Cybersecurity researchers have taken the wraps of an arranged financial-theft operation undertaken by a discreet actor to focus on transaction processing devices and siphon funds from entities mainly positioned in Latin The usa for at least 4 years.
The malicious hacking group has been codenamed Elephant Beetle by Israeli incident reaction company Sygnia, with the intrusions aimed at financial institutions and retail companies by injecting fraudulent transactions between benign action to slip beneath the radar soon after an intensive examine of the targets’ money constructions.
“The attack is relentless in its ingenious simplicity serving as an excellent tactic to cover in simple sight, without having any require to develop exploits,” the researchers stated in a report shared with The Hacker Information, calling out the group’s overlaps with a further tracked by Mandiant as FIN13, an “industrious” danger actor linked to info theft and ransomware attacks in Mexico stretching back again as early as 2016.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Elephant Beetle is reported to leverage an arsenal of no much less than 80 unique equipment and scripts to execute its attacks, even though at the same time using measures to mix in with the victim’s ecosystem around extended periods to reach its goals.
“The unique modus operandi associated with the Elephant Beetle is their deep investigation and knowledge of victim’s monetary units and operations and their persistent lookup for susceptible solutions to technically inject money transactions, finally primary to key fiscal theft,” Arie Zilberstein, vice president of incident response at Sygnia, told The Hacker News. “Specified the prolonged time period of persistence this team has in victim’s networks, they generally change and adapt their tactics and tooling to proceed to be suitable.”
Zilberstein attributed the achievement of the marketing campaign to the vast attack surface area supplied by legacy methods that are existing in money institutions’ networks and can serve as entry factors, thereby enabling attackers to acquire a everlasting foothold into concentrate on networks.
The adversary’s modus operandi follows a small-profile sample that starts with planting backdoors to analyze the victim’s atmosphere, exclusively with an aim to comprehend the many procedures used to aid monetary transactions, adopted by inserting rogue transactions of its very own into the network that steal incremental quantities of dollars from the target to avoid location off alarm.
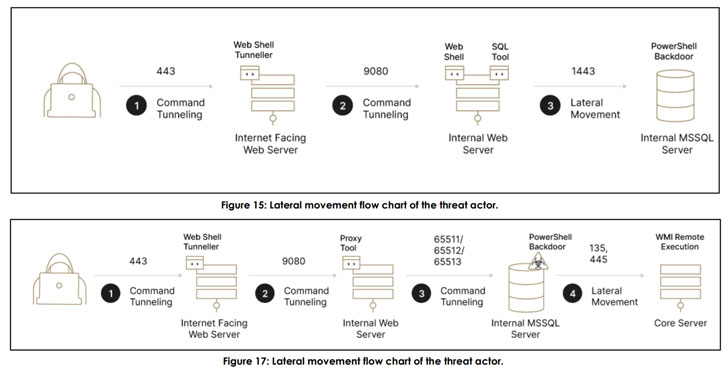
But in the occasion the actor’s fraudulent steps appear to light-weight, they briefly cease their operations only to return a number of months later. The first entry is brokered by having benefit of unpatched flaws in exterior-experiencing Java-dependent web servers these as WebSphere and WebLogic, in the long run main to the deployment of web shells that permit distant code execution and lateral motion —
- CVE-2017-1000486 (CVSS score: 9.8) – Primefaces Software Expression Language Injection
- CVE-2015-7450 (CVSS rating: 9.8) – WebSphere Software Server Cleaning soap Deserialization Exploit
- CVE-2010-5326 (CVSS score: 10.) – SAP NetWeaver Invoker Servlet Exploit
- EDB-ID-24963 – SAP NetWeaver ConfigServlet Remote Code Execution
“This attack emphasizes after yet again that complex attackers are from time to time lurking in networks for [a] prolonged time,” Zilberstein reported. “While a ton of emphasis is supplied now to steering clear of and stopping the imminent risk of ransomware, some other threat actors are continue to operating to stealthily proliferate by themselves in networks to get a lengthy time period and continuous economical obtain.”
“Corporations have to have to fork out excess notice to these techniques, specifically all those which are externally experiencing, and accomplish patching and ongoing looking to reduce and detect attacks of very similar character,” Zilberstein added.
Observed this short article intriguing? Follow THN on Facebook, Twitter and LinkedIn to read much more exceptional material we publish.
Some sections of this short article are sourced from:
thehackernews.com



 ‘Malsmoke’ Exploits Microsoft’s E-Signature Verification
‘Malsmoke’ Exploits Microsoft’s E-Signature Verification