The major award for flaws that allow for cybercriminals to abuse legit companies has amplified by 166 p.c.
Google is escalating the reward quantities in its bug-bounty plan for studies concentrating on probable assaults in the product or service-abuse place, to major out at $13,337 per report.
Merchandise abuse is when a danger actor employs a genuine assistance in a way that enables social-engineering or other cyberattacks. For occasion, last year a marketing campaign created the rounds that took edge of a prevalent default aspect for persons employing Gmail on their smartphones: Calendar invitations immediately pop up on telephones, prompting end users to take or drop them. Cybercriminals ended up sending targets an unsolicited calendar invitation carrying a connection to a phishing URL.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In yet another instance, researcher Martin Vigo learned that it was attainable to be a part of a Google Satisfies enterprise assembly by phone, if just one understood the phone selection and a 4-digit PIN for the meeting these ended up discoverable by uncomplicated “wardialing” and brute-forcing, among the other tactics. Also, he discovered that recurring meetings have static quantities and PINs, presenting former workforce a simple attack vector.
“The nature of product or service abuse is constantly altering,” wrote Google’s Marc Henson, guide and software manager for Have faith in & Basic safety, and Anna Hupa, senior strategist, in a weblog this week. “Why? The technology (merchandise and security) is modifying, the actors are altering and the field is growing. Within this dynamic ecosystem, we are specially fascinated in study that guards users’ privacy, guarantees the integrity of our systems, as nicely as stops economic fraud or other harms at scale.”
The highest reward in the solution-abuse software has now improved by 166 per cent, from $5,000 to $13,337. Investigate with medium- to large-effect and likelihood will now generate up to $5,000. A full breakdown of the benefits is below:
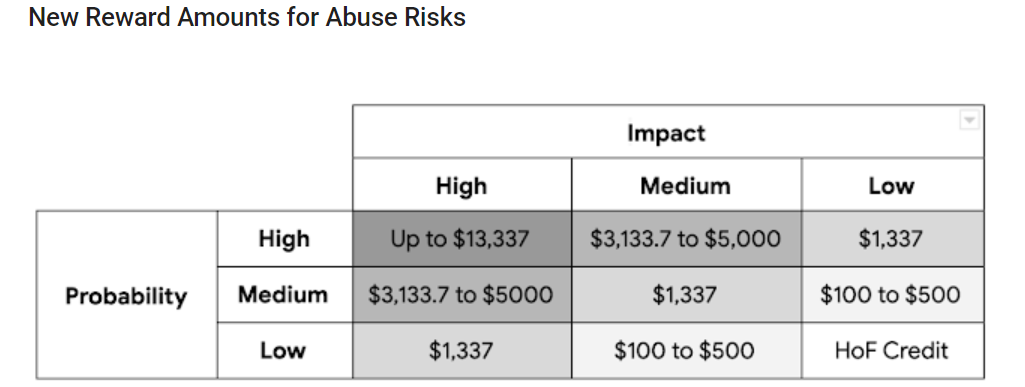
“Reports that qualify for a reward are all those that will consequence in variations to the product code, as opposed to removing of person parts of abusive information,” included Henson and Hupa. “The ultimate reward total for a specified abuse risk report also remains at the discretion of the reward panel. When evaluating the affect of an abuse risk, the panels glimpse at both equally the severity of the issue as well as the variety of impacted customers.”
They added that the increased reward ranges will before long be followed by an enlargement in Google’s Vulnerability Exploration Grants, to assist cyber-investigate into avoiding abuse risks.
The internet big has so much identified more than 750 beforehand not known products abuse pitfalls by way of the system, they explained.
Google has continuously expanded its bug-bounty plans. Final year for occasion it debuted the Developer Info Defense Reward Plan, which provides up to $50,000 for stories on violations of the Google Play, Google API and Google Chrome Web Retail store Extension software privateness guidelines.
Also in 2019, Google tripled best reward payouts for security flaws in Chrome from $5,000 to $15,000 – and doubled the most reward total for high-excellent stories from $15,000 to $30,000.
The Android Security Rewards program meanwhile has included extra exploit types, and upped the leading prize to $1 million for a complete-chain, remote-code-execution exploit with persistence that compromises the Titan M secure element on Pixel products.
This year marks the tenth anniversary of Google beginning its bug-bounty attempts in January, it claimed that it experienced paid out out $21 million in rewards to date and $6.5 million final year on your own.
On Wed Sept. 16 @ 2 PM ET: Learn the strategies to operating a profitable Bug Bounty Software. Register today for this FREE Threatpost webinar “Five Essentials for Working a Productive Bug Bounty Program“. Hear from top Bug Bounty System experts how to juggle community vs . non-public systems and how to navigate the tough terrain of handling Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.


 Python-dependent Spy RAT Emerges to Concentrate on FinTech
Python-dependent Spy RAT Emerges to Concentrate on FinTech