Soon after backlash above false marketing about its encryption policies, Zoom will at last roll out close-to-end encryption upcoming 7 days.
Movie-conferencing huge Zoom is rolling out a complex preview of its close-to-close encryption (E2EE) next 7 days.
Zoom has confronted numerous controversies all over its encryption insurance policies in excess of the earlier calendar year, including several lawsuits alleging that the business falsely informed people that it gives total encryption. Then, the platform came underneath fire in May well when it introduced that it would certainly provide E2EE — but to compensated end users only. The corporation afterwards backtracked just after backlash from privacy advocates, who argued that security actions must be readily available to all. Zoom will now offer you the function to absolutely free/”Basic” consumers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The 1st period of the E2EE rollout aims to solicit suggestions when it comes to its policies. Buyers will be able to weigh in throughout the initial 30 days. Of notice, consumers will require to switch on the feature manually (see down below for specifics).

“We’re pleased to roll out Period 1 of 4 of our E2EE giving, which offers strong protections to support avoid the interception of decryption keys that could be utilized to keep track of assembly material,” claimed Max Krohn, head of security engineering with Zoom, in a Wednesday publish.
Conclusion-To-End Encryption Problems
The subject of encryption is critical for Zoom as it ramps up its security and privacy steps – notably right after a variety of security flaws and privacy issues exposed weaknesses in the on the internet meeting platform, as its person base spiked for the duration of the coronavirus pandemic.
Zoom previously said that it supplied E2EE, but that marketing assert arrived into question soon after a March report from The Intercept said that Zoom’s system actually works by using transportation layer security (TLS) encryption, offering only encryption between particular person customers and provider companies, in its place of right between the consumers of a procedure.
Though “encryption” suggests that in-transit messages are encrypted, accurate E2EE occurs when the concept is encrypted at the resource user’s system, stays encrypted when its routed through servers, and then is decrypted only at the location user’s system.
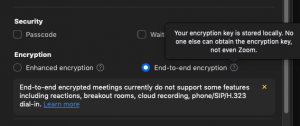
Zoom end-to-finish encryption enablement in settings. Credit history: Zoom
On the heels of this backlash, Zoom in May perhaps obtained a smaller startup named Keybase, with the goal of providing much more sturdy encryption for Zoom calls.
In the scenario of next week’s rollout, Zoom’s E2EE providing will use public-vital cryptography, meaning that the keys for just about every Zoom assembly are created by participants’ machines (as opposed to Zoom’s servers).
“While this is continue to restricted throughout the capabilities it’s enabled for, it represents a major action in the right route with regards to ensuring user security and privacy on the platform,” Jack Mannino, CEO at nVisium, instructed Threatpost. “Distributing keys to the purchasers and decentralizing believe in gives end users increased assurance that their communications are less probably to be intercepted by means of compromised keys or infrastructure.”
In accordance to Krohn, “Encrypted data relayed as a result of Zoom’s servers is indecipherable by Zoom, since Zoom’s servers do not have the vital decryption vital. This crucial administration technique is very similar to that utilised by most finish-to-close encrypted messaging platforms these days.”
Following Week’s Rollout
Zoom hosts can empower E2EE at the account, team or user stage in their configurations. Zoom mentioned that in phase 1 of its rollout, all assembly contributors should be part of from the Zoom desktop customer, cellular app or Zoom Rooms. In buy to see that E2EE is enabled, participants can seem for a inexperienced protect logo in the higher remaining corner of their assembly display screen with a padlock in the middle.
Enabling the attribute may possibly disable specified other capabilities, this kind of as “join just before host,” cloud recording, streaming, live transcription, Breakout Rooms, polling, 1:1 non-public chat and conference reactions, claimed Zoom.
“Zoom’s major priority is the rely on and protection of our end users, and our implementation of E2EE will enable us to proceed to greatly enhance basic safety on our platform,” explained Zoom. “Free/Standard users in search of obtain to E2EE will take part in a a person-time verification process that will prompt the person for added parts of info, such as verifying a phone quantity via textual content message.”
Zoom said the 2nd phase of the rollout, which will include things like superior id management and E2EE single sign-on (SSO) integration, is roadmapped for 2021.
Some parts of this post are sourced from:
threatpost.com


 Broadvoice Leak Exposes 350M Records, Personal Voicemail Transcripts
Broadvoice Leak Exposes 350M Records, Personal Voicemail Transcripts