Cybersecurity scientists have uncovered weaknesses in a software implementation of the Border Gateway Protocol (BGP) that could be weaponized to reach a denial-of-services (DoS) situation on vulnerable BGP friends.
The 3 vulnerabilities reside in version 8.4 of FRRouting, a common open source internet routing protocol suite for Linux and Unix platforms. It truly is now utilised by several vendors like NVIDIA Cumulus, DENT, and SONiC, posing source chain challenges.
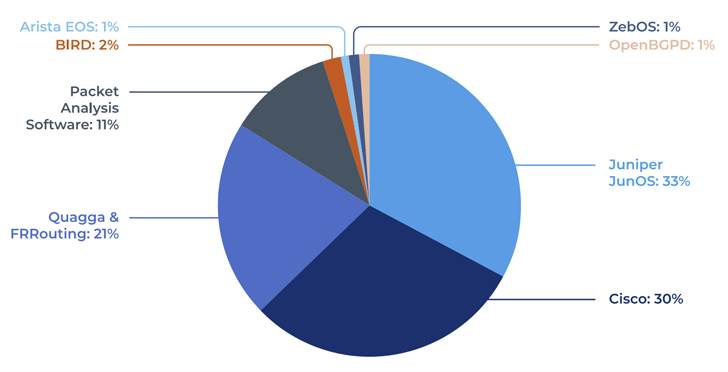
The discovery is the outcome of an examination of seven various implementations of BGP carried out by Forescout Vedere Labs: FRRouting, Chook, OpenBGPd, Mikrotik RouterOS, Juniper JunOS, Cisco IOS, and Arista EOS.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
BGP is a gateway protocol which is made to exchange routing and reachability data involving autonomous techniques. It can be utilised to discover the most efficient routes for offering internet traffic.

The checklist of three flaws is as follows –
- CVE-2022-40302 (CVSS score: 6.5) – Out-of-bounds go through when processing a malformed BGP Open information with an Prolonged Optional Parameters Length solution.
- CVE-2022-40318 (CVSS rating: 6.5) – Out-of-bounds study when processing a malformed BGP Open up message with an Prolonged Optional Parameters Duration selection.
- CVE-2022-43681 (CVSS rating: 6.5) – Out-of-bounds read through when processing a malformed BGP Open concept that abruptly ends with the possibility duration octet.
The issues “could be exploited by attackers to reach a DoS ailment on susceptible BGP peers, therefore dropping all BGP sessions and routing tables and rendering the peer unresponsive,” the corporation claimed in a report shared with The Hacker News.
“The DoS situation may possibly be extended indefinitely by continuously sending malformed packets. The key root bring about is the exact same susceptible code pattern copied into many features associated to different stages of parsing Open messages.”
A threat actor could spoof a legitimate IP handle of a trustworthy BGP peer or exploit other flaws and misconfigurations to compromise a legit peer and then issue a specially-crafted unsolicited BGP Open up concept.
This is reached by using benefit of the simple fact that “FRRouting commences to course of action Open up messages (e.g., decapsulating optional parameters) ahead of it gets a probability to verify the BGP Identifier and ASN fields of the originating router.”
Upcoming WEBINARLearn to Cease Ransomware with Genuine-Time Security
Join our webinar and learn how to end ransomware attacks in their tracks with genuine-time MFA and services account defense.
Preserve My Seat!
Forescout has also built out there an open up source instrument identified as bgp_boofuzzer that allows corporations to examination the security of the BGP suites made use of internally as very well as obtain new flaws in BGP implementations.
“Present day BGP implementations still have reduced-hanging fruits that can be abused by attackers,” Forescout mentioned. “To mitigate the risk of susceptible BGP implementations, […] the very best recommendation is to patch network infrastructure products as typically as doable.”
The results arrive months just after ESET observed that secondhand routers earlier utilised in enterprise networking environments harbored sensitive knowledge, which includes company qualifications, VPN facts, cryptographic keys, and other crucial shopper info.
“In the incorrect fingers, the information gleaned from the devices – together with buyer facts, router-to-router authentication keys, application lists, and much far more – is more than enough to launch a cyberattack,” the Slovak cybersecurity firm said.
Discovered this post fascinating? Stick to us on Twitter and LinkedIn to go through far more special information we publish.
Some areas of this short article are sourced from:
thehackernews.com

 BouldSpy Android Spyware: Iranian Government’s Alleged Tool for Spying on Minority Groups
BouldSpy Android Spyware: Iranian Government’s Alleged Tool for Spying on Minority Groups