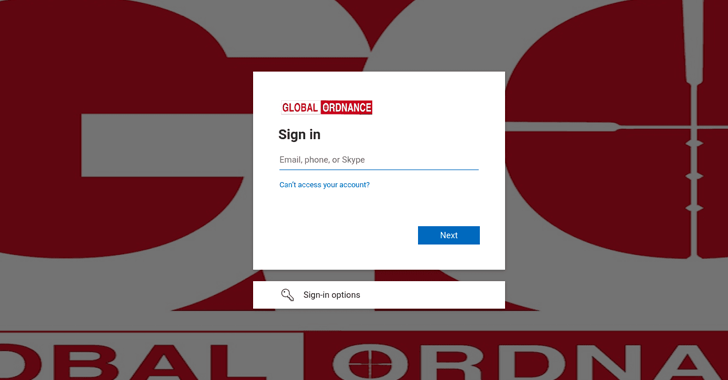
A state-sponsored hacking team with one-way links to Russia has been connected to attack infrastructure that spoofs the Microsoft login web page of Global Ordnance, a respectable U.S.-based mostly armed forces weapons and components provider.
Recorded Future attributed the new infrastructure to a menace exercise team it tracks below the title TAG-53, and is broadly recognized by the cybersecurity group as Callisto, COLDRIVER, SEABORGIUM, and TA446.
“Based mostly on historical community reporting on overlapping TAG-53 strategies, it is probable that this credential harvesting exercise is enabled in aspect by phishing,” Recorded Future’s Insikt Team stated in a report printed this 7 days.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The cybersecurity organization mentioned it found 38 domains, 9 of which contained references to businesses like UMO Poland, Sangrail LTD, DTGruelle, Blue Sky Network, the Fee for Intercontinental Justice and Accountability (CIJA), and the Russian Ministry of Internal Affairs.
It is suspected that the themed domains are most likely an try on portion of the adversary to masquerade as authentic parties in social engineering campaigns.

“Notably, a steady pattern has emerged relating to the use of specially customized infrastructure by TAG-53 highlighting the extended-phrase use of equivalent strategies for their strategic campaigns,” the scientists claimed.
The growth comes virtually four months right after Microsoft disclosed that it took ways to disrupt phishing and credential theft attacks mounted by the team with the objective of breaching defense and intelligence consulting businesses as very well as NGOs, imagine tanks, and bigger education and learning entities in the U.K. and the U.S.
Business security enterprise Proofpoint has even more termed out the group for its subtle impersonation ways to supply rogue phishing backlinks.
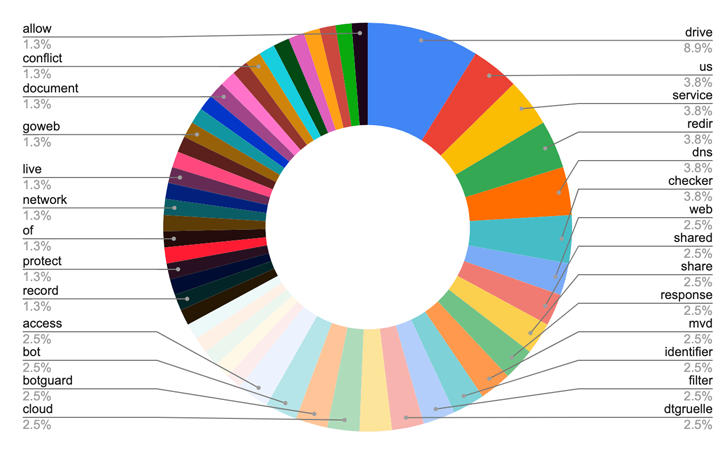 Conditions made use of in TAG-53 connected domains
Conditions made use of in TAG-53 connected domains
In addition, the danger actor has been attributed with low self-confidence to a spear-phishing operation concentrating on Ukraine’s Ministry of Defence coinciding with the onset of Russia’s armed service invasion of the country previously this March.
SEKOIA.IO, in a independent write-up, corroborated the conclusions, uncovering a whole of 87 domains, with two of them alluding to private sector firms Emcompass and BotGuard. Also focused were four NGOs associated in Ukraine crisis reduction.
1 of individuals attacks concerned email communications amongst the NGO and the attacker using a spoofed email address mimicking a reliable supply, adopted by sending a malicious PDF that contains a phishing connection in an try to evade detection from email gateways.
“The email trade reveals that the attacker did not include the destructive payload in the first email, but waited to get an remedy to construct a connection and stay clear of suspicion ahead of sending the payload to the target,” the cybersecurity organization described.
The use of typosquatted Russian ministry domains even further provides bodyweight to Microsoft’s assessment that SEABORGIUM targets former intelligence officers, professionals in Russian affairs, and Russian citizens overseas.
SEKOIA.IO also characterised the concentrating on of CIJA as an intelligence collecting mission built to amass “war crime-connected proof and/or global justice procedures, most likely to foresee and establish counter narrative on long term accusations.”
The disclosures arrive as risk intelligence company Lupovis unveiled that Russian menace actors have compromised the networks belonging to several providers in the U.K., the U.S., France, Brazil, South Africa, and are “rerouting by means of their networks” to launch attacks in opposition to Ukraine.
Microsoft, in the in the meantime, has warned of “potential Russian attack in the digital domain more than the program of this wintertime,” pointing out Moscow’s “multi-pronged hybrid technology technique” of conducting cyber strikes in opposition to civilian infrastructure and impact functions trying to get to fuel discord in Europe.
Uncovered this posting intriguing? Stick to us on Twitter and LinkedIn to read through more unique content material we post.
Some pieces of this write-up are sourced from:
thehackernews.com

 ICO Fines Rogue Nuisance Callers £500,000
ICO Fines Rogue Nuisance Callers £500,000