utilities for credential theft and reconnaissance, Wizard Spider is regarded to use an exploitation toolkit that can make use of a short while ago disclosed vulnerabilities such as Log4Shell to obtain an initial foothold into target networks.

Also, place to buyers a cracking station that hosts cracked hashes linked with area qualifications, Kerberos tickets, and KeePass data files, amongst others.
What’s extra, the group has invested in a personalized VoIP setup wherein employed phone operators cold-simply call non-responsive victims in a bid to put further strain and compel them into shelling out up after a ransomware attack.
This is not the initial time the team has resorted to such a tactic. Final 12 months, Microsoft in-depth a BazarLoader campaign dubbed BazaCall that used phony get in touch with facilities to lure unsuspecting victims into installing ransomware on their methods.
“The group has massive figures of compromised products at its command and employs a really dispersed expert workflow to preserve security and a superior operational tempo,” the researchers claimed.
“It is accountable for an monumental quantity of spam on hundreds of hundreds of thousands of thousands and thousands of devices, as properly as concentrated facts breaches and ransomware attacks on superior-benefit targets.”
Located this short article appealing? Stick to THN on Fb, Twitter and LinkedIn to browse more exceptional content material we publish.
Some pieces of this post are sourced from:
thehackernews.com

 UK Government: Lack of Skills the Number One Issue in Cybersecurity
UK Government: Lack of Skills the Number One Issue in Cybersecurity