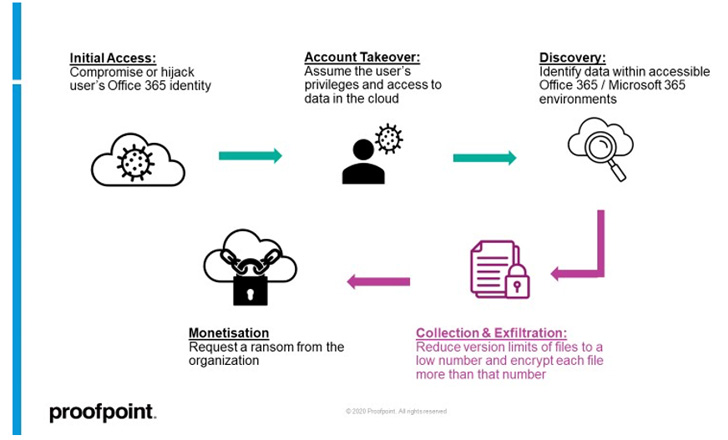
A “hazardous piece of performance” has been found out in Microsoft 365 suite that could be perhaps abused by a malicious actor to ransom information stored on SharePoint and OneDrive and launch attacks on cloud infrastructure.
The cloud ransomware attack can make it attainable to launch file-encrypting malware to “encrypt documents stored on SharePoint and OneDrive in a way that tends to make them unrecoverable without the need of devoted backups or a decryption essential from the attacker,” Proofpoint reported in a report posted these days.
The infection sequence can be carried out utilizing a blend of Microsoft APIs, command-line interface (CLI) scripts, and PowerShell scripts, the enterprise security company included.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The attack, at its main, hinges on a Microsoft 365 characteristic referred to as AutoSave that results in copies of more mature file versions as and when customers make edits to a file saved on OneDrive or SharePoint On-line.

It commences with getting unauthorized obtain to a goal user’s SharePoint On line or OneDrive account, followed by abusing the entry to exfiltrate and encrypt data files. The a few most typical avenues to get hold of the initial foothold contain right breaching the account through phishing or brute-force attacks, tricking a consumer into authorizing a rogue 3rd-party OAuth software, or using in excess of the web session of a logged-in person.
But exactly where this attack stands aside from traditional endpoint ransomware action is that the encryption section calls for locking just about every file on SharePoint On the internet or OneDrive a lot more than the permitted versioning limit.
Microsoft elaborates the versioning actions in its documentation as follows –
Some businesses make it possible for limitless versions of data files and many others use constraints. You could possibly uncover, just after checking in the most up-to-date edition of a file, that an aged variation is missing. If your most modern version is 101. and you see that there is no lengthier a model 1., it implies that the administrator configured the library to permit only 100 major variations of a file. The addition of the 101st model triggers the initially model to be deleted. Only versions 2. by means of 101. continue to be. Similarly, if a 102nd model is included, only versions 3. by means of 102. stay.
By leveraging the access to the account, an attacker can possibly generate also several variations of a file or alternatively cut down the variation limit of a document library to a reduced these as “1” and then move forward to encrypt each individual file 2 times.

“Now all original (pre-attacker) variations of the data files are lost, leaving only the encrypted variations of every file in the cloud account,” the scientists explained. “At this position, the attacker can check with for a ransom from the firm.”
Microsoft, in reaction to the findings, pointed out that older variations of data files can be potentially recovered and restored for an more 14 days with the help of Microsoft Assist, a procedure that Proofpoint located to be unsuccessful.
We have achieved out to the tech large for even more comment, and we will update the story if we hear back again.
To mitigate these attacks, it can be proposed to enforce a powerful password policy, mandate multi-factor authentication (MFA), and stop massive-scale facts downloads to unmanaged products.
“Data files stored in a hybrid point out on both of those endpoint and cloud these as by way of cloud sync folders will decrease the influence of this novel risk as the attacker will not have entry to the community/endpoint information,” the researchers reported. “To carry out a complete ransom movement, the attacker will have to compromise the endpoint and the cloud account to entry the endpoint and cloud-saved information.”
Discovered this posting interesting? Adhere to THN on Facebook, Twitter and LinkedIn to read through extra exceptional content material we submit.
Some areas of this article are sourced from:
thehackernews.com


 Difference Between Agent-Based and Network-Based Internal Vulnerability Scanning
Difference Between Agent-Based and Network-Based Internal Vulnerability Scanning