A now-patched security flaw has been disclosed in the Galaxy Keep application for Samsung gadgets that could probably result in distant command execution on impacted phones.
The vulnerability, which impacts Galaxy Keep version 4.5.32.4, relates to a cross-site scripting (XSS) bug that happens when managing specified deep links. An unbiased security researcher has been credited with reporting the issue.
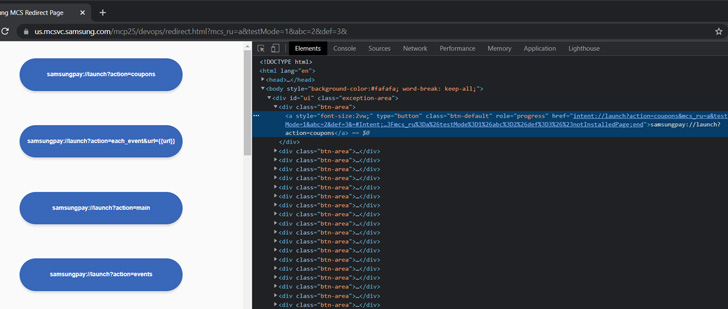
“Here, by not checking the deep website link securely, when a person accesses a connection from a internet site made up of the deeplink, the attacker can execute JS code in the webview context of the Galaxy Retail outlet application,” SSD Protected Disclosure claimed in an advisory posted past week.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
XSS attacks allow for an adversary to inject and execute malicious JavaScript code when visiting a website from a browser or a further software.

The issue identified in the Galaxy Keep application has to do with how deep backlinks are configured for Samsung’s Promoting & Material Support (MCS), probably major to a situation the place arbitrary code injected into the MCS site could direct to its execution.
This could then be leveraged to down load and set up malware-laced applications on the Samsung unit when checking out the hyperlink.
“To be in a position to effectively exploit the victim’s server, it is required to have HTTPS and CORS bypass of chrome,” the scientists noted.
Uncovered this post exciting? Abide by THN on Facebook, Twitter and LinkedIn to study extra distinctive content we article.
Some elements of this post are sourced from:
thehackernews.com


 Russia Suspected in Truss Phone Hacking Scandal
Russia Suspected in Truss Phone Hacking Scandal