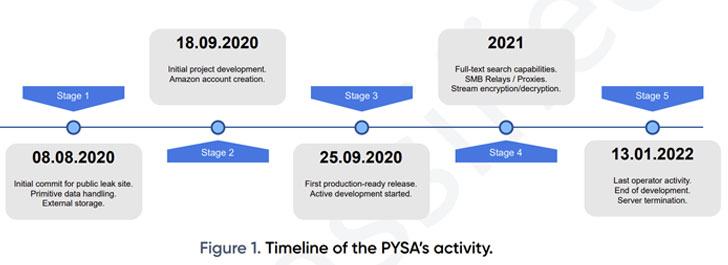
An 18-month-extensive analysis of the PYSA ransomware operation has uncovered that the cybercrime cartel adopted a five-phase computer software advancement cycle from August 2020, with the malware authors prioritizing options to improve the performance of its workflows.
This included a person-friendly device like a entire-textual content lookup motor to facilitate the extraction of metadata and empower the threat actors to come across and access victim facts immediately.
“The team is identified to carefully investigate superior-benefit targets prior to launching its attacks, compromising organization systems and forcing companies to pay out huge ransoms to restore their knowledge,” Swiss cybersecurity corporation PRODAFT said in an exhaustive report printed very last 7 days.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
PYSA, short for “Guard Your Program, Amigo” and a successor of the Mespinoza ransomware, was initial noticed in December 2019 and has emerged as the third most widespread ransomware pressure detected in the course of the fourth quarter of 2021.
Due to the fact September 2020, the cybercriminal gang is thought to have exfiltrated delicate facts belonging to as a lot of as 747 victims until finally its servers had been taken offline earlier this January.
Most of its victims are situated in the U.S. and Europe, with the group generally hanging authorities, health care, and educational sectors. “The U.S. was the most-impacted region, accounting for 59.2% of all PYSA occasions reported, followed by the U.K. at 13.1%,” Intel 471 pointed out in an investigation of ransomware attacks recorded from Oct to December 2021.
PYSA, like other ransomware families, is recognised to observe the “big video game searching” technique of double extortion, which consists of publicizing the stolen data really should a victim refuse to comply with the group’s calls for.
Each individual eligible file is encrypted and specified a “.pysa” extension, decoding which necessitates the RSA private vital that can only be acquired right after paying out the ransom. Virtually 58% of the PYSA victims are claimed to have made digital payments.
PRODAFT, which was able to identify a publicly obtainable .git folder managed by PYSA operators, identified just one of the project’s authors as “[email protected],” a menace actor who is considered to be positioned in a state that observes daylight discounts time primarily based on the commit history.
At minimum 11 accounts, a greater part of which were being created on January 8, 2021, are mentioned to be in charge of the all round procedure, the investigation has disclosed. That explained, 4 of these accounts — named t1, t3, t4, and t5 — account for above 90% of activity on the group’s administration panel.
Other operational security faults made by the group’s users also manufactured it achievable to detect a concealed service working on the TOR anonymity network — a hosting service provider (Snel.com B.V.) found in the Netherlands — featuring a glimpse into the actor’s tactics.
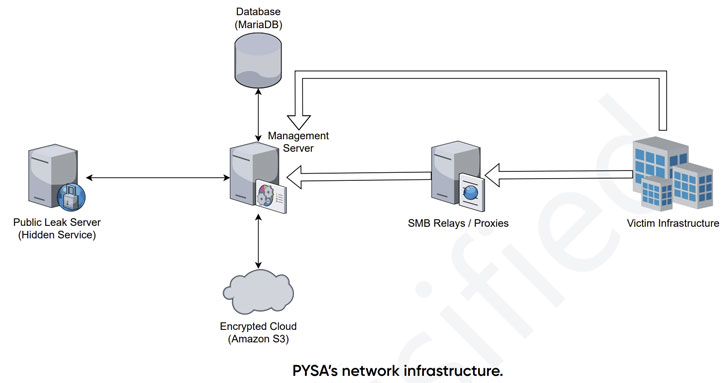
PYSA’s infrastructure also is composed of dockerized containers, such as general public leak servers, databases, and administration servers, as properly as an Amazon S3 cloud to retail outlet the encrypted information, which sum to a substantial 31.47TB.

Also set to use is a customized leak management panel to lookup private documents in the information exfiltrated from victims’ inner networks prior to encryption. Other than utilizing the Git edition regulate program to control the progress procedures, the panel itself is coded in PHP 7.3.12 utilizing the Laravel framework.
What’s much more, the administration panel exposes a assortment of API endpoints that allows the program to list files, down load documents, and review the data files for full-text look for, which is created to categorize the stolen target details into broad classes for uncomplicated retrieval.
“The team is supported by knowledgeable developers who implement modern day operational paradigms to the group’s progress cycle,” the researcher reported. “It indicates a skilled ecosystem with perfectly-organized division of obligations, alternatively than a free network of semi-autonomous danger actors.”
If something, the conclusions are however an additional indicator that ransomware gangs like PYSA and Conti function and are structured like authentic application firms, even including an HR department to recruit new hires and an “employee of the month” award for tackling challenging difficulties.
The disclosure also arrives as a report from cybersecurity company Sophos uncovered that two or extra danger actor groups invested at the very least five months within just the network of an unnamed regional U.S. federal government agency just before deploying a LockBit ransomware payload at the start off of the calendar year.
Identified this article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to go through much more unique material we article.
Some sections of this report are sourced from:
thehackernews.com



 Benchmarking Linux Security – Latest Research Findings
Benchmarking Linux Security – Latest Research Findings