Microsoft is warning that the BlackCat ransomware crew is leveraging exploits for unpatched Exchange server vulnerabilities to acquire accessibility to focused networks.
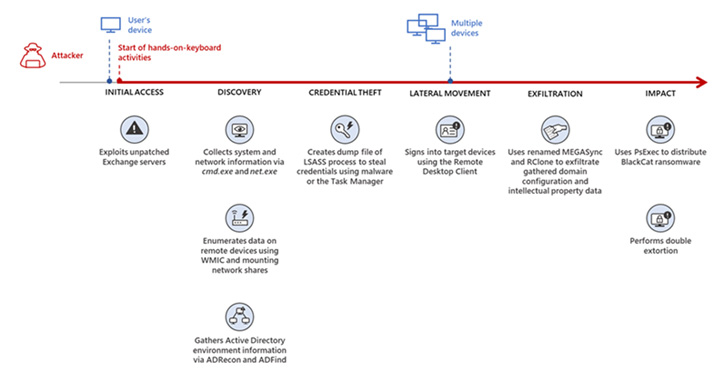
On getting an entry level, the attackers quickly moved to gather data about the compromised devices, adopted by carrying out credential theft and lateral movement routines, just before harvesting intellectual residence and dropping the ransomware payload.
The full sequence of situations performed out more than the class of two total months, the Microsoft 365 Defender Threat Intelligence Team reported in a report posted this 7 days.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“In one more incident we noticed, we observed that a ransomware affiliate acquired original obtain to the setting via an internet-struggling with Remote Desktop server utilizing compromised credentials to indication in,” the scientists stated, pointing out how “no two BlackCat ‘lives’ or deployments could possibly search the very same.”

BlackCat, also identified by the names ALPHV and Noberus, is a relatively new entrant to the hyperactive ransomware space. It really is also recognised to be one of the very first cross-system ransomware written in Rust, exemplifying a trend where by risk actors are switching to uncommon programming languages in an endeavor to evade detection.
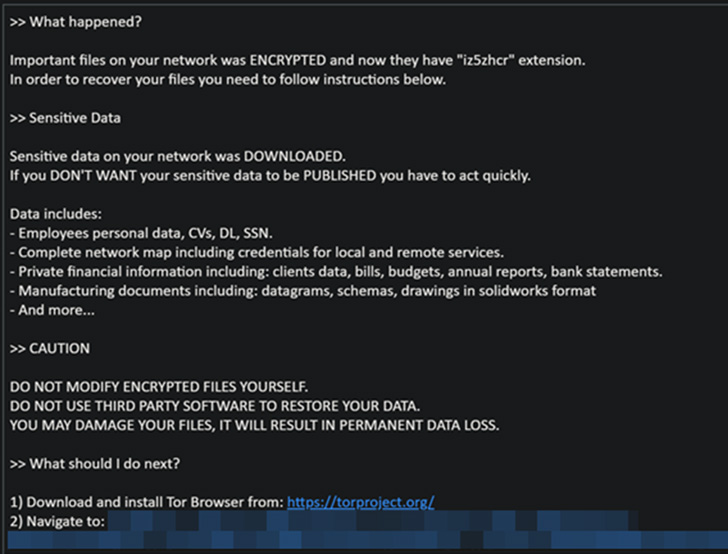
The ransomware-as-a-assistance (RaaS) scheme, irrespective of the various original entry vectors utilized, culminates in the exfiltration and encryption of target info which is then held ransom as part of what’s known as double extortion.
The RaaS design has established to be a rewarding gig financial state-model cybercriminal ecosystem consisting of a few distinctive critical gamers: obtain brokers (IABs), who compromise networks and maintain persistence operators, who create and preserve the ransomware operations and affiliates, who obtain the access from IABs to deploy the actual payload.
According to an alert produced by the U.S. Federal Bureau of Investigation (FBI), BlackCat ransomware attacks have victimized at least 60 entities around the globe as of March 2022 considering that it was 1st noticed in November 2021.
Furthermore, Microsoft explained that “two of the most prolific” affiliate danger teams, which have been connected with numerous ransomware family members such as Hive, Conti, REvil, and LockBit 2., are now distributing BlackCat.

This involves DEV-0237 (aka FIN12), a fiscally enthusiastic risk actor that was very last viewed concentrating on the health care sector in Oct 2021, and DEV-0504, which has been energetic since 2020 and has a sample of shifting payloads when a RaaS plan shuts down.
“DEV-0504 was responsible for deploying BlackCat ransomware in providers in the electrical power sector in January 2022,” Microsoft famous very last thirty day period. “All-around the similar time, DEV-0504 also deployed BlackCat in attacks from organizations in the fashion, tobacco, IT, and manufacturing industries, among other individuals.”
Identified this short article fascinating? Follow THN on Fb, Twitter and LinkedIn to go through a lot more unique articles we post.
Some components of this post are sourced from:
thehackernews.com


 A Microsoft Office 365 Feature Could Help Ransomware Hackers Hold Cloud Files Hostage
A Microsoft Office 365 Feature Could Help Ransomware Hackers Hold Cloud Files Hostage