The danger actor powering a nascent Android banking trojan named SharkBot has managed to evade Google Participate in Retail store security limitations by masquerading as an antivirus app.
SharkBot, like its malware counterparts TeaBot, FluBot, and Oscorp (UBEL), belongs to a category of economic trojans capable of siphoning credentials to initiate dollars transfers from compromised devices by circumventing multi-factor authentication mechanisms. It initial emerged on the scene in November 2021.
Where by SharkBot stands aside is in its capacity to have out the unauthorized transactions via Computerized Transfer Units (ATS), which stands in distinction to TeaBot, which requires a live operator to interact with the contaminated gadgets to conduct the destructive routines.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
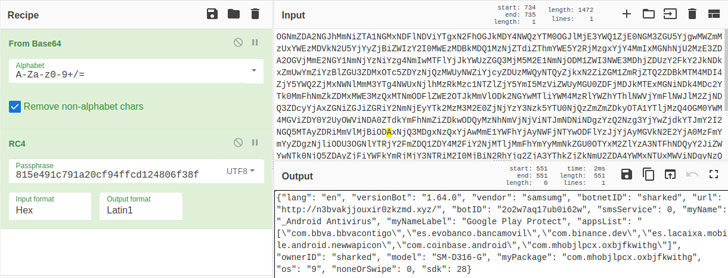
“The ATS options let the malware to receive a record of activities to be simulated, and they will be simulated in get to do the revenue transfers,” Alberto Segura and Rolf Govers, malware analysts at cybersecurity agency NCC Group, said in a report released very last 7 days.
“Because these characteristics can be used to simulate touches/clicks and button presses, it can be applied to not only automatically transfer revenue but also put in other destructive purposes or elements.”
In other text, ATS is utilized to deceive the qualified bank’s fraud detection units by simulating the exact sequence of actions that would be done by the person, these kinds of as button presses, clicks, and gestures, in get to make the illicit revenue transfer.
The most current variation spotted on the Google Play Retail outlet on February 28 are a selection of dropper apps that also leverages Android’s Direct Reply operation to propagate alone to other units, producing it the 2nd banking trojan following FluBot to intercept notifications for wormable attacks.
The listing of destructive apps, all of which were being current on February 10, have been collectively mounted about 57,000 situations to date –
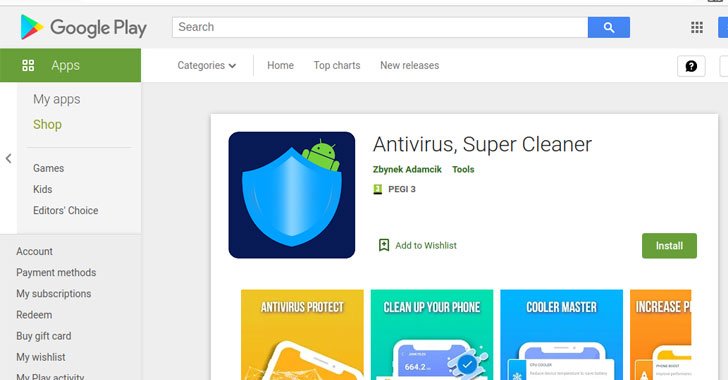
- Antivirus, Tremendous Cleaner (com.abbondioendrizzi.antivirus.supercleaner) – 1,000+ installs
- Atom Cleanse-Booster, Antivirus (com.abbondioendrizzi.applications.supercleaner) – 500+ installs
- Alpha Antivirus, Cleaner (com.pagnotto28.sellsourcecode.alpha) – 5,000+ installs, and
- Impressive Cleaner, Antivirus (com.pagnotto28.sellsourcecode.supercleaner) – 50,000+ installs
SharkBot is also aspect-loaded in that it allows the adversary to inject fraudulent overlays atop official banking applications to steal qualifications, log keystrokes, and attain entire distant handle more than the devices, but only after the victims grant it Accessibility Companies permissions.
The results arrive a 7 days following researchers from Cleafy disclosed details of a new TeaBot variant uncovered in the Play Retail outlet which is designed to target end users of more than 400 banking and economical applications, which includes those from Russia, China, and the U.S.
Observed this short article appealing? Stick to THN on Facebook, Twitter and LinkedIn to examine much more special information we article.
Some pieces of this article are sourced from:
thehackernews.com



 2 New Mozilla Firefox 0-Day Bugs Under Active Attack — Patch Your Browser ASAP!
2 New Mozilla Firefox 0-Day Bugs Under Active Attack — Patch Your Browser ASAP!